March 2, 2021
By: Kim Morgan
In years past, we began each new year with an article about the biggest cyberattacks of the pervious year. However, 2020 proved to be a year SO full of breaches and attacks, we devoted space for the first quarter, second quarter, and third quarter of 2020. Today we conclude this four-part series. I’d like to say that valuable lessons were learned between the beginning of the year to the end of the year, and we saw a decrease in the severity of the attacks. Unfortunately, the stakes grew towards the end of they year. Hopefully, these lessons are strong enough to carry to 2021, and we can go back to the one and done article format? Here’s hoping!
October 2020
 Barnes and Noble
Barnes and Noble
In October of 2020, US bookseller Barnes and Noble confirmed a cyberattack impacting their eBook reader and storage platform, Nook.
As reported by Bleeping Computer, the problem was first discovered as people across all social media channels complained they could not access their Nook libraries or that previous purchases had disappeared, or that they could not log into the platform. The outage also seemingly spread to some of Barnes and Noble’s 600 nation-wide stores where it appeared some cash registeres were unable to function.
Though first blamed on network issues, Barnes and Noble confirmed that cyberattackers caused the service disruption. In an email, the bookseller said that on October 10, Barnes & Noble was the victim of intrusion, leading to “unauthorized and unlawful access to certain Barnes & Noble corporate systems.” Customer email addresses, billing and shipping addresses, telephone numbers, and transaction histories may have been exposed during the breach.
As of October 21, 2020, the Egregor group (a relatively “new kid” on the hacker scene), claimed responsibility for the attack. They claimed their malware was responsible for the breach and also claimed to have stolen unencrypted financial audit data. It is unclear if that refers to internal or customer data.
A member of the group said that someone was able to gain access to a Windows domain admin account before turning over that access to Egregor. This is a relatively new trend from 2020 – where someone will gain access to an environment and sell said access to a larger hacker collective. For prices between $300 and $10,000, ransomware groups can easily buy initial network access to already-compromised companies on underground forums.
Since then, Egregor published “two Windows Registry hives that appear to have been exported from Barnes & Noble’s Windows servers during the attack,” according to the media report. The files however don’t prove that the gang has financial data.
Ubisoft and Crytek
On the heels of Barnes and Noble the hacking gang (collective? Flock?) Egregor announced they had gained access into the systems of game developers Ubisoft and Crytek. Data allegedly taken from each company has been published on the ransomware gang’s dark web portal ahead of the announcement.
Egregor suggested they possessed source codes from one Ubisoft’s games, which was scheduled to be released later in that month. Ironically, security exerts have tried to reach out to Ubisoft via Twitter about several employees who had been phished. Though not confirmed, this may explain how the breach occurred.
November 2020
 Vertafore
Vertafore
The Denver-based company Vertafore produces software that insurance companies and brokerages use to keep track of customer data. Like utility companies, insurance companies keep track of far more data than more traditional B2C businesses.
In November of 2020, Vertafore disclosed a third-party had accessed the details of 27.7 million Texas drivers. The incident is believed to have taken place sometime between March 11 and August 1, and happened as a result of human error when three data files were inadvertently stored in an unsecured external storage service.
Exposed data included Texas driver license numbers, names, dates of birth, addresses, and vehicle registration histories. Fortunately, this data set did not include social security numbers or any financial information.
At the time of the release, the Texas Attorney General, Texas Department of Public Safety, the Texas Department of Motor Vehicles, and federal law enforcement were all notified of the breach. Vertafore also reached out to the Texas drivers whose data was part of this hack.
Vertafore said it has worked with an intelligence firm but has not found any evidence that the leaked data has been abused or misused.
“Although that firm did not find any evidence, to be considerate of all Texas driver license recipients and out of an abundance of caution, Vertafore is offering them one year of free credit monitoring and identity restoration services in recognition that these services offer valuable protection in other contexts beyond this event,” Vertafore said.
This underscores the trend in targeting local or federal government agencies. The extraction and sale of PII is a growing business, and consumers have little power to protect their data after it is handed off to a government agency and their sub-contractors.
Embraer
First identified on November 25, 2020, Brazilian aerospace and defense group Embraer disclosed they targeted by a cyberattack that impacted the company’s operations. As a consequence of the attack internal systems suffered a partial and temporary interruption, which temporarily impacted some operations.
