June 7, 2021 by Siobhan Climer and Mishaal Khan
This article was originally published in March of 2020.
Last year the world dealt with the global coronavirus pandemic. Health officials across the globe recommended social distancing and quarantining and greater attention toward basic hygienic practices. To facilitate the former, thousands of businesses embraced – wherever possible – remote work environments. Now that we are coming out the other side of this, hybrid models seem to be gaining traction.
Remote work increased 140% between 2005 and 2019.

In September 2019, we reported that more than 25% of Americans work remotely part of the time. The outbreak of Covid-19 prompted many employers to shift to a remote work environment to limit the spread of the virus, and the number of U.S. workers that engaged in a work-at-home or remote work role has grew tremendously as a result.
While there are many benefits to remote work, including greater productivity, lower operating costs, improved recruitment, and reduced carbon emissions, there are also numerous challenges.
One challenge companies face when moving to a remote work environment? Cybersecurity.

The Why: Remote Work Increases Cybersecurity Risk
Remote work without the added complexity of a global pandemic can increase cybersecurity risk – all on its own. With employees dispersed over multiple locations using unknown devices to send and receive sensitive data, the risk to the company grows immensely.
The Risk Increases With Crisis
From the now prolific Covid-19 Map Malware to scammers in the Midwest going door-to-door with fake “at-home Covid-19 testing kits”, criminals were quick to latch on to the coronavirus outbreak.
Figure 1: Recent News And Headlines Around Covid-19 Scams
As Flavius Plesu, founder and CEO of human risk intelligence firm OutThink told ZDNet,
“At times of crisis, hackers see opportunity.”
In one heartbreaking case, cybercriminals attacked a Covid-19 test and treatment hospital in the Czech Republic, forcing the hospital to shut down its entire network, reroute acute patients to a different hospital, and even postpone urgent surgeries.
Cybercriminals are expert social engineers who use fear and uncertainty to bait and attack unknowing victims. An event that impacts the globe, as in the case of Covid-19, provides an incredible opportunity for these criminals.

The Challenge: Cybersecurity In A Remote Work Environment
As we alluded to earlier, there are numerous challenges in a remote work environment. From an IT perspective, the encompassing perimeter security layer is erased, leaving the internal network and everything it houses at increased risk.
In fact, a recent OpenVPN study reported that 90% of IT professionals believe remote workers are not secure.
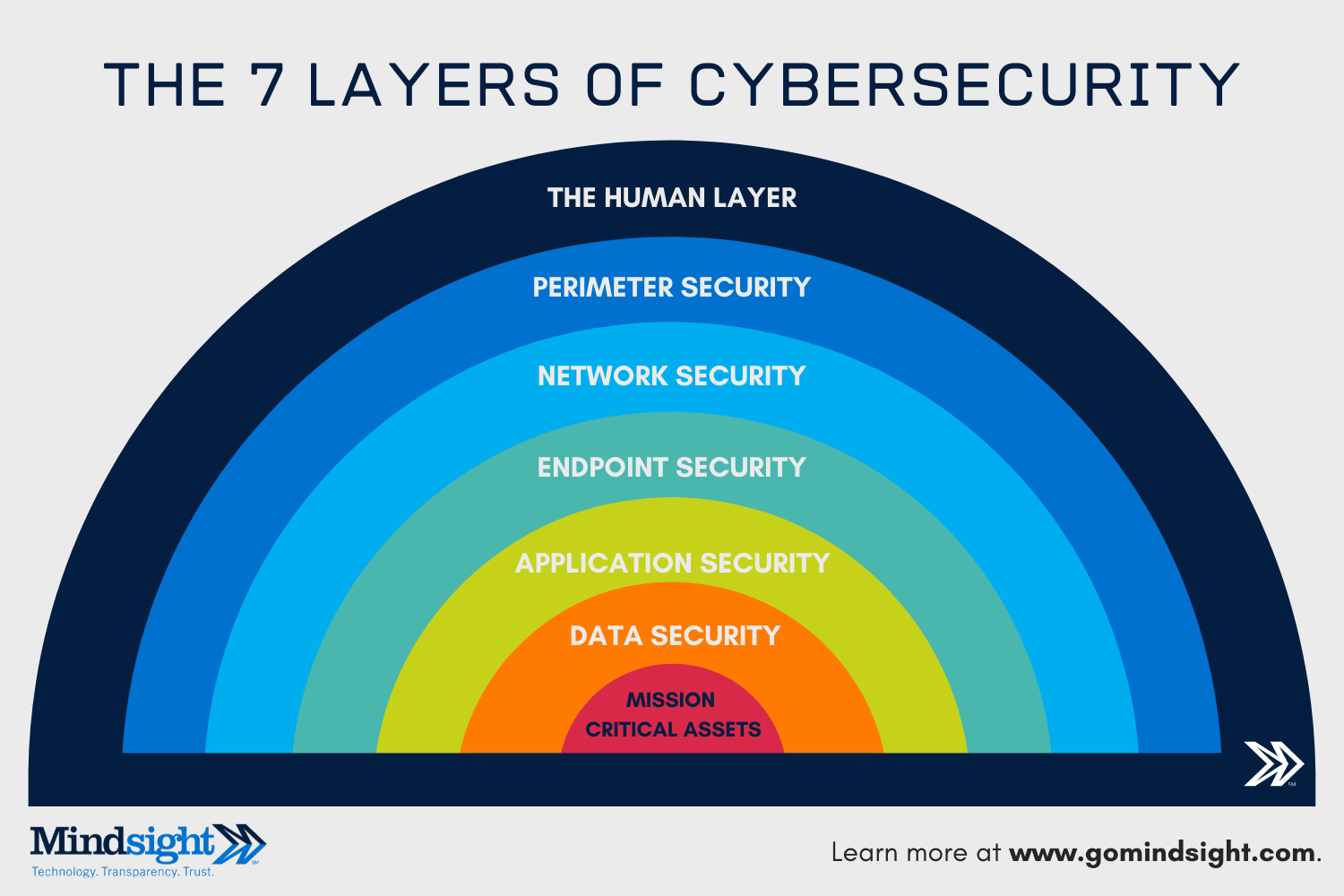
The 7 Layers Of Cybersecurity: What Happens If The Perimeter Is Gone?
With the perimeter layer absent, humans – both malicious outsiders and negligent insiders – have near-direct access to the interior security layers. For some enterprise organizations, they may have already taken steps to embrace edge computing; however, for many this security layer is instrumental in protecting mission-critical assets.
The How: Tackle Cybersecurity In A Hybrid Work Environment
With the need to move employees to a hybrid work environment, businesses are forced to take on this added cybersecurity risk.
So, how can they make this necessary change securely – and fast?

