February 6, 2020 by Siobhan Climer and Mishaal Khan
On January 16, 2020 the National Institute of Standards and Technology (NIST) of the U.S. Department of Commerce released a final version of the NIST Privacy Framework, a tool for improving privacy through enterprise risk management.
NIST is well-known for its Cybersecurity Framework that is based on existing standards, guidelines, and practices for organizations to reduce risk profiles. Although voluntary, cybersecurity frameworks – like the NIST, CIS, ISO 27001/27002, and PCI DSS – have been widely adopted to mitigate risk and improve overall security postures.
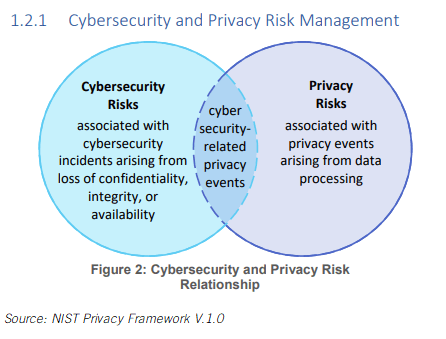
In its release of the Privacy Framework, NIST articulates the difference between Cybersecurity Frameworks and the former. In the figure below, extracted from the Framework, NIST outlines the overlap and difference between cybersecurity risks and privacy risks.
While cybersecurity and privacy overlap, there are discrete differences, which is why NIST – and others – have invested in creating actionable frameworks for IT leaders.
How Does The NIST Privacy Framework Version 1.0 Work?
Data protection and privacy are more important than ever as users continue to exchange information for services. Data is valuable and protecting it is vital to building trust with employees, clients, and other businesses.
The NIST Privacy Framework Version 1.0 is a tool that “helps organizations identify and manage privacy risk to build innovative products and services while protecting individuals’ privacy.”
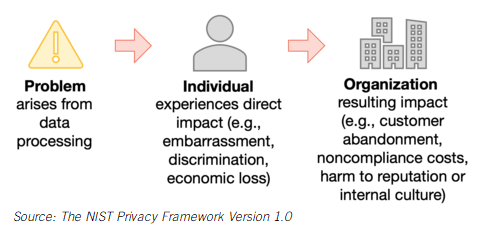
NIST’s approach to is from a data process standpoint, as shown in the Figure below:
The NIST Privacy Framework is composed of three parts: Core, Profiles, and Implementation Tiers. You can read more about these in the actual Framework documents; these elements are primarily used to break down the planning strategy and implementation piece for those looking to implement these standards.
Why Use NIST?
Data privacy matters. In a recent report on the perceptions of consumers around the Internet of Things (IoT), researchers found that while 75% of people distrust the way their data is collected and shared by IoT devices, 72% of people have purchased an IoT device.
 Privacy and convenience often come head to head, and this research brings this conundrum to the forefront.
Privacy and convenience often come head to head, and this research brings this conundrum to the forefront.
“People who say they’re concerned with security will do a lot of very insecure things,” says Robert W. Proctor, Professor of Psychological Sciences at Purdue University.
The NIST Privacy Framework Version 1.0 provides an opportunity for businesses to differentiate themselves and provide protections to users – both internal and external – that they desire but may not be able to fulfill.
Starting the implementation of NIST Privacy Framework now is smart, as your users increase their scrutiny of data privacy and data sharing practices.
How Does NIST Compare To Other Frameworks?
Guidance around data privacy is still limited. The General Data Protection Regulation (GDPR) certainly laid much of the ground work for data privacy compliance, and the release of the California Consumer Protection Act (CCPA) is following suit.
Presently, data privacy regulations are not widespread in the U.S., at least at the Federal level. California, as shown above, New York, Massachusetts, and Minnesota all have individual data privacy laws – and across the U.S. there are more than 600 individual privacy-related laws.
