March 25, 2025
Let’s be real—cyber threats aren’t slowing down anytime soon. Whether you’re a small business owner, an IT manager at a mid-sized company, or part of a large enterprise, the risk of cyberattacks is something you can’t afford to ignore. The challenge? While big corporations have entire security teams dedicated to fending off threats, small and medium-sized businesses (SMBs) often have limited resources, making them prime targets for hackers.
One of the best (and surprisingly simple) ways to step up your cybersecurity? Hardware tokens for Multi-Factor Authentication (MFA).
The Rising Threat of Cyberattacks
Cybercriminals are working overtime, and the numbers prove it. In 2023 alone, the FBI received over 880,000 cybercrime complaints, a 10% increase from the previous year. The financial losses? A staggering $12.5 billion—a 22% jump from 2022.
But here’s the thing—small businesses aren’t just part of this trend; they’re one of the biggest targets. SMBs make up 43% of cyberattack victims, with the average attack costing about $25,000 per incident. In 2020, small businesses suffered over 700,000 attacks, leading to $2.8 billion in damages. The situation isn’t improving—41% of small businesses reported being hit by cyberattacks in 2023, up from 38% in 2022 and nearly double the 22% reported in 2021.
Clearly, just having a strong password isn’t cutting it anymore.
What Are Hardware Tokens?
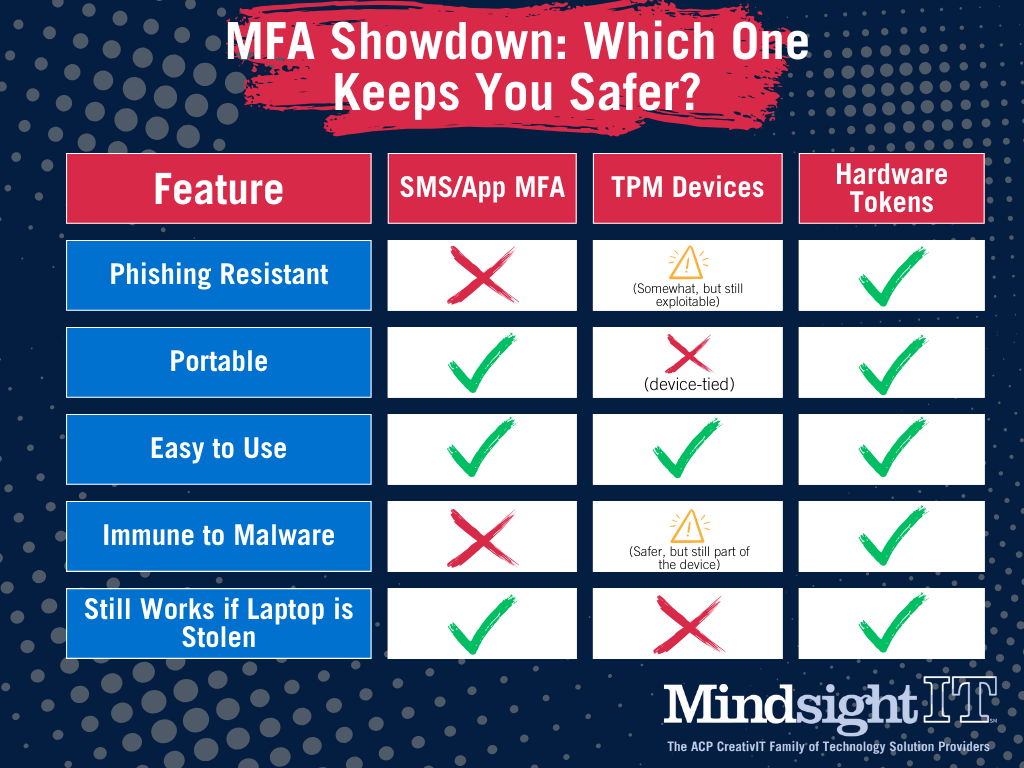
Hardware tokens are small physical devices that add an extra layer of security when logging into an account. They can generate unique, one-time passcodes (OTPs) or use public key cryptography to verify your identity. Unlike software-based authentication methods—like authentication apps or SMS codes—hardware tokens can’t be easily compromised by malware, phishing attacks, or SIM-swapping scams.
Simply put: if a hacker steals your password, they still can’t access your account without the physical hardware token. That’s a game-changer.
Why Hardware Tokens Are a Smart Move for Businesses
- They Offer the Strongest Protection
Phishing attacks trick users into giving up login credentials, but with hardware tokens, stolen passwords are useless. Attackers would need the actual, physical token to get into an account. That’s a huge advantage over SMS or app-based authentication, which can be intercepted. - They’re Easy to Use
Some people hesitate to adopt new security tools because they think they’ll be complicated. But hardware tokens are actually incredibly simple—you just plug them into a USB port or tap them against a compatible reader. No extra codes, no hassle. - They Save Money in the Long Run
Yes, there’s an upfront cost to buying tokens, but compare that to the cost of a data breach—ransomware payments, legal fees, regulatory fines, lost customers… it adds up fast. Investing in hardware tokens is a small price to pay for major protection. - They Help with Compliance
Many industries—like finance, healthcare, and legal services—have strict regulations around cybersecurity. Hardware tokens help businesses stay compliant, reducing the risk of hefty fines and reputational damage.
