January 28, 2021
By: Kim Morgan
What do gaming company Nintendo, manufacturing veteran Mitsubishi, and tween accessory empire Claire’s have in common? The were all hacked in the second quarter of 2020. In a crazy year where at least 36 billion data records were exposed, threats began to rapidly increase as the world was thrown into the chaos of COVID-19.
Last week at examined major cybersecurity breaches of the first quarter of 2020. Today we will look at a rundown of some of the most major breaches of the second quarter of 2020. This is around the time stay at home orders went into effect as well as access to pandemic relief funds.
April 2021
US Small Business Administration (SBA)
In April of 2020, the US Small Business Administration (SBA) revealed a suspected data breach impacting the portal used by business owners to apply for emergency loans. These loans were part of a stimulus package approved earlier in the month to help small business owners face cover revenue lost because of the COVID-19 pandemic.
A letter sent to disaster loan applicants, dated April 13, explains that a breach was detected on March 25. A section of the portal was disabled while a security issue was resolved — although no details have been made public on the nature of the issue. Approximately 8,000 records may have been compromised including name, social security number, email address, dates of birth, citizen status, and insurance information.
Unfortunately, this wasn’t the first major cybersecurity breach associated with the COVID-19 pandemic. In the five weeks between the first shutdowns (mid-March 2020) and the discovery of this breach (April 23, 2020), spam and phishing scams rose by 6000%. Many of those scams used language related to the pandemic and federal relief dollars associated with the pandemic.
Sample emails collected by IBM X-Force researchers reveal that small business owners are being targeted by fake SBA officials, promising recipients government funds to keep them afloat during the crisis. Close to 40% of business owners surveyed by IBM believe they have received at least one such email, which often contain malicious attachments designed to deploy malware on their devices.
 Nintendo
Nintendo
On April 24, 2020, gaming behemoth Nintendo confirmed that hackers managed to access around 160,000 user accounts since the beginning of that month. The discovery was made after users complained about hackers accessing their Nintendo accounts and then abusing attached payment card info to buy Fortnite currency and other Nintendo games.
At the time, a credential stuffing attack was ruled out of the question. Many users reported using strong passwords that were unique to their Nintendo profiles, and almost impossible to guess or have leaked anywhere online. Instead, the gaming company says hackers abused its NNID integration.
NNID stands for Nintendo Network ID (NNID), which is a legacy login system, used to manage accounts on the old Wii U or Nintendo 3DS platforms.
On newer Nintendo devices, users can link their old NNID accounts to a Nintendo profile. Nintendo didn’t specify what exactly was happening behind the scenes but said that hackers abused this integration to gain access to the main Nintendo profiles. As of April 24, Nintendo disabled the ability to log into accounts using the older NNID profiles.
To mitigate the risk for everyone involved, Nintendo contacted all impacted users to prompt a password reset on both the main and NNID accounts. They recommended that users set different passwords for each account, once the password reset kicks in. Users that uses the same password for the Nintendo and NNID accounts right now were also advised to use different passwords, even if they hadn’t been hacked.
Further, the company is warned customers that hackers might have gained access to other account information, such as Nintendo nicknames, dates of birth, countries of origin, regions, and email addresses.
May 2020
Mitsubishi
On May 20, 2020, the AP reported a cyberattack on Mitsubishi. Part of the data set included information related to a “cutting-edge” missile prototype. The missile, a speed glider known as HGV, was documented in files Mitsubishi and other manufacturers held as part of a bidding process. It has been reported by local news outlets that Mitsubishi did not win the bid.
The cyberattack took place on June 28, 2019, but was only made public in May of 2020, almost a full year after it occured. The Japanese tech giant said approximately 200MB in files were stolen, but this was thought to primarily relate to members of staff.
Mitsubishi acknowledged the cyberattack and the potential theft of data belonging to roughly 8,000 individuals. In addition, the company informed the Defense Ministry of the potential exposure of sensitive information. Chief Cabinet Secretary Yoshihide Suga said that Japan’s Defense Ministry is analyzing the “possible impact of the information leak on national security.”
The intrusion was made possible through the use of a zero-day vulnerability in Trend Micro OfficeScan antivirus software. A Chinese cyberespionage group known as Tick — or Bronze Butler — was blamed for the attack.
 Illinois Department of Employment Security (IDES)
Illinois Department of Employment Security (IDES)
On May 18, 2020 the Illinois Department of Employment Security (IDES) acknowledged a security lapse that exposed the private information of independent contractors and the self-employed. IDES blamed the security incident on a “glitch” in a new system rolled out to process the claims of citizens in the state of Illinois who need to file for unemployment benefits.
