October 29, 2019 by Siobhan Climer and Mishaal Khan
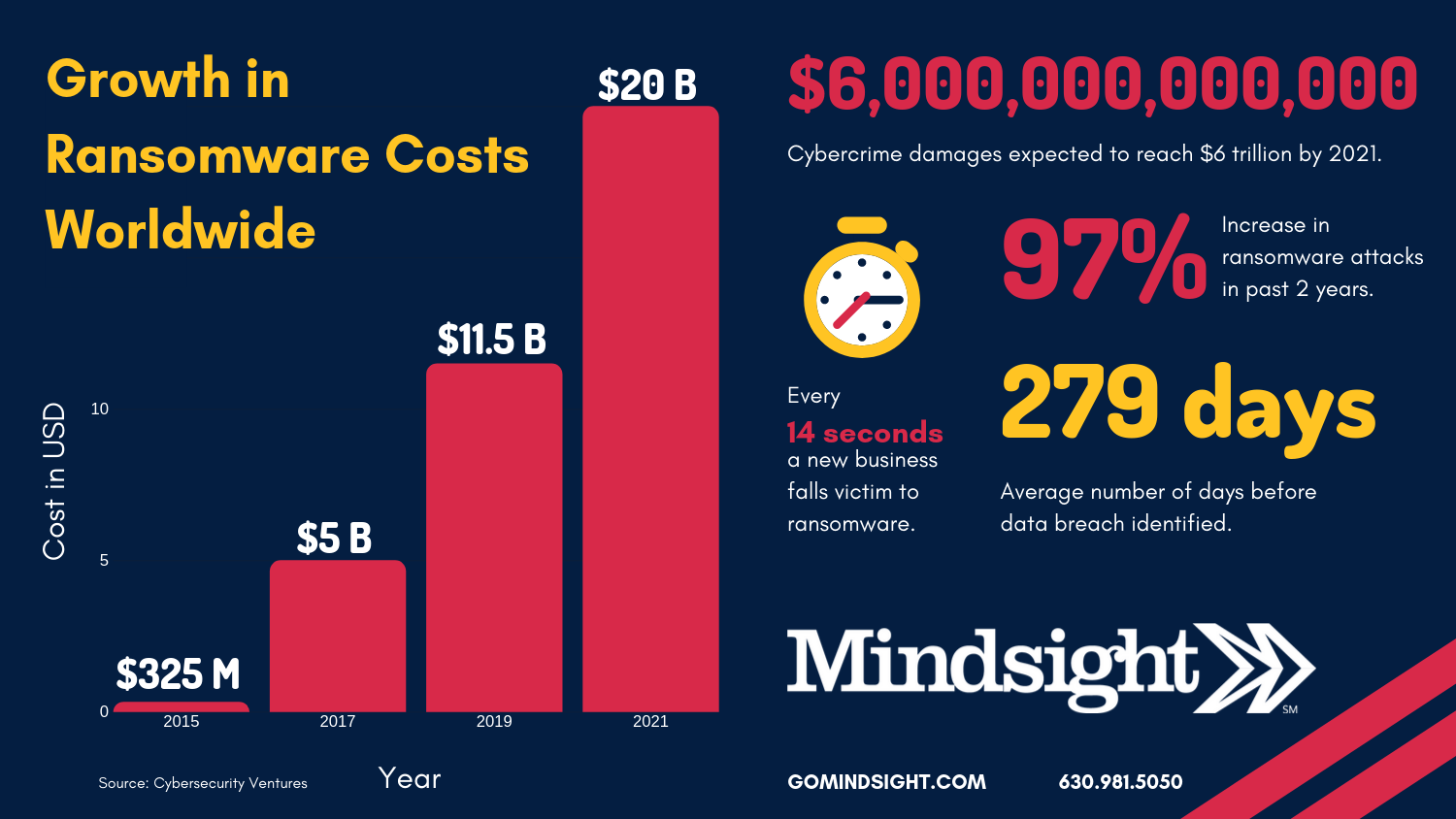
Ransomware risks are up significantly in the first half of 2019 and are only anticipated to rise in the next 2 years – reaching an expected $20 billion in costs globally by 2021.
Manufacturing, in particular, has been hit heavily by ransomware attacks. In early October, major German manufacturer Pilz was the victim of a massive ransomware attack and remained down for over a week.
