September 14, 2021 by Siobhan Climer and Mishaal Khan
This article was originally published in June of 2019.
Cybercrime costs are expected to reach $10.5 trillion USD by 2025, up a staggering 15% from a mere $6 trillion in 2020. Despite the lingering beliefs that bad actors are only attacking enterprise organizations, 43% of cyber-attacks target SMBs with 61% of all small and mid-sized businesses reporting at least one cyber attack in the last year.
To better protect yourself from the threat, it is important to understand the phases of a cyber attack and what you and your team can do before, during, and after an attack to deter, remediate, and optimize your security posture.
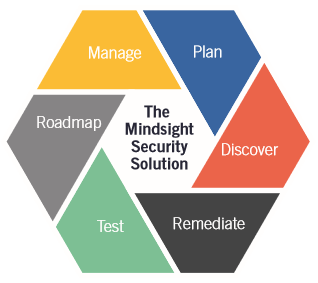
Data Security: Six Links To Success
Given the growing risks, it is more important than ever to build a resilient security framework that protects your business and the data on which it relies. By breaking down the stages of building a resilient security posture into six primary elements, we make the process of developing a hardened security posture less overwhelming.
It is important to note the process is not linear or cyclic. Instead, each link feeds into the security posture and interacts more like a puzzle, and less like a step-by-step program.
The Phases Of A Cyber Attack
Modern network security today is all about balance. In the face of cyber threats, a hands off or “set it and forget it” policy leaves your company wide open to attack. Grip your network too tightly, however, and people won’t be able to do their jobs. Your IT team must find a middle ground. You need security policies to be effective and non-restrictive, especially given the heighted risk associated with remote workers or a hybrid work model.
Before The Attack
 Before the attack is launched, a hacker may perform some reconnaissance on your network. From there, many hackers personalize their malware to capitalize on a discovered weakness.
Before the attack is launched, a hacker may perform some reconnaissance on your network. From there, many hackers personalize their malware to capitalize on a discovered weakness.
The goal of data security before the attack is to create a shell around your network so impenetrable that nothing can go into or out of your network without you knowing what it is and why it’s here. The vast majority of attacks can be stopped before they start, so make sure your outer defenses are up to the challenge.
Many businesses struggle to develop a robust security posture because they use a patchwork of point solution tools that, while valuable as part of a complete data security strategy, provide a false sense of complete security. That is why it is essential to build a true strategy that ensure each layer of data security is complete.
During The Attack
Inevitably, some cyber threats will be capable of breaching the outer defenses of a network. Whether through clever programming or an elaborate phishing attack, your data security strategy cannot end at the edge of the network.
 Deploying an intrusion detection/prevention system (IDPS) to identify, contain, and destroy malicious files on your network. Once a threat exposes itself, your IDPS can spring into action and eliminate the malware.
Deploying an intrusion detection/prevention system (IDPS) to identify, contain, and destroy malicious files on your network. Once a threat exposes itself, your IDPS can spring into action and eliminate the malware.
It is important to note that for most organizations, hackers average over 200 days in the network before being detected. That is plenty of time to elevate privileges, exfiltrate data, and deeply impact the business.
After The Attack
After the attack has either run its course or been intercepted by an IDPS system, the work cannot end. If your security strategy doesn’t learn from its mistakes and plug holes in its defenses, the environment is doomed to suffer the same attack again.
Continually monitoring, managing, and testing your security posture is key to protecting your network from future attacks. Taking the information gathered and implementing security awareness training, improving defensive and offensive systems, and refining your security strategy are key at this stage.
Also, consider investing in training to arm network users with the information necessary to avoid social engineering, phishing scams, or even password sophistication. These small moves not only lend a sense of ownership of network security to other areas of the business, but fortify your outer layer of network security.
Talk with our expert security team today to build a security roadmap for your business that protects your data.
Using The Phases Of A Cyber Attack To Build Resilience
Understanding how the different phases of an attack work can help you and your information security team build a strong defensive system. Ensuring the right deterrence factors are in place and that you mitigate risk from the most prevalent threats by using cybersecurity frameworks are key to building a robust hardened security posture ready for today’s threats.
Contact us today to discuss the phases of a cyber attack and your security posture.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Author
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Strengthen Your Security Posture: Start With A Cybersecurity Framework