July 14, 2020 by Siobhan Climer and Mishaal Khan | This article has been updated to reflect recent developments in security threat vectors.
A common misconception among those outside the cybersecurity sector is that a single technology – a single action or software or strategy – can make an organization “secure”.

This is, of course, untrue. As Certified Ethical Hacker and Mindsight’s own Security Solutions Architect Mishaal Khan says: “You can never secure yourself 100% from anything. Even I cannot help you be 100% secure or 100% private.”
Mishaal goes on to explain that the layered approach to security is important for this very reason. By minimizing attack vectors and securing against specific attack types, organizations are better able to deter malicious entities and protect the business and its data. This is especially critical given the volatility of the threat landscape.
So, what exactly is a layered approach to security?
What Are The 7 Layers of Security?
This question is a bit more complex than it first looks. Many readers may be familiar with the OSI Model, a framework that many early cybersecurity adopters use to prescribe security solutions as related to a networking system.
The OSI Model
Unfortunately, cybersecurity today goes far beyond a networking-only approach. Today, cybersecurity traverses far beyond the network realm to the endpoint, perimeter, and the humans on the other side.
That’s why we propose a new model that looks at cybersecurity more holistically.
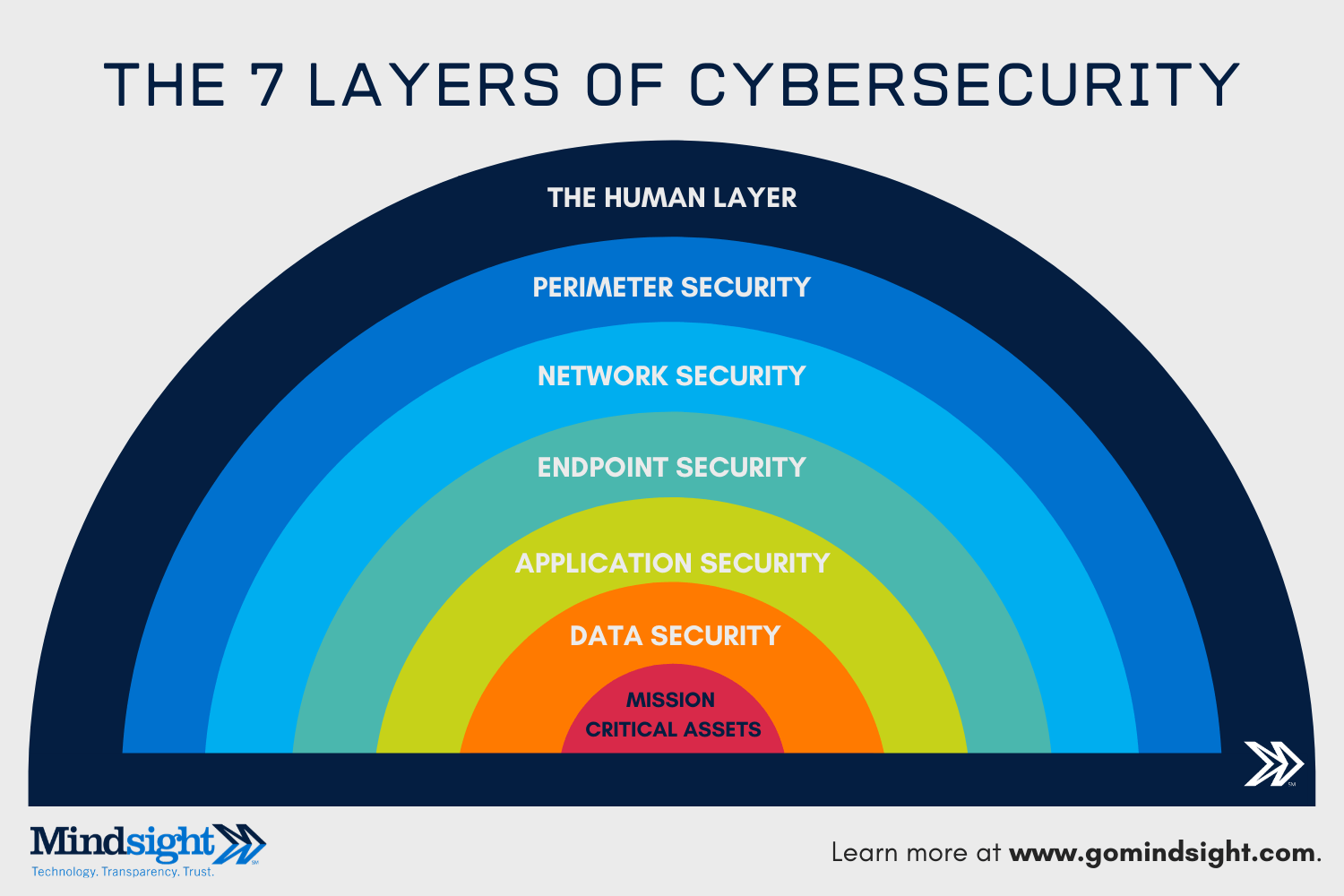
The 7 Layers of Cybersecurity
The 7 layers of cybersecurity should center on the mission critical assets you are seeking to protect.
1: Mission Critical Assets – This is the data you need to protect*
2: Data Security – Data security controls protect the storage and transfer of data.
3: Application Security – Applications security controls protect access to an application, an application’s access to your mission critical assets, and the internal security of the application.
4: Endpoint Security – Endpoint security controls protect the connection between devices and the network.
5: Network Security – Network security controls protect an organization’s network and prevent unauthorized access of the network.
6: Perimeter Security – Perimeter security controls include both the physical and digital security methodologies that protect the business overall.
7: The Human Layer – Humans are the weakest link in any cybersecurity posture. Human security controls include phishing simulations and access management controls that protect mission critical assets from a wide variety of human threats, including cyber criminals, malicious insiders, and negligent users.
*NOT ALL DATA IS CREATED EQUAL and does not require equal levels of protection. Identifying the kinds of data you have, categorizing that which is mission critical, and centering your security program around that is a smart first step towards a more secure organization.
Why Layer Security at All?
Back to Mishaal for a moment:
If you start approaching every aspect of security, perfecting every single security control – it will never end. There will always be new holes, new vulnerabilities. That’s a losing battle in my opinion.
Hackers are always ahead of us. So, we need to have a layered approach and then get narrower and narrower, going through the multiple layers. The layered approach has many advantages. If somebody infiltrates one or two layers, there are still more. Even if all those layers, individually, are weak, combined they form a strong deterrence to attackers.
In essence, deterrence.
A multi-pronged approach to cybersecurity that centers on what you need to protect most is the best way to protect your organization.

