July 21, 2021 by Siobhan Climer, Mishaal Khan and Kim Morgan
This article was originally published in August of 2019.
Today’s IT strategists know that data security threats cannot be ignored. According to AV-Test, a security research firm, there are over 350,000 new malware programs every day. In fact, since last summer, total malware has steadily increased from 1 billion instances to 1.3 billion instances. 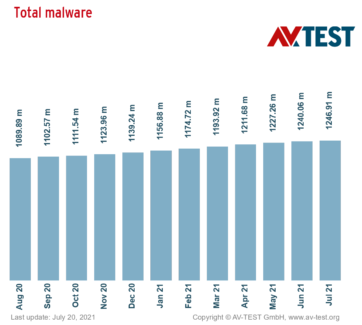
There is nothing to suggest that this trend won’t continue into the future. Knowing this, it is critical that businesses and organizations invests in cyber resiliency, so that when a security event occurs – and it will – critical business data is not lost, compromised or corrupted.
What Is Cyber Resiliency?
Cyber resiliency refers to the intersection of cybersecurity and disaster recovery. These aren’t poorly named avenues in your town’s newest subdivision, but crucial distinctions as to how companies should protect their data.
Many professionals in technology either conflate or bucket these together; however, there are some innate differences.
Disaster recovery is about business continuity. When a disaster strikes, the data needs to be backed up and recoverable so the business can continue.
Cybersecurity is about information asset protection, ensuring the privacy and protection of sensitive personally identifiable information (PII).
Where disaster recovery and cybersecurity meet – at the crossroads of data protection – is cyber resiliency, where the data the business relies on is private, protected, backed up, and recoverable.
Learn more about cyber resiliency and the crossroads of data protection in our white paper.
Building An IT Strategy: People, Process, And Technology
For far too long, information security was relegated to the side in IT strategy, and considered an IT-only issue. For many organizations today, this is still reality. IT leadership still struggles to get their boards and C-suites invested in true cyber resiliency.
It takes hard work, strategy, complete enterprise investment (that means everyone), and, unfortunately, time. But the reward – a resilient business that manages the deluge of threats, attacks, and vulnerabilities with grace and a degree of certainty – is worth the effort.
How To Integrate Cyber Resiliency?
Let’s break down IT strategy into its oldest, most comprehensive buckets: people, process, and technology.
PEOPLE
Seek support
The IT department can’t do it alone. While IT is often the driver of cyber resiliency, you need to have the CEO and your leadership team on board. Secure buy-in from all department heads before you deploy your strategy, and treat this issue as a company-wide initiative.
Build a team
Once leadership is invested, find the right people to build cyber resiliency. This may include a vetted partner, an ethical hacker, and certified security analysts. This is also a great time to consider contracting a Managed Services Partner.
Promote Cybersecurity Culture
Security awareness campaigns, disaster recovery tabletops, and offering real-life advice and guidance to everyone is key to minimizing the human factor risk.
PROCESS
Design technology roadmap
The Technology Roadmap is an often over-looked tool for aligning IT strategy to the business, broadly, and the integration of cyber resiliency.
Analyze risk
Key to digital transformation and cyber resiliency is ensuring you mitigate risks. Whether it is a potential partner, product, or business shift, ensure you identify potential risks and outcomes.
Measure to improve
Identifying baseline performance is the only way to measure and improve your overall security posture.
TECHNOLOGY
Align to business goals
The business goals – whether that’s profit growth, workplace culture improvement, or improving overall efficiencies – must be tied to your cyber resiliency and any technologies you choose to help you reach those goals.
POC before implementation
The newest technologies and dashboards can look and sound amazing, but it is important to validate the technology in your environment before deploying; otherwise, you might find yourself stuck with technical debt.
Deploy with a trusted partner
The right technology partner – who is certified and verified – will:
- Deploy the technology you choose
- Within the roadmap you designed
- To meet the goals you set
All to deliver cyber resiliency to your organization.
What Do You Do First?
Get buy-in from leadership. Digital transformation in action starts at the top. Need help convincing the board that cyber resiliency is a serious threat to the business? Mindsight provides a free POC of DNS filtering, which is a quick and easy way to have actionable insights around security.
Contact us today to discuss cyber resiliency or for vCISO services.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Kim Morgan is part of the Marketing Department at Mindsight. Since 2007, she has devoted her career to using digital media to educate and effectively communicate a variety of topics at all levels of expertise. Kim’s favorite part about Mindsight is how team members are encouraged to always be curious, and continue developing not only professionally, but also personally. When not working, she can be found toting her 4 kids around in her sweet sweet minivan while rocking out to hits from the late 90’s and early 2000’s.