March 16, 2021 by Kim Morgan
Let’s review 2020 really fast: global pandemic that caused more people than ever working from home, Tiger King, sour dough bread, and tie dye. Now time for the pop quiz: which phenomenon from 2020 exponentially increased every company’s cyber attack surface? If you answered “people working from home”, you’re correct!

Here we are, almost exactly a year since the first round of stay-at-home orders were issued, yet the security landscape looks scarier than ever, even though more security measures have been installed since last March. Companies big and small share a common enemy when it comes to data breaches, and that’s employee negligence. Not surprisingly, the evolution of cybercrime in recent years shows attacks consistently rely on the human factor to succeed.
Where is the disconnect? Companies are taking the time to buy products and services related to cybersecurity but are not creating a cybersecurity culture. Most frequently, cybercriminals will perform attacks on an organization using phishing emails and similar tactics, making employees at all levels the first line of defense that needs to be strengthened. After all, computers and apps aren’t clicking on phishing emails, humans are — so that’s where cybersecurity investments need to be focused. Employees are also the ones with everyday access to many of the organization’s computers, networks, and systems, which means they play an important part in building resilience in the threat landscape.
What is Cybersecurity Culture?
Cybersecurity culture in the workplace is more than creating and adopting policies in a vacuum without proper explanation or forcing knowledge workers to frequently update their not-so-strong passwords. Employees aren’t putting their organizations at risk out of malice, they merely need training and guidance to avoid different types of cybercrime that could harm the business.
When discussing awareness and culture, the best methods for promoting cybersecurity awareness internally seem to include interesting, relevant, and engaging programs. C levels need to promote these programs, as well.
Companies need to spend more time explaining and raising awareness with their employees about possible cyber risks and their implications and enforcing safe cybersecurity procedures that will assimilate easily with their daily work routines and practices. Show employees how their behavior can help or hinder the entire organization’s structure, from their solutions and products to third-party vendors.
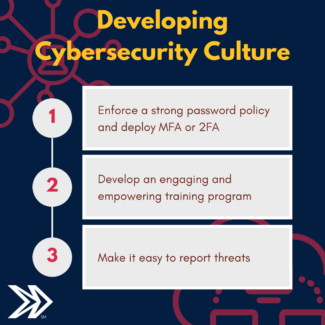
How to Establish a Cybersecurity Culture
Start with the basics: enforce a strong password policy and deploy multi-factor authentication (MFA) or two-factor authentication (2FA).
Passwords
Making passwords more difficult for an attacking algorithm to guess or steal is one of the best ways to ensure cyber safety. But let’s be honest, when asked to change a password, how many employees just change the number at the end of their first pet’s name? Cyber criminals will soon catch on that if “albusdumbledog1” worked last year, there’s a strong possibility that “albusdumbledog2” will work this year.
Longer passwords, or passphrases, with a mix of alphabetic, numeric, and special characters and without dictionary words embedded within them can render brute-force attacks worthless – especially when the organization implements an automatic lockout protocol for repeated login failures.
MFA or 2FA
Multi-factor authentication (MFA) is an authentication method that grants access to system users when presented with two or more factors – or pieces of evidence – to an authentication mechanism. Factor types include knowledge, possession, and inherence; in practice, these factors include something you know, something you have, and something you are.
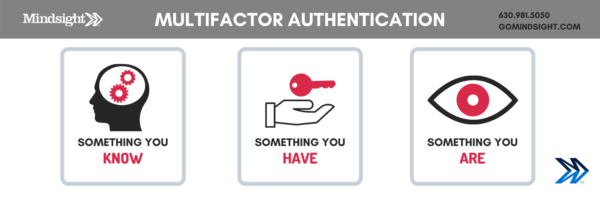
Multi-factor authentication won’t solve your every cybersecurity woe, but it provides another layer to your security posture, targeted directly at the weakest multifactor authentication users.
If you haven’t yet implemented MFA, that’s okay. In fact, waiting for a solution that minimizes the cons of MFA is smart. Today, there are solutions on the market that are inexpensive to implement and easy to scale.
Develop an Engaging and Empowering Training Program
When most of the world is suffering from virtual meeting and PowerPoint fatigue, it’s hard to think of new and exciting ways to deliver information to your teams. And, through the wrong delivery, cybersecurity training can come off as preachy, boring, or even not as serious as it really is.
Instead of statistics or going over procedure ad nauseum, show real-life examples of hacks, and the effects of a poor security posture. Relevance is key. Customize training for different departments, as not all of them encounter the same threats and take time for conversations between departments to share their experiences. This will lead to a deeper understanding of cyber hygiene and its many different components.
To change or alter undesirable behavior, it is critical to empower your teams. Show the “how” and the “why” of cybersecurity. Stress how everyone plays a part in the security scheme and why their role is important. If they don’t feel empowered, their investment in the program will be minimal.
Make It Easy to Report Threats
In most companies, the relationship between IT and other departments is very need-based. Most people only reach out to IT if they need assistance, or worst, if they think they’ve put the network at risk. Communication needs to be open with all departments, and everyone needs to feel positive about reaching out to IT to either report something or to react in a constructive manner when they’ve made a mistake like click on a phishing link.
Introduce the IT team regularly, either through email or in team meetings. Create a very simple protocol to report a problem – either through email or a portal, or even a dedicated phone number they can call. Encourage employees to ask questions if they see something even remotely suspicious.
 Benefits of Promoting Strong Cybersecurity Culture
Benefits of Promoting Strong Cybersecurity Culture
Creating a strong and resilient cybersecurity culture will protect your company against cyber threats and possible data breaches. Though this is a significant investment, the benefits far outweigh the consequences of not having one at all. Keep in mind the average cost of a data breach (Mindsight can help calculate your risk), as well as the loss of business projects and the greater vulnerability to future attacks your company could suffer.
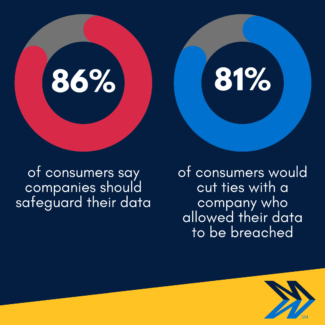
Strong security culture will also create a stronger customer trust and loyalty to your brand — because 81% of companies would cut ties with a company they know has been breached. Proper attention in this area can only grow your brand’s reputation and the costs of security training will be covered in no time.
Every business is different, and the technology and training needed may vary accordingly. While there are some universal truths in cybersecurity, every environment is different.
Mindsight has always offered free whiteboard chats with our engineers. Now more than ever we hope businesses will take advantage of our expertise to make decisions that reduce risk.
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About the Author
Kim Morgan is part of the Marketing Department at Mindsight. Since 2007, she has devoted her career to using digital media to educate and effectively communicate a variety of topics at all levels of expertise. Kim’s favorite part about Mindsight is how team members are encouraged to always be curious, and continue developing not only professionally, but also personally. When not working, she can be found toting her 4 kids around in her sweet sweet minivan while rocking out to hits from the late 90’s and early 2000’s.
 Benefits of Promoting Strong Cybersecurity Culture
Benefits of Promoting Strong Cybersecurity Culture