June 16, 2020 by Siobhan Climer and Mishaal Khan
The rise in cyberattacks across the globe is unmatched. The 2019 Hiscox Cyber Reading Readiness Report found that 61% of firms suffered a cyberattack in 2018-2019, an increase from 41% of the previous period.
COVID-19 has only exacerbated the behavior of cyber criminals. Recent reports indicate a 238% increase in cybersecurity attacks related to coronavirus specifically targeting banks and financial institutions.
The role of cybersecurity experts, who help defend and test the organization’s network, are more important than ever before. Many institutions are using virtual CISOs or outside cybersecurity analysts to support the endeavors and fortify security controls.
46% Of Companies Report Cybersecurity Attacks During Covid-19 Crisis: A Cybersecurity Report
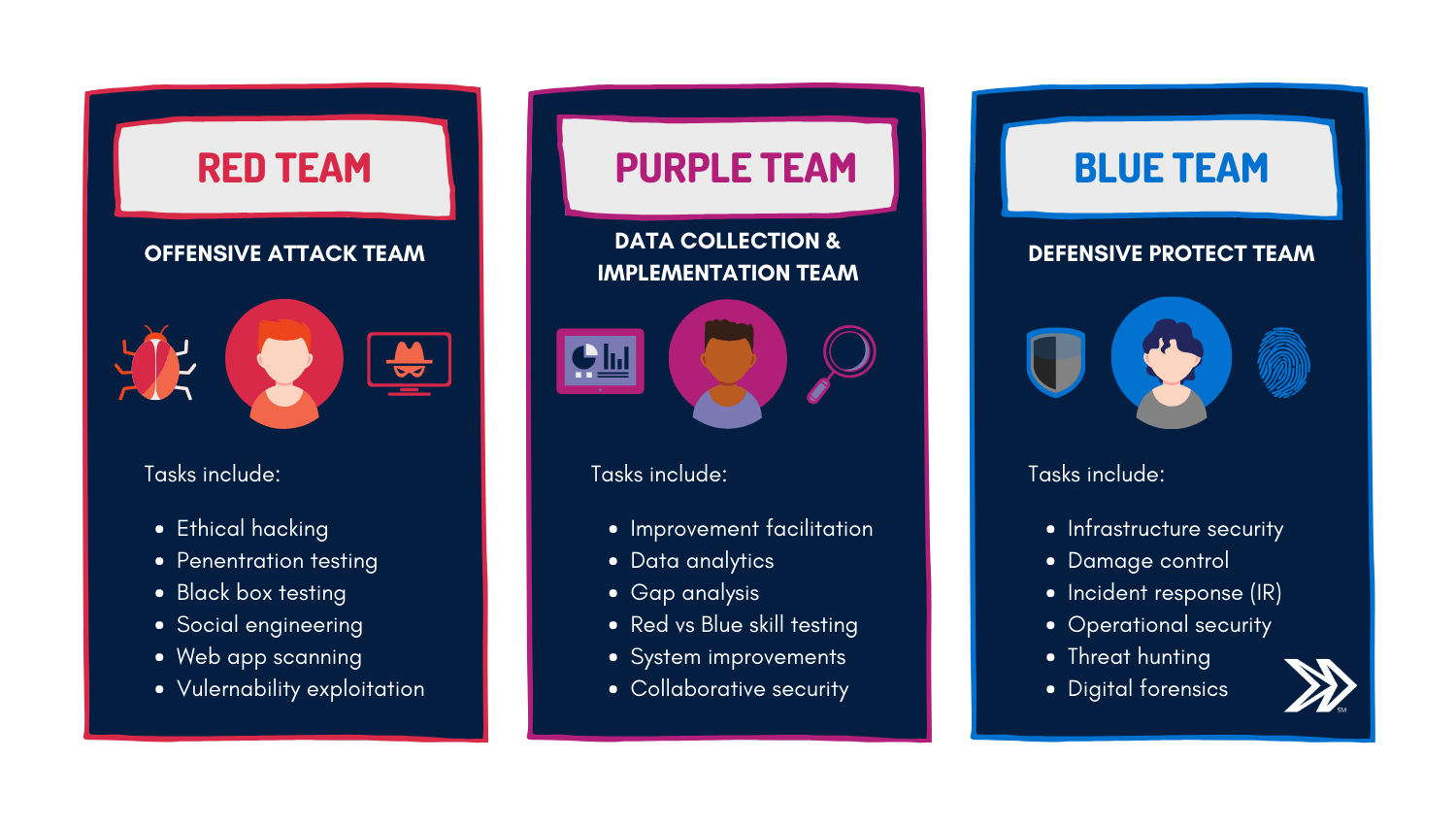
What Is Red Team Vs Blue Team?