But What About TPM-Enabled Devices?
Good question! Some businesses rely on Trusted Platform Module (TPM) technology for security. TPM chips are built directly into devices and help with encryption, secure boot, and authentication.
So, why not just use TPM instead of hardware tokens? Here’s the key difference:
- TPM is tied to the device. If someone steals your laptop or gains remote access to your system, they could potentially exploit TPM-based authentication.
- Hardware tokens are independent and portable. If an attacker gets your password, they still need the physical token to log in—no matter what device they’re using.
TPM is a great security feature, but it’s not a substitute for strong, independent authentication like hardware tokens.
How an MSP Can Help with Implementation
Adopting hardware tokens doesn’t have to be a headache. A Managed Services Provider (MSP) can make the process seamless by handling everything from setup to long-term support. Here’s what an MSP can do for you:
Assess Your Security Needs
- Identify your company’s biggest vulnerabilities and compliance requirements.
- Recommend the right hardware token solution based on your business size and risk level.
Procure and Deploy Tokens
- Source and distribute tokens efficiently.
- Integrate them with your existing Identity and Access Management (IAM) system.
Train Your Employees
- Provide easy-to-understand training sessions so your team knows how to use the tokens.
- Educate employees on best practices for secure authentication.
Provide Ongoing Support
- Monitor authentication security.
- Replace lost or stolen tokens.
- Ensure continued compliance with industry regulations.
Okay, But What’s the Catch? (A Few Token Truths)
Look, hardware tokens are awesome—but they’re not magical unicorns. Like anything else, they come with a few quirks:
- They Can Be Lost (Because… Humans)
We’ve all misplaced our keys, phones, and that one sock. Tokens are no different. If someone loses theirs, it’s a mild panic moment—but easily fixable. - They Cost a Bit Upfront
Yep, they’re not free. But neither is a data breach. Think of it like buying locks for your doors—you don’t skip that just to save a few bucks. - Not Everyone Loves Change
Some folks will grumble about having to carry “yet another thing.” But with a little guidance and maybe a coffee bribe, they’ll get on board. - They Need Some Babysitting
Someone’s got to keep track of who has what, manage replacements, and make sure no orphaned tokens are floating around. That’s what IT (or your friendly neighborhood MSP) is for.
But What If Someone Loses One?
It happens. Here’s how to handle it without breaking a sweat:
- Step 1: Report it (Bonus points for not waiting three days.)
- Step 2: Deactivate the missing token before anyone shady tries to use it.
- Step 3: Use a backup login method like an authenticator app or temporary access code.
- Step 4: Issue a replacement token and carry on with your (secure) day.
No drama, no data breaches—just a quick swap and you’re back in business.
“If you allow weaker authentication mechanisms as a backup, attackers will exploit them.”
Weaker backup methods, like SMS or email-based codes, can create vulnerabilities if they’re used alongside hardware tokens. If attackers can exploit these, they might bypass MFA entirely. As Matt Cox suggests, “Start with your most privileged accounts and sensitive applications” when implementing hardware tokens. This ensures that your highest-risk access points are well-protected from day one, reducing exposure for your most valuable assets.
For average users, it’s important to layer protections, especially since “you can’t always rely on your user never getting phished.” In these cases, multi-layered defenses—such as behavioral analytics, device trust, or endpoint protection—can provide an additional layer of security beyond just authentication.
To prevent attackers from exploiting weak backup methods, businesses should:
- Limit the use of weaker authentication mechanisms like SMS, ensuring they are only available for emergencies.
- Enforce stronger alternatives, such as authentication apps or biometric verification.
- Regularly audit authentication policies to make sure they’re up to date with current threats.
The key is to prioritize hardware tokens for your most sensitive access points while ensuring other layers of security protect the rest—because even the best MFA system can’t guard against every possible phishing attack on its own.
The Bottom Line: It’s Time to Strengthen Your Authentication Game
Cyber threats aren’t slowing down, and businesses—especially SMBs—need stronger authentication methods to stay safe. Hardware tokens are one of the most secure ways to protect against phishing, SIM-swapping, and credential theft.
About Mindsight
Mindsight delivers enterprise managed services and technology solutions to the mid-market across a variety of industries including manufacturing, financial services, government, education – just to name a few. Our solution architects and engineers are 100% expert-level and work as an extension of your IT team. Mindsight is headquartered in Downers Grove, IL, a suburb of Chicago.
Mindsight is part of the ACP CreativIT Family of Technology Solution Providers

