Updated June 11, 2020 by Siobhan Climer and Mishaal Khan
According to recent reports, COVID-19 is blamed for a 238% surge in targeted cybersecurity attacks of banks. Cyber criminals, who feed on chaos and uncertainty, have taken the crisis as an opportunity. The correlation between news cycle events, such as the announcement of the coronavirus spread in the U.S., and cyberattacks is significant.
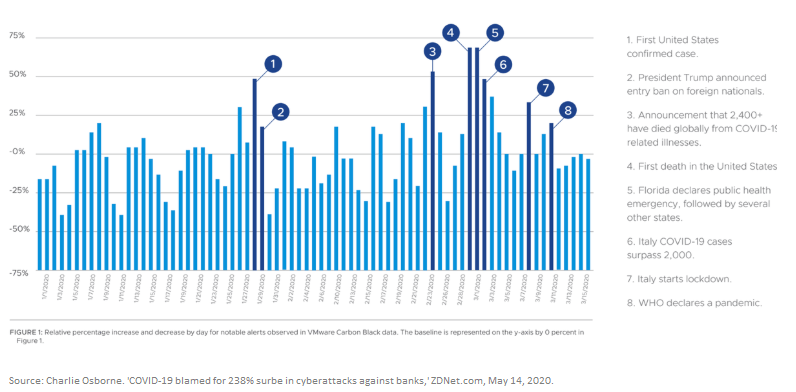
In addition to the spike in attacks, 82% of CIOs in a recent report by VMware Carbon Black report that the cyberattack methods are improving. The report specifically mentions social engineering and other tactics that exploit human weaknesses.
While events have increased the prevalence of cybersecurity threats to financial institutions, the threat vector itself is not new. A number of high-profile data breaches over the past decade have exposed American’s personal information; namely, the 2017 Equifax data breach, which exposed over 143 million American’s personal information; and the 2013 Yahoo breach, which exposed over 3 billion accounts.
These major data breaches have affected over 1 trillion user accounts, and these numbers are only expected to rise. The financial impact of this is huge, as we recently reported. Cyber criminals purchase this information – credentials, account information, usernames, and passwords – on the darknet and then leverage it along with social engineering and other tactics to gain access to financial institutions, bank accounts, credit information, and more.
Despite every attempt to remain secure, financial services make up 35% of all data breaches, earning it the unfortunate title of the most-breached sector. These events remind both business leaders and consumers of the tenuous nature of cyber security. Are you prepared to face these top cybersecurity threats to financial services?
Top Cybersecurity Threats To Financial Services
1. Web Application Attacks
The Attack: From Google docs to calculator tools, webmail platforms to financial records, most of the applications we use today are hosted on the web. These applications are vulnerable to attacks because they are the most accessible and rely on user input.
use today are hosted on the web. These applications are vulnerable to attacks because they are the most accessible and rely on user input.
Applications need to be accessed over Port 80 (HTTP) or Port 443 (HTTPS) to function. The types of web application attacks vary from unvalidated redirects and forwards to SQL injections. DDoS attacks, which we’ll go over in a minute, can fall into this category as well.
The Defense: Use an intelligent Web Application Firewall (WAF) along with the behavioral firewall to block cross-site scripting (XSS) attacks.
Auditing your databases regularly is essential to identify and deal with any vulnerabilities before they are exploited. Simple steps, like clearing stored cookies, avoiding untrustworthy websites, and scanning for viruses and malware are just as important as brushing your teeth and flossing when it comes to cybersecurity health.
2. DDoS Attacks
The Attack: DDoS, or a distributed denial-of-service (denial-of-service), attacks slow down websites by making them unavailable to users. These attacks go a long way to silencing websites that the hackers may disagree with, or disrupting business flow to a competitor. DDoS attacks can be inexpensive ($150 buys a week-long DDoS attack on the darknet), and, therefore, prolific. 1/3 of network downtime incidents are attributed to DDoS attacks, costing businesses financial losses and reputation damages.
 The Defense: Luckily, there are lots of DDoS protection tools and integrated preventative services.
The Defense: Luckily, there are lots of DDoS protection tools and integrated preventative services.
Cisco produced a helpful guide outlining the different DDoS methodologies and prevention steps, which is perfect for a longer read. In brief, remotely triggered black hole (RTBH) filtering is a good option for preventing attack traffic before it hits the network. Anycast, a routing methodology that routes traffic through various nodes, can dilute malicious traffic from DDoS attacks.
Other tools, like reputation-based blocking, can identify malicious URLs and establish a database to protect against future attacks – like adding spam callers to a blocked senders list.
3. Backdoors And Supply-Chain Attacks
 The Attack: Targeted attacks often use “backdoors” – applications used to obtain remote access – in the second or third stage of the attack. By using backdoors, hackers gain access to the network while bypassing intrusion detection systems. Port binding, connect-back techniques, connection availability abuse, legitimate platform abuse, common service protocols, and custom DNS lookups are all examples of backdoor attacks.