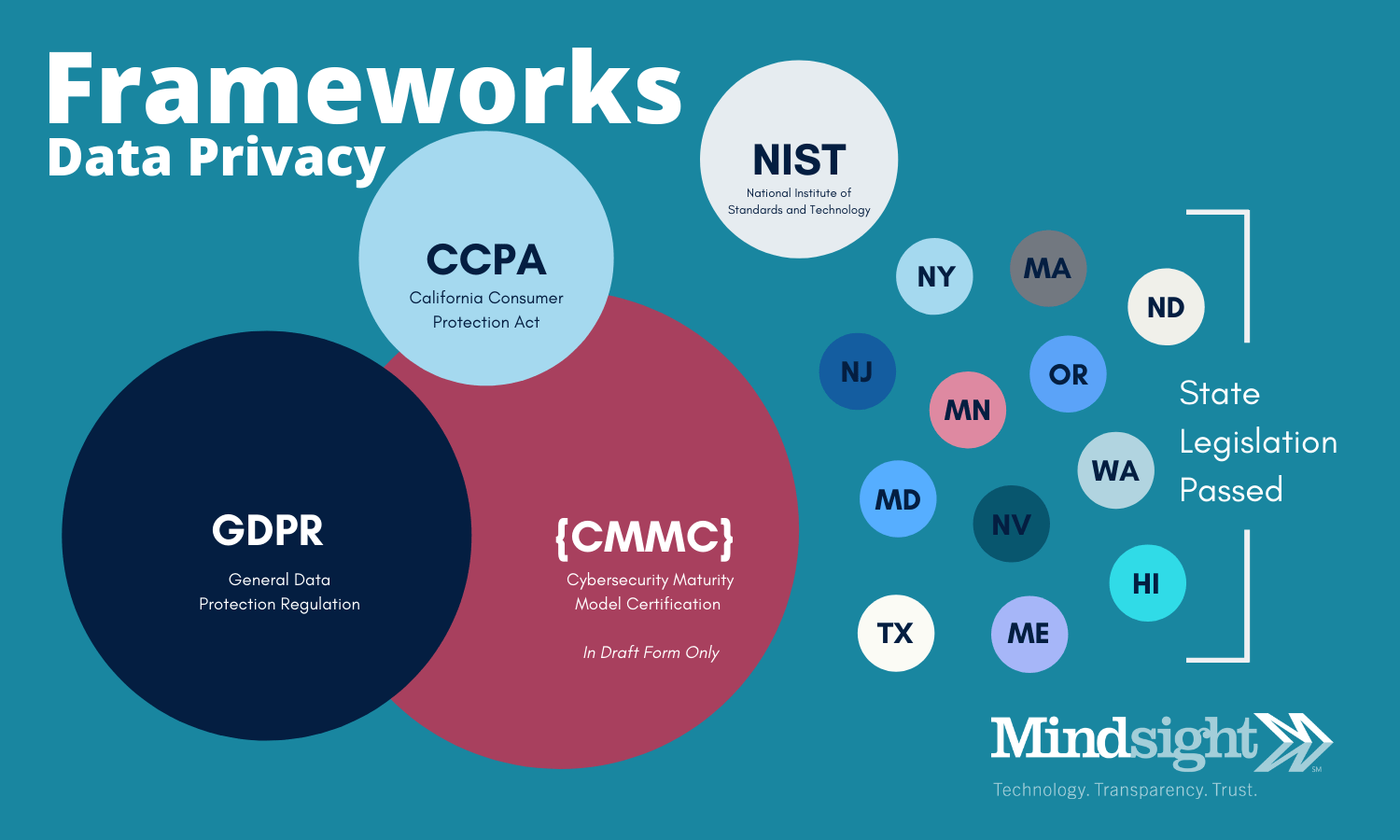
The NIST provides a level of standardization around data privacy. While it is currently voluntary, changes to perceptions around data privacy, data security, and the value of data by consumers and citizens alike will likely power a heightened focus on regulating data.
CMMC – The Next Framework Leader
 The NIST Privacy Framework Version 1.0 and the NIST Cybersecurity Framework Version 1.1 are both executed by the U.S. Commerce Department. This was a logical step towards data security with the increasing use of credit cards and ecommerce.
The NIST Privacy Framework Version 1.0 and the NIST Cybersecurity Framework Version 1.1 are both executed by the U.S. Commerce Department. This was a logical step towards data security with the increasing use of credit cards and ecommerce.
However, data is far more complex, and the risk of ransomware and data breaches is far more than a simple credit card lapse away. This is perhaps part of the reason the Department of Defense is in the process of developing a Cybersecurity Framework called the Cybersecurity Maturity Model Certification (CMMC).
The CMMC will eventually be a cost-effective way for smaller businesses to implement cybersecurity standards, and it will enable certified third party organizations to conduct audits to inform risk.
Security Risk Assessments Build On Cybersecurity Frameworks
Starting on a path towards data security and privacy doesn’t have to be overwhelming. By working with certified cybersecurity practitioners, organizations can assess risk, identify gaps in a security posture, invest in security controls, and protect the integrity of data.
Talk with Mindsight’s cybersecurity experts today to learn how you can get started protecting your organization and the data on which it relies. Our engineers provide complimentary whiteboard sessions to talk at a high-level about what you need and how an organization like Mindsight can help.
Like what you read?
Contact us today to discuss the NIST Privacy Framework Version 1.0.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
Strengthen Your Security Posture: Start With A Cybersecurity Framework