June 30, 2020 by Siobhan Climer and Mishaal Khan
For ages, network engineers and cybersecurity practitioners have called for increased use of network access controls; despite this push, adoption remains sluggish.
Over the last two years, business and IT leaders alike have leaned more heavily into cybersecurity solutions. Rising security issues due to unwanted devices and unauthorized users initiating network breaches, as well as more media attention on data breaches and security, is drawing more attention to network security.
A May 2020 Gartner report found that while NAC vendors are expanding into adjacent markets, implementation of network access controls is growing primarily among the most common use cases: security and risk management around mission-critical data.
While the risk vectors are growing (i.e. IoT, smart metering, connected cars, windmills, medical monitoring, etc.), the basics of cybersecurity are what are drawing IT leaders to implement NAC today.
Network Access Controls & FortiNAC
Bookmark and check out this recorded webinar presented by Mindsight and Fortinet from June 2020 when you have a few minutes. It’s a great overview of the why behind NAC, the vendor landscape, and a review of FortiNAC – Fortinet’s NAC solution.
See Mindsight’s upcoming virtual events and register for relevant presentations.
Why Are Network Access Controls Important For Network Security
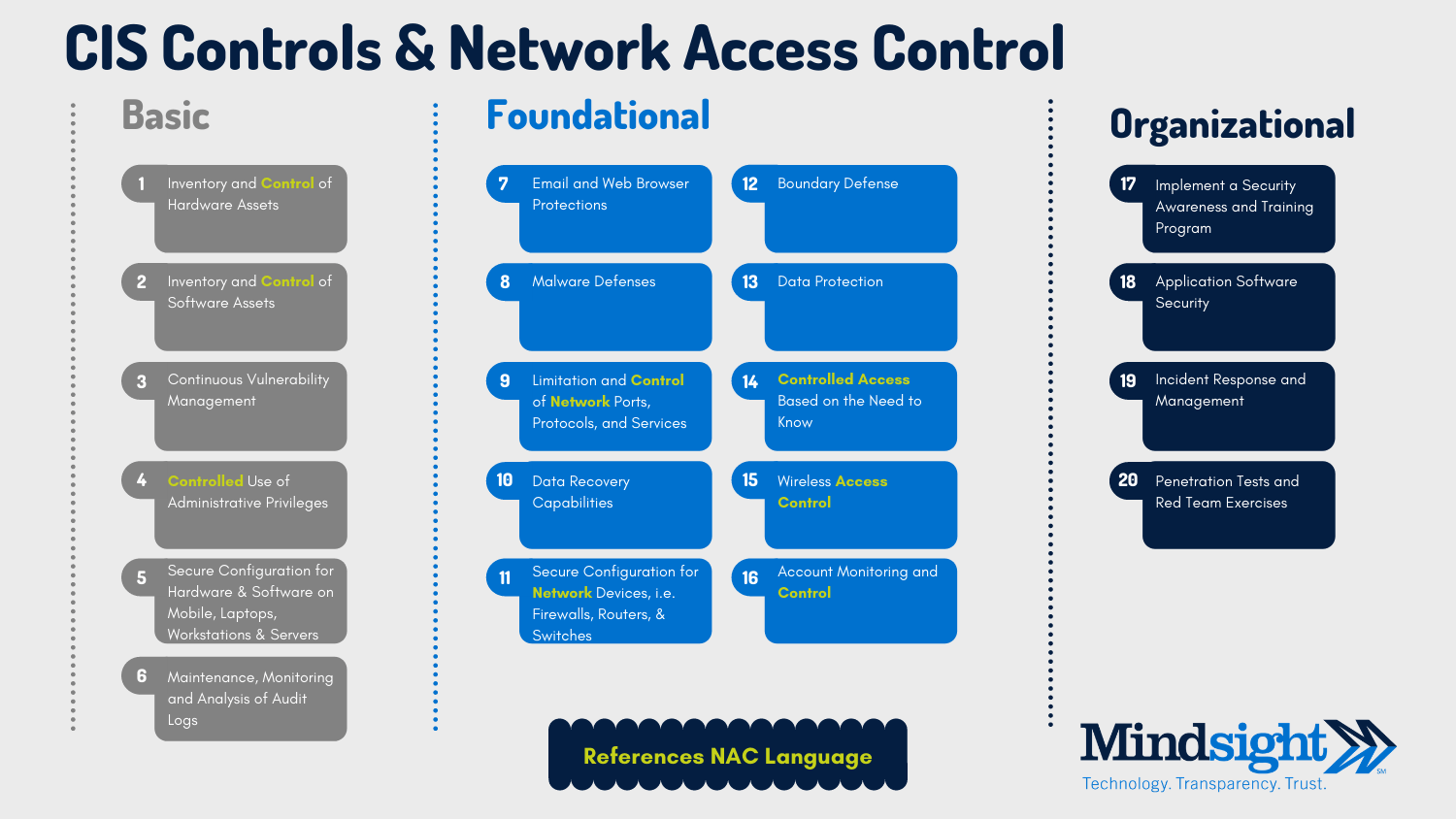
Cybersecurity frameworks provide a structure by which security practitioners can strategically secure their organization. The Center for Internet Security (CIS) and the National Institute of Standards and Technology (NIST) have the two most commonly adopted cybersecurity frameworks businesses choose to use, outside of industry-specific regulations (i.e. HIPAA or PCI DSS).
