January 16, 2020 by Siobhan Climer and Mishaal Khan
The Verizon Data Breach Investigations Report found that “81% of hacking-related breaches leveraged either stolen and/or weak passwords,” and that more than 70% of employees reuse passwords at work.
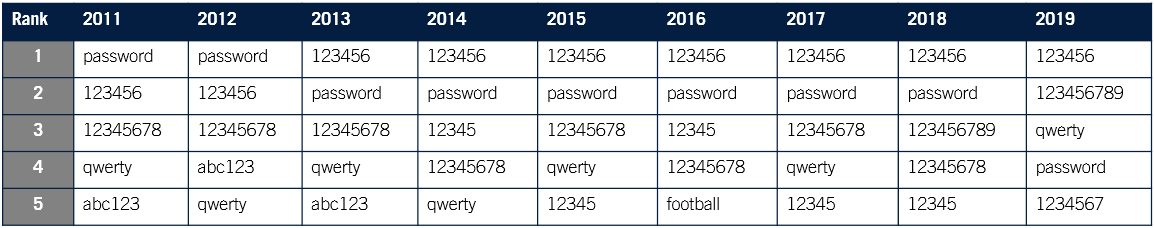
Poor password hygiene is, unfortunately, nothing new. Every year, internet security firm SplashData releases the Worst Passwords List. What is fascinating is how little the list changes year-over-year. ‘password’, ‘123456’, ‘qwerty’ and ‘123456789’ have been in the top 4 for the last nine years. Have we learned nothing?!
While security awareness training is an important element of tackling poor password practices, it still relies on the user to make risk-aware decisions. Multi-factor authentication, on the other hand, helps return control to security practitioners.
What Is Multi-Factor Authentication?
Multi-factor authentication (MFA) is an authentication method that grants access to system users when presented with two or more factors – or pieces of evidence – to an authentication mechanism. Factor types include knowledge, possession, and inherence; in practice, these factors include something you know, something you have, and something you are.
Two-factor authentication (2FA) is considered a subset of MFA and includes two – and only two – authentication factors. Common examples of 2FA include:
- Bank card and pin
- Phone number and SMS verification code
- Bank card and phone call
- Login credentials and device authentication
There are different types of authentication methods, and the list of factors grows every day. The most common authentication factors in use today are:

Knowledge: PINS, user IDs, passwords, answers to challenge questions
Possession: One-time passwords (OTP), tokens, smartcards, digital certificates, device specifics (i.e. cookies, IP addresses)
Inherence: Retinal scans, fingerprints, voice recognition, face scan, typing rhythm
Remember no single factor is secure. It is the combined use of multiple factors that increases the challenge for attackers.
The ‘Good’ Of Multi-Factor Authentication
Compromised passwords and usernames are a dime a dozen on the dark web (actually more like $1.00), so chances are that a cyber criminal already has  some credentials that could be used to access your systems. Whether they use phishing, credential stuffing, or social engineering to gather the remaining missing pieces is anyone’s guess.
some credentials that could be used to access your systems. Whether they use phishing, credential stuffing, or social engineering to gather the remaining missing pieces is anyone’s guess.
Multi-factor authentication adds that additional security layer at your weakest point. By tying access to something other than just a password, you make it that much harder for nefarious actors to engage in an attack on your network.
The Good: Multi-factor authentication:
- Protects sensitive information
- Increases overall security significantly
- Reduces risk surface
- Adds additional security layering
- Helps meet some compliance requirements
The ‘Bad’ Of Multi-Factor Authentication
Despite the hype, multi-factor authentication is not a silver bullet for security. The rise in MFA as a defense mechanism has led to several social engineering and technical attacks by criminals to circumvent the practice, some of which were successful.
 Less than a month after shipping, the Samsung Galaxy S8 had its biometric iris scanner hacked. Voice recognition is also demonstrably penetrable, as are fingerprints. Cyber criminals are also able to imitate device metrics, thereby authenticating via device even without it in hand. Using a combination of email forwarding or SMS programming, these criminals can bypass different factors.
Less than a month after shipping, the Samsung Galaxy S8 had its biometric iris scanner hacked. Voice recognition is also demonstrably penetrable, as are fingerprints. Cyber criminals are also able to imitate device metrics, thereby authenticating via device even without it in hand. Using a combination of email forwarding or SMS programming, these criminals can bypass different factors.
(This all takes work, though. That’s the key to a strong security posture; deter criminals by making the task of infiltrating your systems challenging.)
The Bad: Multi-Factor Authentication
- Harder for users to use
- Potential increases in costs
- Lack of technical expertise for implementation/maintenance
- Absent backup and disaster recovery plan for MFA
- Inconsistent application of MFA
Should You Implement Multi-Factor Authentication?
Yes. One-hundred times yes.
Multi-factor authentication won’t solve your every cybersecurity woe, but it provides another layer to your security posture, targeted directly at the weakest ![]() link: users.
link: users.
If you haven’t yet implemented MFA, that’s okay. In fact, waiting for a solution that minimizes the cons of MFA is smart. Today, there are solutions on the market that are inexpensive to implement and easy to scale.
Find out more about today’s multi-factor authentication solutions by talking with our experts today. Our engineers provide complimentary 1:1 whiteboard sessions – in person or virtually – to talk about your specific environment and the challenges you face. Talk with them today.
Like what you read?
Contact us today to discuss multifactor authentication.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.