February 22, 2024
Cybercrime is a multi-trillion-dollar plague that negatively impacts organizations and businesses of all types and sizes. Some are more prepared to combat it than others, but cybercriminals are relentless in their efforts to exploit human psychology and even the most sophisticated cyber safeguards. Here are some of the sectors that get hit the hardest.
MANUFACTURING
According to Statista: “For several years, the manufacturing industry has been one of the most targeted sectors of cyber criminals worldwide, resulting in around 250 data violation incidents in 2022 in the United States alone, impacting approximately 23.9 million U.S. users during this period. If successful, attackers demand money, usually in cryptocurrencies, for stolen data points or sell the data on the dark web. In 2022, the global average cost per industrial data breach was around 4.47 million U.S. dollars.”
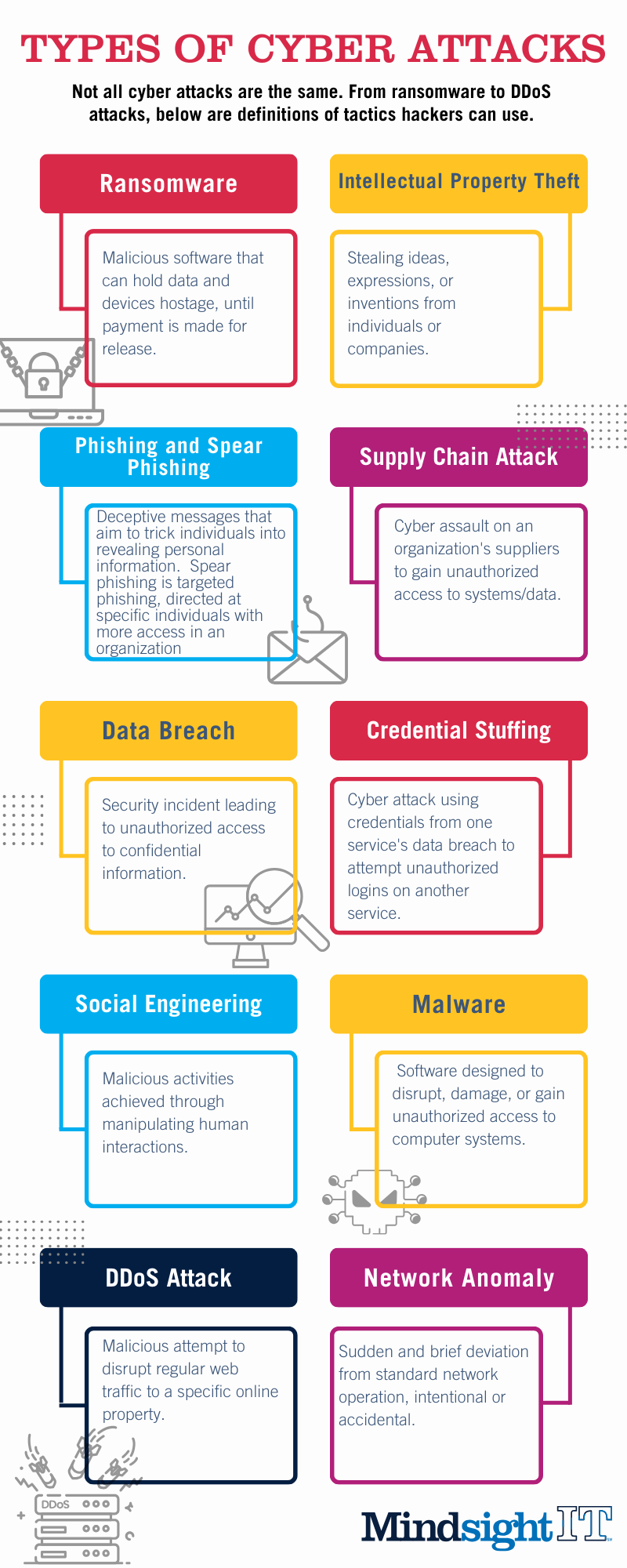
Types of attacks: Ransomware, intellectual property theft, phishing, supply chain.
Recent real-world example: Western Digital. “The hackers who breached data storage giant Western Digital claim to have stolen around 10 terabytes of data from the company, including reams of customer information,” TechCrunch reported. “The extortionists are pushing the company to negotiate a ransom — of a ‘minimum 8 figures’ — in exchange for not publishing the stolen data.”
EDUCATION
According to Zscaler’s Annual Phishing Report, “The education industry experienced the most significant surge in 2022 phishing attempts, jumping from the eighth spot to number one, with an increase of 576%.” As per this summary of a recent Verizon report: “The educational services sector experienced 1,241 incidents in 2021, with 282 involving confirmed data disclosure. Of those attacks, 75% were from external sources, while the remainder involved insiders. These attacks were overwhelmingly motivated by monetary rewards, with 95% involving a financial motive.”
Types of attacks: Data Breaches, Ransomware, DDoS (distributed denial of service) Attacks, Phishing.
Recent real-world example: Illuminate Education. According to one summary of the incident, “In January 2022, cybercriminals targeted the school management platform Illuminate Education and gained access to a database containing personal information on more than 820,000 current and former NYC students. The attack took the New York public school system’s online grading and attendance system offline for several weeks.”
STATE/LOCAL GOVERNMENT
According to a late-2022 govtech.com summary of Verizon’s 2021 Data Breach Investigation Report, “Social engineering is the most common attack method in relation to cybersecurity in the government sector” and “over 69 percent of breaches were due to social engineering, with phishing emails the most prominent vector. The report found that the public sector is particularly vulnerable to attackers who can craft a credible phishing email. Public-sector attackers were overwhelmingly interested in obtaining credentials, with 80 percent of incidents attempting to steal logins and passwords that would further the attacker’s presence in the intended victim’s network and systems.”
Types of attacks: Social engineering, ransomware, phishing and spear phishing, DDoS.
Recent real-world example: Freemont County, Colorado. According to a local newspaper report, “[L]ocal officials said the Governor’s Office of Information Technology determined the cyberattack that affected most county departments was executed by BlackCat ransomware, also known as ALPHV. Actors affiliated with BlackCat often request multi-million-dollar ransom payments of cryptocurrency like Bitcoin or Monero to recover encrypted digital files, according to an April report from the Federal Bureau of Investigation.” Weeks after the intrusion, the article added, the county was still scrambling to get all systems up and running again.
According to Statista, the average cost of a financial industry data breach in 2022 was nearly six million dollars. “By comparison, the average cost of a breach across all industries amounted to over four million U.S. dollars. In the United States, the financial damage of a data breach came to around nine million dollars on average. The two types of attacks causing the highest monetary loss were business e-mail compromise (BEC) and e-mail account compromise (EAC) scams.”
Types of attacks: Malware, phishing and spear phishing, credential stuffing, supply chain attacks, network and system anomalies.
Recent real-world example: U.S. division of ICBC. The world’s biggest bank was hit by a ransomware attack last November. “ICBC said it ‘successfully cleared’ U.S. Treasury trades executed Wednesday and repo financing trades done on Thursday,” a CNBC report indicated. “However, multiple news outlets reported there was disruption to U.S. Treasury trades. The Financial Times, citing traders and banks, said Friday that the ransomware attack prevented the ICBC division from settling Treasury trades on behalf of other market participants.” The ransomware, from a group called Lockbit, was responsible for nearly 28 percent of known ransomware activity in the past year and remains a major threat to organizations in the ransomware landscape.” (Flashpoint, July 2023).
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.