A quick scan of any of the security frameworks – we used the CIS20 below – shows a great deal of network access control language.
Network access controls are indeed fundamental to the most basic and foundational elements of a security posture, checking the primary components of security compliance framework.
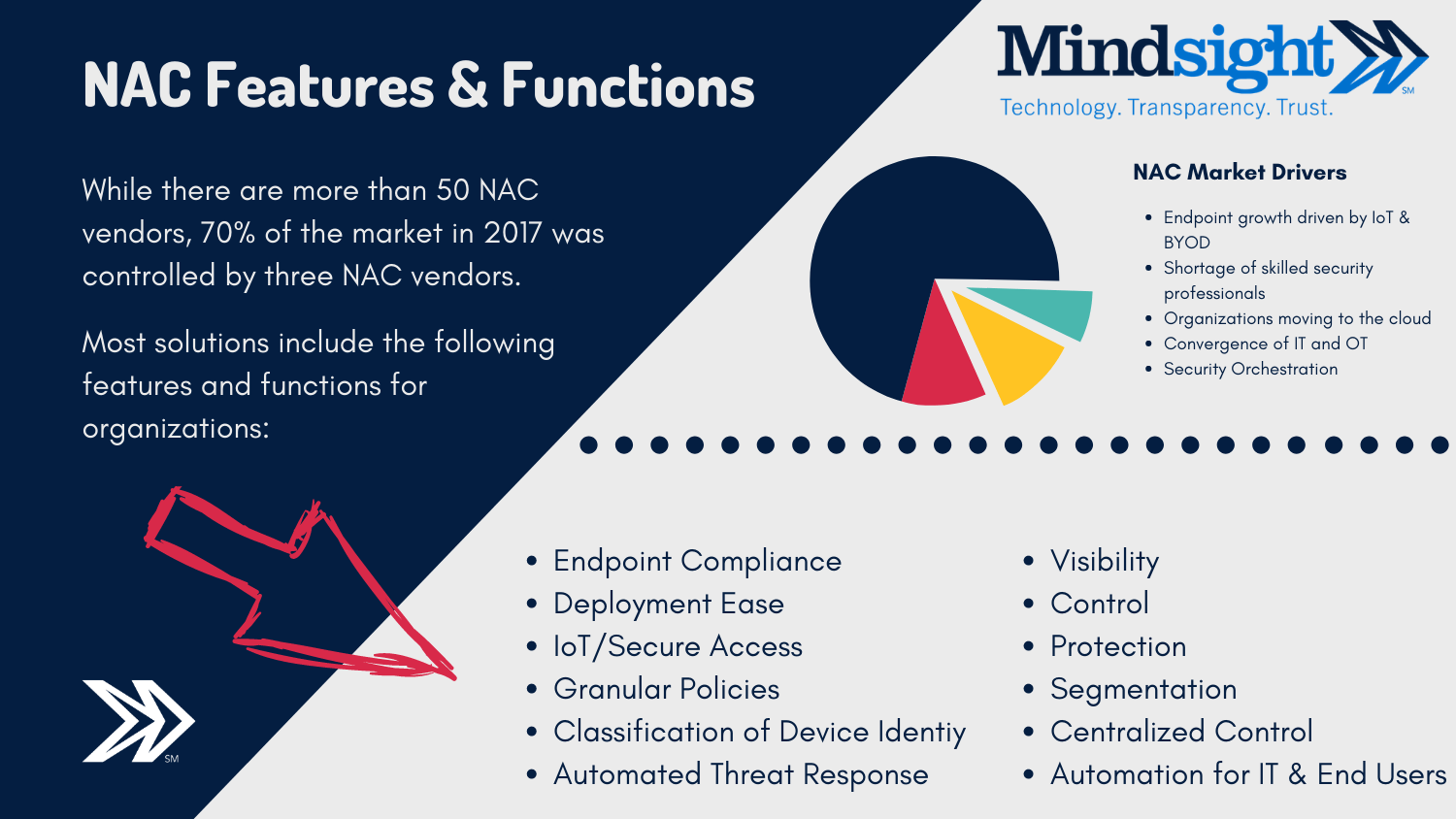
In addition, NAC fulfills multiple functions of endpoint security.
Visibility
How can you protect what you can’t see? You can’t. Visibility is essential to a strong cybersecurity posture. NAC gives you device insight, such as location, posture, and quarantine status.
Control
Once you know what you have, you can control it. With that data in hand, you can create a baseline and observe – and investigate – deviations.
Compliance
NAC covers a multitude of checkboxes for the organization, enforcing many compliance standards and providing a basis for accurate security assessment.
Market Analysis Of Network Access Control Solutions
“Network visibility into endpoints and devices is critical. Every device on a network is a potential attack or reconnaissance point that must be discovered and secured. NAC vendors continue to innovate to meet new usage cases—most notably IoT, Operational Technology(OT), and cloud.”
– Network Access Control Market, Global, Forecast to 2022:
NAC Evolving As Enterprise Networks Expand Beyond Secure Walls
Frost & Sullivan
Emerging trends around IoT, mobility, BYOD, and cloud are the primary drivers of NAC demand, according to the report. In addition to the primary security functions listed above, NAC vendors have an enormous list of features and functions they add on (though, you might not need every feature).
How To Choose A NAC Solution And Get Started
Here are the questions we hear again and again:
- Which solution should I be looking at?
- What sort of scalability do I need?
- What feature set is important to my organization?
Here’s our Buyer’s Checklist – what network access control buyers should consider before making a vendor decision:
- Integration: Does it integrate with your existing infrastructure? If it doesn’t, you’re going to have to buy more gap solutions – leading to a less secure posture.
- Interoperability: Will the solution adjust as your organization changes? How adaptable is it for future infrastructure changes?
- Visibility: Not all solutions provide equal visibility across your business; make sure the solution gives you the right kinds of visibility.
- Enforcement: How much does it enforce?
- Compliance: Does it fulfill my compliance needs?
- Features: This set is almost endless: IoT, DLP, Agent vs Agentless. You likely don’t need all of these features, so identifying which features are critical to your organization is essential.
- Deployment Complexity: The complexity of deployment can vary greatly; you need to understand what will be required and whether you have the assets to deploy.
- Price: It runs the gambit. This is the security and compliance of your network, but you likely don’t need all the features. A partner helps you find the right solution.
- Support: You don’t want a solution that is not supported or relies on community-based support.
Compare Network Access Controls Solutions To Find Your Fit
Not sure where to start? That’s okay. Mindsight’s team can help you assess your needs and find the right solution for your organization.
Contact us today or email jvitro@gomindsight.com directly to see how we can work together.
Like what you read?
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer writes about technology trends in education, healthcare, and business. With over a decade of experience communicating complex concepts around everything from cybersecurity to neuroscience, Siobhan is an expert at breaking down technical and scientific principles so that everyone takes away valuable insights. When she’s not writing tech, she’s reading and writing fantasy, hiking, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
VPN Use Up 53% in 6 Days; Stress On Remote-Access Networks: An Infrastructure Report