If you yourself are from the cybersecurity sector or are familiar with cybersecurity practices, you have likely come across Red Team vs Blue Team language. These names simply apply to the different facets of cybersecurity roles in a single organization.
These delineations refer to a comprehensive offensive and defensive approach to security. The idea is that you need to continually test your cybersecurity controls: from both sides of the network.
In addition to Red Team vs Blue Team, there is also another category: the Purple Team. The Purple Team is, unsurprisingly, the joining of the insights from Red and Blue.
It’s not really Red Team Vs Blue Team; although, these personas often enjoy the competitive rivalry. In essence, by utilizing Red Team AND Blue Team AND Purple Team skillsets, an organization better prepares itself for the inevitable threat of a real cyber attack.
Who Are These Cybersecurity Specialists?
Cybersecurity experts walk a wide road; many do not come from traditional technical backgrounds. Jeff Lanza, a former FBI agent, specializing in cybersecurity operations, collaborated with Mindsight for a recent presentation. He shared that many cybersecurity analysts are former artists or journalists, human resource officers or writers.
Cybersecurity specialists – the folks that join Red Team Vs Blue Team groups and help strengthen an organizations’ defenses – are empathetic, creative, and action-oriented. They find new solutions to ever-evolving challenges. These ethical hackers and digital forensic investigators also have numerous certifications, including:
- Certified Ethical Hacker (CEH)
- CompTIA Security+
- Certified Information System Security Professional (CISSP)
- Certified Information Security Manager (CISM)
- Certified Information Systems Auditor (CISA)
- NIST Cybersecurity Framework (NCSF)
- Certified Cloud Security Professional (CCSP)
- Computer Hacking Forensic Investigator (CHFI)
- Cisco Certified Network Associate (CCNA) Security
Credentials and certificates only tell part of the story, though. Your next attacker does not need a certification to penetrate your network; your network specialists may not need one either.
Test Out Your Cybersecurity Skills At The Next Threat-Hunting Workshop
Mindsight is collaborating with Cisco to launch a Threat Hunting Workshop on June 24th. Join us to develop your skills and test your abilities. In this 4-hour workshop, you will learn the best practices for threat hunting, be taught how to incorporate threat hunting into your daily workflow, and get hands-on with four real-world scenarios.
The Scenarios: Learning Red Team Vs Blue Team Tactics
OLYMPIC DESTROYER (25-40 MINUTES) [CTR/AMP/TG]
Your CIO read about a recent threat “Olympic Destroyer”. Concerned that other threat actors may be able to reuse this malware, the CIO is asking if this threat is being blocked or if we need to update to be protected.
APT 29 (60-75 MINUTES) [CTR/AMP]
The FBI alerted your CIO that a hacking group, is increasing the number of attacks on your industry. How will you determine what their tactics, techniques, and procedures are? How do you find if any evidence is in your environment?
FISH THE PHISH (30-45 MINUTES) [CTR/SMA]
One of our IT analysts noticed a phishing domain that was caught by Umbrella. We have decided to investigate further in our environment to see if we can determine the source of the offending URL. Unfortunately, we have not deployed AMP for Endpoints to this user’s computer, so we don’t have visibility on his machine. We were able to identify the specific link by looking at the user’s browser history, but unfortunately, the user has no recollection of where the link came from. Now we will investigate to determine the source and to see if we can identify any further steps to prevent this in the future!
VPN FILTER (30-45) [CTR/UMB/INV]
The CIO saw a Twitter post mentioning a threat called “VPNFilter” that has infected over half a million routers worldwide. While none of our corporate routers should be affected, the CIO wants to know if there are any infected “Shadow IT” devices connected to our network and if so, if our security products are blocking this threat or not.
The Tools: How To Protect And Defend A Network
CISCO THREAT RESPONSE
A cloud-based research tool which automates integrations across Cisco Security products and threat intelligence sources.
AMP FOR ENDPOINTS
A cloud-based endpoint protection platform (EPP) and endpoint detection and response (EDR) software, providing a total endpoint protection solution.
THREAT GRID
Cloud-based analysis tool combining advanced sandboxing with threat intelligence built into one unified solution.
EMAIL SECURITY
Keep your cloud-based email safe and productive by stopping phishing, spoofing, business email compromise and other common cyber threats.
Like what you read?
Contact us today to discuss red team vs blue team and cybersecurity expertise.
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer writes about technology trends in education, healthcare, and business. With over a decade of experience communicating complex concepts around everything from cybersecurity to neuroscience, Siobhan is an expert at breaking down technical and scientific principles so that everyone takes away valuable insights. When she’s not writing tech, she’s reading and writing fantasy, hiking, and exploring the world with her twin daughters. Find her on twitter @techtalksio.