How Do You Build a Layered Cybersecurity Program?
A robust security posture doesn’t happen overnight.
The first step is to understand your current environment. Businesses today have complex environments. Remote work, globalization, and cloud computing have dramatically improved efficiencies and productivity in the workplace – but these changes have also added new vectors for attackers.

Perform Basic Discovery
What systems do you use? How many devices? Do you have a firewall? DNS filtering? Access management? The first step is to take an inventory of your current systems.
Test, Analyze, and Repeat
Are your current security controls correctly configured and effective? Before investing in new security tools or solutions, first make sure what you have is what you need. Use the testing and analysis to inform your next decision.
Assess Your Security Program and Compliance
Is there any low-hanging fruit you can snatch to earn some quick wins? What steps do you need to take to ensure you are compliant with industry or federal regulations? Identify what you need to fix first and prioritize security investments.

Strategically Build in Remediation and Controls
Simply forcing users to take a mandated phishing video course or enabling two-factor authorization isn’t incredibly strategic – nor is it always effective. For every control you implement, repeat testing and analysis to ensure it is effective.
And Yet – Prepare to Be Attacked
More than 80% of organizations have been the victims of a cybersecurity attack. Remember, you can never be 100% secure. Ensure you have a tested backup and disaster recovery program and incident response plan.

The 7 Layers of Security in the Time of COVID-19
The outbreak of the coronavirus across the world has long-lasting impacts on cybersecurity and the layers of security protection. In fact, we recently provided analysis of the Barracuda report that found 46% of all companies have reported a cybersecurity incident following the outbreak of COVID-19 and the subsequent lockdown.
 There are a number of factors leading to these numbers:
There are a number of factors leading to these numbers:
- Rapid remote deployments
- Reliance on digital communications
- Disruption to security processes
- Different risks in remote environments
- Shift to cloud-based infrastructures
The increase and likely success of these attacks (49% of survey respondents expected to be the victims of a data breach during the month of April) is cause for concern. Weak or gap-ridden cybersecurity postures will quickly be tested and vulnerabilities will be exploited – if they haven’t been already.
Cyber criminals thrive on uncertainty. The vast amount of change gives them free rein to manipulate, coerce, and exploit.
A holistic model that uses layers of security to protect mission-critical assets is critical. Even if a phishing campaign is successful or a remote network is compromised, the CISO who implements layered approach will have nets further along that decrease vertical and lateral movement within the network of malicious forces.
Security Analysts You Can Trust
Want our experts on your team? Reach out today with any questions you have and get started on building a better security posture. We’re here to help.
Contact us today to discuss the 7 layers of cybersecurity.
Originally published March 12, 2020, this blog has been updated to reflect the changing security challenges elicited by the dramatic shift to remote environments and diversifying attack vectors developing in response to the outbreak of COVID-19.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer is a science and technology writer on technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters.
Strengthen Your Security Posture: Start With A Cybersecurity Framework