January 20, 2022
As global cybercrime grows more sophisticated and widespread, cyber insurance is growing more popular among organizations of all sizes. Here’s the catch: Many insurers won’t underwrite a policy if certain security measures aren’t already in place. That’s becoming very common.
Which means any C-suite leader who still relies mainly on their insurance company to blunt the potentially catastrophic impact of a data breach (rather than taking proactive steps to safeguard their most sensitive information) is in for a shock. Those who’ve already encountered this roadblock know what a challenge it can be to overcome.
“Insurance carriers have caught on and are now saying they don’t want to be on the hook for millions in coverage if something happens,” Khan says. “That’s why companies must have cybersecurity protocols in place so securing a policy is easier and less costly.”
On February 15, Mindsight will host a virtual event, Cyber Insurance Requirements in 2022: What You Need To Know, that will address this increasingly important issue. Featuring our Cybersecurity Practice Lead Mishaal Khan in conversation with cyber insurance specialist Charlie Stenger of the Sunstar Insurance Group, it will cover everything from what insurers require in order to underwrite a policy and how pricing can vary significantly, to specific steps you can take so you’re not caught off guard when trying to secure a policy. This will be a Q&A session between our experts and the audience.
“When companies get hacked, there are unknown costs involved that can be stratospheric,” Khan says. “Whether intangible or hard costs, they would have been covered by cyber insurance.”
But only if the insured party is granted coverage in the first place. And there are many reasons why it’s denied.
“If you don’t have remote MFA in place,” Stenger says by way of example, the carrier will say ‘no thank you.’ Because of all the issues going on, they’re not letting it slide anymore.”
Insufficient coverage is an issue, too. Besides not fully covering losses in the event of an attack, it can also affect customer relationships. After being encouraged by Stenger to go with a $5 million policy, one of his clients instead opted for $3 million of coverage because the premium was lower. But when they landed a big new client, that client insisted on a $5 million policy before doing business.
Managed services providers (MSPs) like Mindsight can help by performing client security assessments that identify gaps and deliver necessary measures to close those gaps, including timelines and budgets. MSPs are typically in touch with client insurers throughout the year to make sure all necessary protocols are in place. That way, issues are addressed, and premiums lowered before the next insurance renewal date. Scrambling to get your proverbial ducks in a row only after coverage has been denied is inadvisable.
Here are the typical requirements for cyber coverage so you’re prepared when your next renewal date rolls around. If you’ve already met all of them, well done and rest easy. If that’s not the case, however, there’s no time to waste.
Annual Employee Training
Security is most effective when everyone’s in the know. That doesn’t mean they all need technical expertise, but it does mean increasing awareness of how their organization can be vulnerable to cybercrime via methods like social engineering, phishing emails and other ploys that leverage human psychology to breach internal systems.
Annual Accounting Staff Training
According to the FBI, billions of dollars are lost each year to something called payroll diversion. “The scam is frequently carried out when a subject compromises legitimate business or personal email accounts through social engineering or computer intrusion to conduct unauthorized transfers of funds.” That’s why every employee who handles financial transactions needs to be aware of potential vulnerabilities. Additional scams include wire fraud and W-2 phishing.
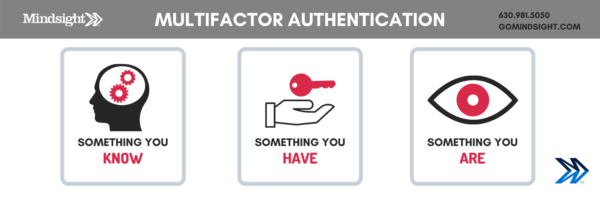
Multi-Factor Authentication (MFA)
Whether or not you’re part of a larger organization, MFA is one of the most basic and effective ways to protect sensitive information. Rather than logging on with just a password, MFA requires another form of identification (a randomly generated code or maybe a fingerprint scan) before you’re allowed entry. This way, even if a criminal figures out your password, it’s not enough to breach an account or a system.
Endpoint Detection and Response (EDR) Software
These tools constantly identify and monitor network threats. For example, here’s how Microsoft’s Defender for Endpoint solution works: “When a threat is detected, alerts are created in the system for an analyst to investigate. Alerts with the same attack techniques or attributed to the same attacker are aggregated into an entity called an incident. Aggregating alerts in this manner makes it easy for analysts to collectively investigate and respond to threats.”
Software Patching and Updates
This is another basic practice that delivers real results when it comes to security. Make sure to regularly install patches and repair bugs. Not doing so is like failing to fix chinks in a suit of armor. Sooner or later the enemy will find those openings and exploit them to the fullest. Monthly vulnerability scans are a good way to find technological soft spots before they become an issue.
End-of-Life Software
Just as the functionality and security of old smartphones diminish when they’re no longer able to install critical software updates, outdated software has the same effect on your system. Running the most current versions and regularly updating older versions can help protect against cyber intrusions while keeping your operation running smoothly.
Remote Desktop Protocol (RDP)
Remote access is a great tool. Until it’s not. If you can directly access another computer over your network, so can someone with nefarious intentions — like, for instance, spreading malicious software that could wreak havoc. So make sure your RDP is secure by, among other things, prohibiting direct exposure to the Internet, allowing access only via VPN and requiring multi-factor authentication.
Endpoint Protection/Anti-Virus Software
If it’s centrally managed and correctly configured, this goes a long way toward preventing malware and other malicious applications from compromising your system.
System Backups
What if there’s a fire, a flood or an earthquake, and every computer in your business is destroyed? What if crucial hardware suddenly goes kablooey? What if there’s a cyberattack that paralyzes your systems? The solution to all those worst-case scenarios is onsite and offsite system backups that are encrypted, strictly monitored and guarded by anti-virus software. Additionally, test your data recovery methods every six months or so to make sure you’re ready for a real-life emergency.
Incident Response and Business Continuity Planning
In the event your systems are breached by cybercriminals, the last thing you want to do is respond frantically or chaotically. That’s why it’s vital to have a workable plan in place for mitigating damage and communicating internally. If you’re hit by ransomware or malware, which can be even more destructive than a flood or a fire, you can remain calm while business operations suffer minimal disruption.
Like what you read?
Contact us today to discuss the steps you need to take to remain compliant.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Expert
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.



