January 2, 2018 by Siobhan Climer
 Mitigating third-party vendor risk is a necessary component of any CTO, CIO, or CISO work day. In today’s world, though, it’s a part of doing business. Partners enable improved business efficiencies and a competitive advantage over others. The right partner can prove to be an essential component of your future business strategy. The wrong partner can open you up to cyberattacks and data breaches while also decreasing efficiency and dealing you disadvantage after disadvantage.
Mitigating third-party vendor risk is a necessary component of any CTO, CIO, or CISO work day. In today’s world, though, it’s a part of doing business. Partners enable improved business efficiencies and a competitive advantage over others. The right partner can prove to be an essential component of your future business strategy. The wrong partner can open you up to cyberattacks and data breaches while also decreasing efficiency and dealing you disadvantage after disadvantage.
The digital supply network your business uses is complex, interconnected, and dynamic. While a more holistic, supportive network benefits the organization overall, the increased complexities and openness of a digital supply network also increases the complexity of vetting vendors. This makes the supply chain an intriguing target for cyberattacks.
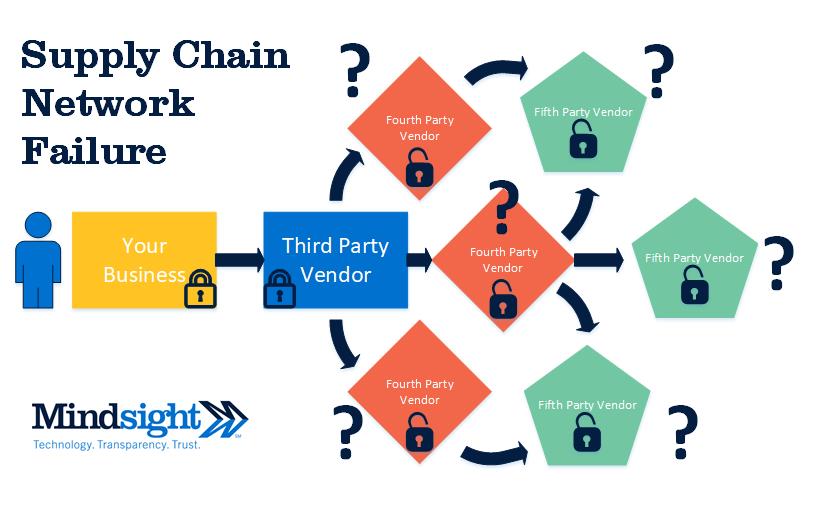
A Microcosm Digital Supply Chain Network Failure
Managing third-party risks comes down to understanding the network that interacts with your business. The improved agility of a digital supply network is also its downfall. Developing new partnerships means creating an intricate – and often insecure – network that can impact your risk assessment. Understanding each relationship within your digital supply network is vital to protecting the security of your organization.
Now imagine this series of relationships compounded repeatedly across all aspects of your business. This opens the business up to risk from multiple angles, many not even involving the partners you’ve vetted.
An Infamous Example
 Back in 2014, Target was the victim of a large data breach that left over 40 million credit and debit cards exposed. How did such a large hack occur? Through a third-party HVAC vendor. Many companies use internet-connected HVAC (heating, ventilation, and air conditioning) systems, and it was through this system hackers accessed the point-of-sale (POS) systems and stole valuable personal credit information (PCI).
Back in 2014, Target was the victim of a large data breach that left over 40 million credit and debit cards exposed. How did such a large hack occur? Through a third-party HVAC vendor. Many companies use internet-connected HVAC (heating, ventilation, and air conditioning) systems, and it was through this system hackers accessed the point-of-sale (POS) systems and stole valuable personal credit information (PCI).
As it turns out, over 55,000 HVAC systems do not have adequate security.
The attack, in this case, didn’t target Target directly. It was through the digital supply network hackers were able to gain access to Target’s data.
How could this affect you?
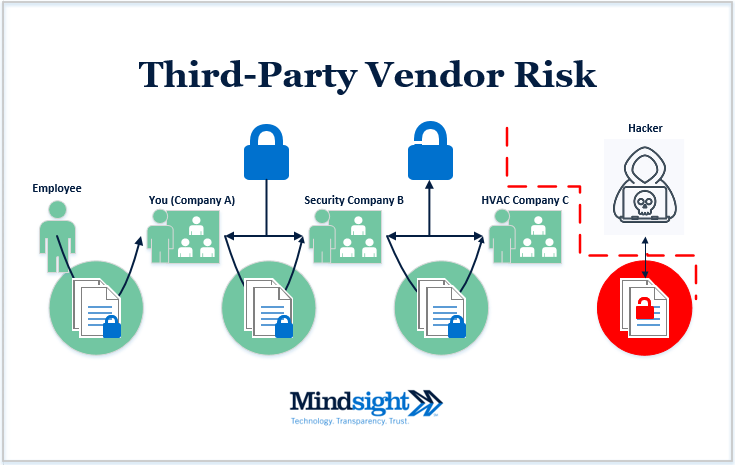
Let’s say you – Company A – perform background checks on your employees. You outsource this task to a security firm, Company B. Company B uses HVAC systems in their buildings and partners with company C. Company C uses internet-connected HVAC systems that are improperly secured and suffers an external cyberattack. What happens next? The personal information of any employee you submitted to Company B has been compromised (see below).
Preventing Digital Supply Network Attacks
There’s no silver bullet. Developing a complete security posture is the first step. You need to perform risk assessments for every aspect of your business, but especially of the digital supply network. You need to understand your business objectives fully, verify all claimed accreditations, collect certificates and analyses from every partner, and craft a thorough contract that includes SLAs.
Taking security seriously is what Mindsight does. Contact our team to find out how we can help protect your digital supply network from the growing risk of cyberattacks.
Like what you read?
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Author
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.