Downtime costs money. Just last year, we developed a Downtime Cost Calculator to help businesses calculate the financial impact of downtime. Since then, the impact of ransomware has only grown. The average ransom payment increased by 184% in the beginning of 2019 and affected businesses for an average of 9.6 days.
Ransomware Disrupts Production, IT Services, And Logistics
Pharmaceutical manufacturer Merck & Company, food manufacturer Mondelez International, multinational aluminum producer Norsk Hydro, and French car manufacturer Renault: what do these disparate manufacturers have in common?
All were victims of ransomware and experienced significant downtime, affecting production and IT systems. The October 13th attack on Pilz illustrated the damage ransomware can have, even on enterprise-level organizations.
All of Pilz’s locations across 76 countries were forced to disconnect from the main network, were unable to file new orders, and could not check and report on customer statuses. It took over three days to regain access to internal email services, and well over a week to restore product order and delivery systems.
Why Manufacturing Looms As Target For Ransomware
Manufacturers are often slow to upgrade IT infrastructure, and these legacy systems frequently have well-known exploitable vulnerabilities. The complexity of the manufacturing supply chain, with its connected web of suppliers, production lines, multinational sites, and logistics also increases the risk.
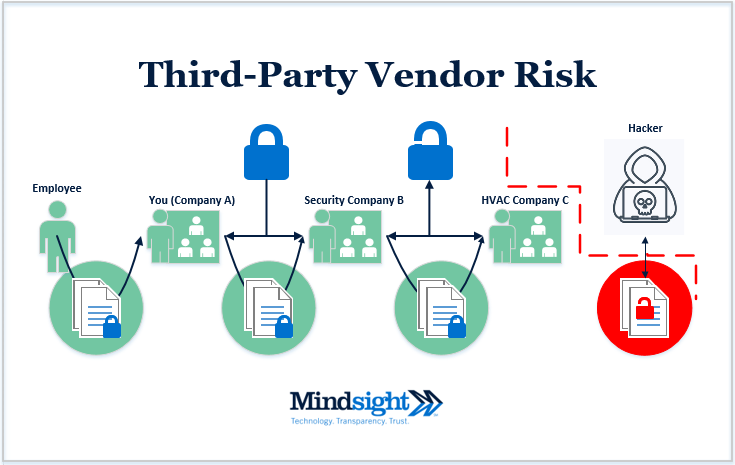
With so many hands in the process, it’s easy for something to slip by. In the example of Taiwan Semiconductor Manufacturing Company, the software shipped by a third party vendor was infected with WannaCry ransomware.
Third-party vendor risk is nothing new; in the infamous Target data breach, it was via an insecure HVAC vendor cybercriminals were able to exfiltrate credit card information.
The New York Times’ recently reported on the motivations of cybercriminals who target manufacturers:
“Some using ransomware hope to extort money – sometimes in the form of cryptocurrencies – from companies whose systems are shut down. Others seek to steal intellectual property – a host of trade secrets including patent information and formulas, as well as blueprints and schematics.”
Nation States Use Ransomware To Fight Cyberwar
In June of 2019, Asco, a Belgium aircraft parts manufacturer, was forced to shut down international production, with many reports indicating this was due to a ransomware attack. While companies are often hesitant to identify if they were hacked – Asco did not confirm the source of the attack – the cyber cold war has reached a new level. External analysts concur that Asco, and other manufacturers in countries around the world, are at increased risk.
Manufacturing, which remains the foundation of infrastructure and economic growth in much of the world, is a prime target for nation states. And since manufacturers often lag behind in terms of infrastructure IT systems, they become the perfect target for cybercriminals.
How Manufacturers Can Defend Against Ransomware
Ensuring you have an up-to-date, tested disaster recovery program with regularly tested backups is fundamental to the defense against ransomware. To find out more about how disaster recovery and data security intersect, read our latest point-of-view paper on their intersection.
Informed cybersecurity centers on identifying the most mission-critical data and assets to the business. By determining what applications and workloads are the most critical to your employees, you can defend your company from ransomware threats.
Find out more about how to protect against ransomware by engaging in a complimentary whiteboard session – in-person or via web meeting – to discuss the risks to your organization and what you can do to prevent being a victim.
Like what you read?
Contact us today to discuss the risk of ransomware to manufacturers.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
Securing Your ICS Environment: Cybersecurity Protection In Manufacturing