According to Brazilian newspaper O Globo, the incident in question was a ransomware attack, which required the deactivation of a significant share of the servers operated by the company, which is currently operating under a contingency plan, with enhanced security.
No other details were released.
DECEMBER 2020
Fire Eye
As if 2020 wasn’t enough of an “unprecedented” year, FireEye, one of the world’s largest security firms was hacked and that a “highly sophisticated threat actor” accessed its internal network and stole hacking tools FireEye uses to test the networks of its customers. In a press release, FireEye CEO Kevin Mandia said the threat actor also searched for information related to some of the company’s government customers. Cool.
Mandia described the attacker as a “highly sophisticated threat actor, one whose discipline, operational security, and techniques lead us to believe it was a state-sponsored attack.”
“Based on my 25 years in cyber security and responding to incidents, I’ve concluded we are witnessing an attack by a nation with top-tier offensive capabilities,” Mandia said in a statement released after markets closed on December 8th.
“This attack is different from the tens of thousands of incidents we have responded to throughout the years,” the FireEye top exec added.
“The attackers tailored their world-class capabilities specifically to target and attack FireEye. They are highly trained in operational security and executed with discipline and focus.
“They operated clandestinely, using methods that counter security tools and forensic examination. They used a novel combination of techniques not witnessed by us or our partners in the past.”
This attack itself was huge news in the tech world, and sadly only eclipsed by our last hack in this report.
 The United States of America
The United States of America
Well, ok, so that is a bold and blanket statement, saying that “The Untied States of America” was a cyber target. But, in effect, federal systems and multiple federal law enforcement agencies were all part of a large global attack which led to several data breaches. The cyberattack and data breach were reported to be among the worst cyber-espionage incidents ever suffered by the U.S., due to the sensitivity and high profile of the targets and the long duration (eight to nine months) in which the hackers had access.
While in the grips of the coronavirus pandemic, another threat was manifesting, unbeknownst to all: the Russian government’s hack of SolarWinds’s proprietary software Orion network monitoring program was destroying the security of top American government agencies and tech companies.
The United States Cybersecurity Infrastructure and Security Agency (CISA) said the hacks posed a “grave risk” to US governments at all levels. As time went on more and more government agencies and companies were revealed to have been hacked. This includes the Department of State; Department of Homeland Security; National Institutes of Health; the Pentagon; Department of the Treasury; Department of Commerce; and the Department of Energy, including the National Nuclear Security Administration. Vendors Mimecast, Palo Alto Networks, Qualys, and Fidelis confirmed in early 2021 they were also targeted during the SolarWinds supply chain attack.
As of today, the total effects of the breach are still unknown.
Think your organization might need some extra protection? Contact us for a complimentary vulnerability scan.
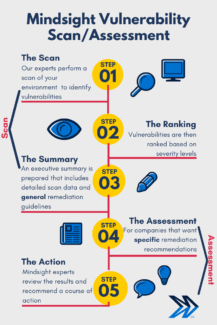
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About the Author
Kim Morgan is part of the Marketing Department at Mindsight. Since 2007, she has devoted her career to using digital media to educate and effectively communicate a variety of topics at all levels of expertise. Kim’s favorite part about Mindsight is how team members are encouraged to always be curious, and continue developing not only professionally, but also personally. When not working, she can be found toting her 4 kids around in her sweet sweet minivan while rocking out to hits from the late 90’s and early 2000’s.
 Barnes and Noble
Barnes and Noble Vertafore
Vertafore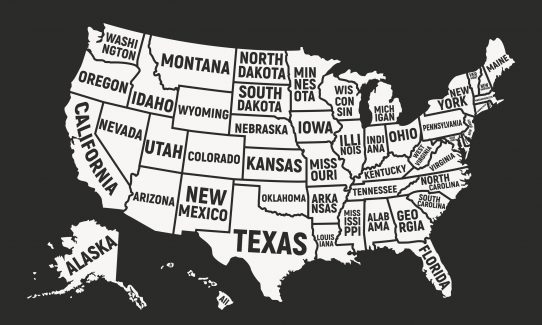 The United States of America
The United States of America