IDES employed a new system called Pandemic Unemployment Assistance (PUA) in response to cater to those that found themselves out of work due to state-wide shutdowns. On this system over 44,000 applicants opened a claim within the first 24 hours. Names, Social Security numbers, and other data points — including phone numbers and addresses — related to unemployment claims were leaked through the scheme’s website.
IDES’ data leak was uncovered by a business owner who applied for benefits and realized she was able to view information belonging to others. According to the publication, “thousands and thousands” of records were available. The security hole was plugged within an hour. However, it is not known how many applicants may have been impacted.
The agency did not reveal what caused the data leak.
June 2020
DMI
Not many people know who DMI is, or what they do – but they have one very notable client among several Fortune 100 companies: NASA.
In a blog post published June 3, 2020, the DopplePaymer ransomware gang said it successfully breached the network of Digital Management Inc. (DMI), a Maryland-based company that provides managed IT and cyber-security services on demand.
It is unclear how deep inside DMI’s network the DopplePaymer gang made it during their breach, and how many customer networks they managed to breach. The thing that appears to be clear is that they got their hands on NASA-related files, suggesting they breached DMI’s NASA-related infrastructure.
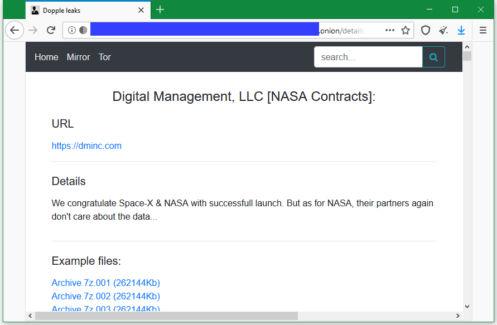
As proof, DopplePaymer posted 20 archive files on a dark web portal the group is operating. The archives include everything from HR files to project plans. Furthermore, the DopplePaymer gang also posted a list of 2,583 servers and workstations that hackers claim are part of DMI’s internal network, and which they have encrypted and are now holding for ransom.
The purpose of releasing all these files is for extortion. The DopplePaymer ransomware crew is one of several ransomware gangs that operate “leak sites” where they publish data from hacked companies. DopplePaymer operators first share small samples like the one they shared today, and in case the victim isn’t intimidated and still refuses to pay the file decryption fee, they leak all files as revenge.
It is unclear how they breached the system.
Claire’s
The data breach Claire’s experienced is another example of a how the uncertainty caused by the COVID-19 pandemic left businesses around the world open to cyber-attacks. It’s also another example of a Magecart attack.
On March 20, 2020, Claire’s closed all of its brick and mortar stores due to worldwide stay-at-home orders. The next day, an anonymous party registered the domain “claires-assets dot com”. Though nothing suspicious occurred for about 4 weeks, malicious code was added to the online storefronts of Claire’s and sister brand Icing the last week of April. This activity was first discovered by Netherlands-based cybersecurity firm Sansec.
The injected code would intercept any customer information that was entered during checkout and send it to the “claires-assets dot com”. The malware was present until June 13th. It is unclear how much data was collected over this time.
The attackers appear to have infiltrated the company’s Salesforce Commerce Cloud environment for at least seven weeks, although the security firm that spotted the breach says there’s no indication that the underlying Salesforce platform itself had a flaw or was hacked.
Attackers tweaked a legitimate file – app.min.js – to make it malicious. To exfiltrate the data, attackers’ code would create a temporary image, append the stolen data to it, transfer the file and then delete the image, Sansec says. “We suspect that attackers have deliberately chosen an image file for exfiltration, because image requests are not always monitored by security systems.”
This large-scale breach has led to a class-action lawsuit against the company, saying their lax security resulted in the disclosure of credit card information.
Next week we’ll take a look at the 3rd quarter hacks of 2020. The industries hacked ran the gamut of tech, education, retail, and even hospitality.
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About the Author
Kim Morgan is part of the Marketing Department at Mindsight. Since 2007, she has devoted her career to using digital media to educate and effectively communicate a variety of topics at all levels of expertise. Kim’s favorite part about Mindsight is how team members are encouraged to always be curious, and continue developing not only professionally, but also personally. When not working, she can be found toting her 4 kids around in her sweet sweet minivan while rocking out to hits from the late 90’s and early 2000’s.
