October 17, 2019 by Siobhan Climer and Mishaal Khan
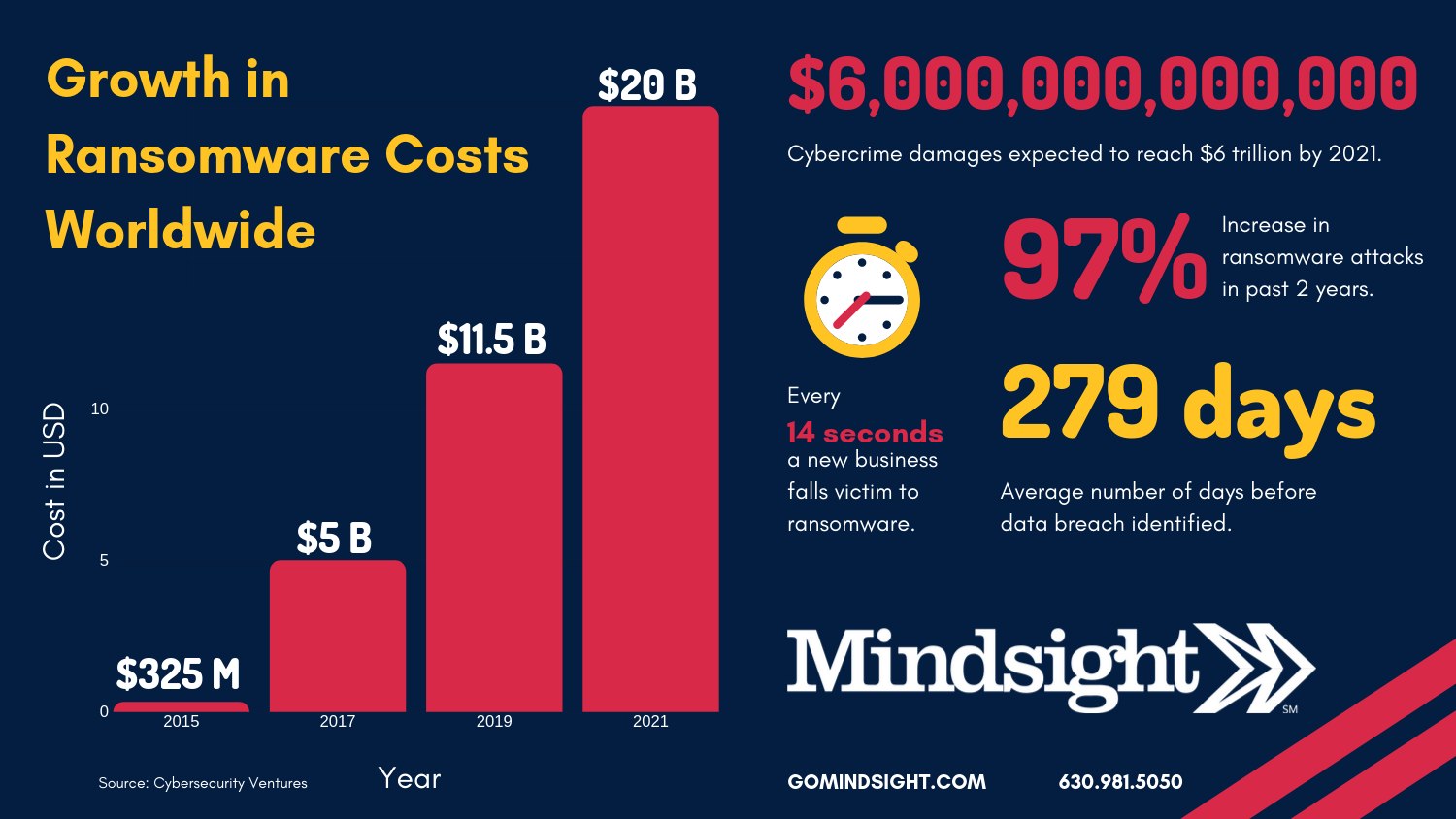
According to Crowdstrike’s 2019 Global Threat Report: Adversary Tradecraft and the Importance of Speed, “the most prominent trend in eCrime for 2018 was the continued rise of ‘Big Game Hunting,’ which combines targeted, intrusion-style TTPs with the deployment of ransomware across a large organization, all in pursuit of a bigger financial payoff.”
The report goes on to depict a growing ransomware-as-a-service (RaaS) industry that includes several named entities, such as GandCrab and Emotet. These specific adversarial operations target businesses and individuals of any size and offer professional malware distribution services.
Rise In Ransomware Targets Changing
While 2017 was the year of high-profile well-known ransomware operations – namely, WannaCry and NotPetya – 2018, and now 2019, have seen a distinct rise in ransomware and cybercrime attacks.
What’s interesting is the rise of ransomware attacks among schools, local governments, towns, villages, and small healthcare clinics. A September report by CBS News found that over 70% of ransomware attacks in the first half of 2019 targeted cities and towns. In August, 22 Texas cities were targeted as a joint cyber-assault, identified by the FBI as a “single threat actor”.
Hospitals, too, have become a vulnerable target for ransomware attacks. Two healthcare providers in 2019 have permanently closed, and others have experienced significant downtime. In fact, almost 500 providers have been victims of ransomware this year so far.
Despite the rise in ransomware attacks, the FBI continues to urge victims to not pay ransoms.
What Businesses Can To Protect Against Ransomware
Ransomware requires a complex, layered approach to security. There are three categories of cybersecurity that businesses must undertake to ensure they are protected against ransomware threats: prevention, detection, and response.
Proactive Cybersecurity
Prevention relies on proactive security measures that protect valuable, mission-critical data, deter cybercriminal activity, ensure the security of the weak human layer, and create redundancy through disaster recovery programming, so that should an attack occur, backups are in place to hasten operability.
Disaster recovery planning is essential in proactively securing yourself against ransomware. By having backups of your essential data, cybercriminals lose the leverage they would otherwise hold via ransomware.
Some examples of preventative measures:
- Firewalls
- MFA
- DNS Security
- Email/Spam Filtering
- Security Awareness Training
Detecting Malicious Activity
Threat actors evolve every day, which is why even hardened security architectures have exploitable vulnerabilities. That is why it is important to have strong monitoring and detection capabilities in place. Cybercriminals often infiltrate and lurk, maximizing the damage they do to your business before demanding ransom. By ensuring you have detection tools in place, you can reduce the damage and risk to your business.
Some examples of detection tools:
- SIEM/SOC
- Endpoint Detection
- Identity Access Management
Responding To An Attack
If your company falls victim to ransomware, the best insurance against damage to the business are secure and tested backups. By integrating cybersecurity with disaster recovery programming, you can ensure that should your files and critical data fall into the hands of cybercriminals, you retain access to the data and minimize damages.
Once an attack happens – just like any mistake – it is key to learn from it. Retaining digital forensics and incident response can help you identify threats and develop a more robust security posture to protect against future incidents.
Some examples of cybersecurity response protocols:
- Incidence Response
- Security Controls Hardening
- Digital Forensics
Mindsight Knows From Experience
We are often contacted by organizations that are victims of ransomware. While we are unable to amend the damage that has been done, we have helped businesses harden their security postures and implement detection and prevention mechanisms to deter and minimize the risk of future attacks.
Want to know more about our security offerings? Contact us today to discuss how to protect your business from ransomware. Our team of security experts includes hackers, pentesters, and certified engineers who design and implement validated security solutions, so you know you are protected against the most prevalent threats.
Like what you read?
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.