Step 1: Get Strategic About Resources
Resources are going to be limited. Whether its VPN access, bandwidth, extra monitors, or the IT department’s time and people, a swift shift to a remote work environment is going to strain the team.
Determine what a minimally viable remote work environment requires and procure those resources first.
Step 2: Cover The Basics …
Anti-virus software, secure Wi-Fi, employee training – make sure the fundamentals are covered so employees are secure in their environments.
Make sure employees know to lock their computer screens if working in shared spaces (even if that’s at home).
 Step 3: … And Write Them Down
Step 3: … And Write Them Down
Ensure every employee has received (and read) your Work-at-Home or Hybrid Work Security Policy. Don’t have one? Make one. Even hardened cybersecurity experts click on phishing emails and fail to backup data. Start developing a cybersecurity culture at all levels.
Step 4: Secure The Network – Wherever
If you do not already have a VPN, get it now. An extended remote work environment means most employees will need to access network assets at some point. Ensure they do so securely with a VPN.
Step 5: MFA, Email Security, Content Filtering – And More
 Now’s the time to harden your security controls. As Ira Winkler, President of Secure Mentem says, “It’s a ridiculous business decision to rely on the discretion of a minimally trained user to thwart a highly skilled sociopath, financially motivated criminal, or nation-state.”
Now’s the time to harden your security controls. As Ira Winkler, President of Secure Mentem says, “It’s a ridiculous business decision to rely on the discretion of a minimally trained user to thwart a highly skilled sociopath, financially motivated criminal, or nation-state.”
Don’t put the onus of cybersecurity on your employees. This is the time to assess, test, and harden your security posture to reduce overall risk in a remote work environment.
Step 6: Get Help
With strained resources and a seemingly constant in-flux state, you might need help. Mindsight feels it is our duty at this time to assist not only our loyal customers, but anyone in need of assistance in implementing remote work technology, structure, and security policies.
We’re here to help. Reach out today to start the conversation around how you can improve cybersecurity in a remote work environment.
Like what you read?
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Senior Security Solutions Architect, has been breaking – and thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Mishaal offers insight into the often murky world of cybersecurity. Mishaal brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, governments, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer writes about technology trends in education, healthcare, and business. With over a decade of experience communicating complex concepts around everything from cybersecurity to neuroscience, Siobhan is an expert at breaking down technical and scientific principles so that everyone takes away valuable insights. When she’s not writing tech, she’s reading and writing fantasy, hiking, and exploring the world with her twin daughters. Find her on twitter @techtalksio.

 Step 3: … And Write Them Down
Step 3: … And Write Them Down