February 11, 2021
Over the last three years, cybercriminals stole 834 million records in 4,395 data breaches. And that’s just in the United States. Worldwide, that first figure balloons to the billions — 36 billion in 2020 alone. Much of the stolen information was sold on the so-called “dark web” to identity thieves who used it to amass piles of cash.
 And yet, most small and mid-sized companies fail to get serious about cybersecurity until they themselves are targeted. Even then, there’s still a widespread mentality of “insurance will handle it.” Mishaal Khan, Mindsight Cybersecurity Practice Leader and Solution Architect, thinks both of those approaches are deeply misguided. Being proactive rather than reactive about security, he says, is key to preventing external hacks that can do major damage to your firm’s reputation, which in turn adversely affects your bottom line — often in ways that are irreversible.
And yet, most small and mid-sized companies fail to get serious about cybersecurity until they themselves are targeted. Even then, there’s still a widespread mentality of “insurance will handle it.” Mishaal Khan, Mindsight Cybersecurity Practice Leader and Solution Architect, thinks both of those approaches are deeply misguided. Being proactive rather than reactive about security, he says, is key to preventing external hacks that can do major damage to your firm’s reputation, which in turn adversely affects your bottom line — often in ways that are irreversible.
That’s why he strongly recommends a stem-to-stern scan of your company’s systems to establish a baseline of potential vulnerabilities, plus external pentesting at least annually. Absent those basic but crucial measures, Khan says, organizations are just asking for trouble. And many of them will find it.
“New bugs are discovered all the time, so that’s why you can’t just say, ‘I got a scan three years ago, but I never change anything, so I’m still good.’ No, you’re not good.”
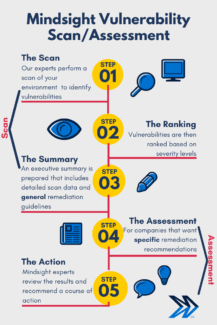
Here’s how Mindsight approaches it: Our cybersecurity experts perform a scan of your network to identify vulnerabilities in your servers, network devices, firewalls, virtual machines, applications, and anything connected to the network — known or unknown. Vulnerabilities are then ranked based on severity levels, and an executive summary is prepared that includes detailed scan data and general remediation guidelines. For companies that want specific remediation recommendations, Mindsight can perform a vulnerability assessment. Mindsight experts then review the results and recommended courses of action with stakeholders.
 As for the notion that insurance will sufficiently cover losses in the event of a breach, Khan says, that’s pure fantasy. Far beyond stolen funds or infrastructure damage, cyber attacks cause reputational carnage that’s not easy to define in dollars. “Insurance companies don’t want to pay until they see an actual amount of damage,” he says. “And in cybersecurity, how do you prove that a loss in value caused by a data breach resulted in future lost profits? You can’t.” Insurance doesn’t usually cover the cost to improve your security after a breach either.
As for the notion that insurance will sufficiently cover losses in the event of a breach, Khan says, that’s pure fantasy. Far beyond stolen funds or infrastructure damage, cyber attacks cause reputational carnage that’s not easy to define in dollars. “Insurance companies don’t want to pay until they see an actual amount of damage,” he says. “And in cybersecurity, how do you prove that a loss in value caused by a data breach resulted in future lost profits? You can’t.” Insurance doesn’t usually cover the cost to improve your security after a breach either.
 Considering that cybercrime can cost small and mid-sized companies anywhere from $10,000 to many millions, Khan (who’s also a certified ethical hacker) is puzzled by those who remain reluctant to invest in effective protection. Because while vulnerability scans and pentesting might run a few thousand dollars every now and then, that’s a drop in the proverbial bucket compared to clean-up costs incurred after an attack occurs. In fact, Khan says, it’s even minimal compared to what most companies spend on coffee and paper. That’s why he and his colleagues at Mindsight are increasingly communicating with high-level decision-makers who know that long-term stability in an extremely online world requires technological diligence and financial investment.
Considering that cybercrime can cost small and mid-sized companies anywhere from $10,000 to many millions, Khan (who’s also a certified ethical hacker) is puzzled by those who remain reluctant to invest in effective protection. Because while vulnerability scans and pentesting might run a few thousand dollars every now and then, that’s a drop in the proverbial bucket compared to clean-up costs incurred after an attack occurs. In fact, Khan says, it’s even minimal compared to what most companies spend on coffee and paper. That’s why he and his colleagues at Mindsight are increasingly communicating with high-level decision-makers who know that long-term stability in an extremely online world requires technological diligence and financial investment.
To that end, Khan will keynote an upcoming virtual security event hosted by Mindsight. Titled “Calculating the Real Costs of a Data Breach,” scheduled for February 23 from 11 to 11:45 a.m. Central Time (register here).
“I hope it will shed light,” Khan says, “on how we should see cybersecurity: as a savior rather than an expense.”
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About the Expert
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.