The Attack: Targeted attacks often use “backdoors” – applications used to obtain remote access – in the second or third stage of the attack. By using backdoors, hackers gain access to the network while bypassing intrusion detection systems. Port binding, connect-back techniques, connection availability abuse, legitimate platform abuse, common service protocols, and custom DNS lookups are all examples of backdoor attacks.
Cybersecurity threats to financial services are rising, including a recent threat to a financial institution that began seeing suspicious DNS requests while processing financial transactions.
This led to the discovery of ShadowPad, one of the largest supply-chain attacks that originated in legitimate software. Somewhere along the line, someone opened a backdoor, opening up hundreds of customers to serious cybersecurity threats.
The Defense: Auditing and monitoring are the surest ways to detect supply-chain attacks.
In the case of ShadowPad, it was the observation by the monitoring services of the financial institution that first alerted IT to the unusual activity. Firewalls can help, but they won’t prevent access from legitimate requests, even if something malicious is buried inside. Bringing in a trusted partner that manages and monitors your services is one way to ensure you have eyes on your network 24/7/365.
4. Third-Fourth-Fifth Party Vendors
The Attack: Managing risk of third-, fourth-, and fifth-party vendors is a challenge. Though you may have strong protections in place in your own network, when you begin working with other vendors, you must also assess the cyber security threats to financial services of third-party agreements. If your partner is attacked by ransomware, how will that affect your bottom line? Will you be at risk, too? Who is responsible for protecting the network?
 The Defense: Contracts and reviews.
The Defense: Contracts and reviews.
You aren’t in control of your third-party vendors, but you get to decide if they should remain your partner.
Whether it is a cloud provider or a mobile app developer, ensure any vendors you work with have strong security measures in place. Then, make sure any other parties they work with also have secure networks. It can be a convoluted network, but assessing and developing a risk management plan is necessary to protect yourself from these unknowns.
5. Global Operational Risks
The Attack: Globalization means that businesses operate internationally, across state lines, in different towns with different languages, regulations, and expectations. This increase in operational size means an increase in operational risk. Cybersecurity threats to financial services are especially vulnerable, since cyber criminals target the financial sector in the hopes of larger monetary gains.
 The Defense: Assessment. Ask yourself the following:
The Defense: Assessment. Ask yourself the following:
- Where are my third- and fourth-party vendors located?
- What regulations are affecting my business and those of my third-party vendors?
- Are security risks to my business different in different locations? How so?
- What security measures do we need in these different regions?
- Are we expanding? Will our cybersecurity risks expand as well?
Then, determine if your team has the resources necessary to ensure the protection of consumer data. If they don’t, who can you entrust with the responsibility of securing your environment? Finding a trusted managed services provider might be the next step.
6. Emerging Technologies
The Attack: It’s cliché to say it at this point, but technology is always changing. Emerging technologies are useful, necessary, and provide competitive advantages to your institution.
In the finance sector, CIOs and CTOs are already considering how blockchain and the Internet of Things (IoT) can be leveraged to build growth. But these tools also bring additional risks. You can be confident hackers are ahead of you, finding ways to utilize blockchain and IoT for attacks. Just last year, the largest DDoS attack came via IoT.
 The Defense: MFA, patching, and cybersecurity hygiene.
The Defense: MFA, patching, and cybersecurity hygiene.
The risk will never be fully diminished, but there are ways to defend yourself. Regulations are trying to keep pace, including a new measure that requires companies to meet minimum cybersecurity requirements.
In the end, though, financial institutions are responsible for protecting their organization from attacks by using multi-factor authentication internally and enabling device patching to address different vulnerabilities.
Blockchain-Enabled SDN: Evolving Network Security Parameters
7. Insider Threats
 The Attack: Unfortunately, the reality is that 60% of cyberattacks come from inside the company. Financial firms and financial services were in the top three sectors targeted by insider attacks, according to that same IBM report.
The Attack: Unfortunately, the reality is that 60% of cyberattacks come from inside the company. Financial firms and financial services were in the top three sectors targeted by insider attacks, according to that same IBM report.
From disgruntled employees to poorly-compensated bank tellers, 75% of those internal attacks were intentional. These employees can offer up their credentials to a hacker, or simply decline to seriously review cyber security concerns due to poor morale. This makes the employee one of the top cybersecurity threats to financial services.
The remaining 25% of internal attacks are due to human error. Phishing scams and malware downloads can work on even the most loyal and hard-working employees.
The Defense: Identify mission-critical and tighten access.
Protect what is most valuable, tighten access controls, and ensure your employees are satisfied and feel valued for their contributions. A strong organization that protects and rewards employees means your first layer of defense – the people you employ – are ready to make sure institutional assets are safe.
Cybersecurity threats to financial services are pernicious and prolific.
With so much at stake, financial institutions are looking for new ways to address emerging threats head on. A trusted services provider like Mindsight monitors and reviews the risks to your business constantly, giving you peace of mind and your customers someone to rely on.
Contact us today to discuss how to prevent the top cybersecurity threats to financial services.
Like what you read?
Originally Published June 27, 2018, this post has been updated with the latest information on the threats financial institutions may face in the changing global circumstances surrounding coronavirus and remote banking.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.




