Updated January 28, 2020 by Siobhan Climer
Security is an ever-growing concern for modern businesses. In the wake of high-profile hacks of Fortune 500 companies over the last few years, it has never been more important to keep your environment secure and reduce your risk of a breach.
![]() A slew of products, strategies, and solutions from a wide range of developers have come on the market to intercept these threats. Your environment needs a firewall, intrusion detection/prevention systems, additional forms of monitoring, and more.
A slew of products, strategies, and solutions from a wide range of developers have come on the market to intercept these threats. Your environment needs a firewall, intrusion detection/prevention systems, additional forms of monitoring, and more.
Even still, the wrong click from any one of your users can invite the worst the internet has to offer into your corporate network. Command and control attacks in particular have proven to be a difficult challenge for security professionals to prevent because they circumvent many of our standard security strategies.
Command and Control Attacks in a Nutshell
The premise of a command and control attack is fairly simple. Security appliances like firewalls and intrusion detection and prevention systems (IDPS) are designed to recognize and thwart malicious activity or files.

However, a command and control attack is more devious than the standard threat. A command and control file isn’t malicious at first. Acting as a Trojan horse, the file is deemed harmless by your firewall and permitted entry.
Once inside, it lies dormant for a certain time period or until it is triggered. Then, the file reaches out to a malicious domain and downloads all of its harmful data. Suddenly, your business network is infected, and it is already too late to stop the attack.
Command and Control Attack Steps:
- Enters through firewall
- Lies dormant
- Reaches out to malicious domain to download malware
- Infects your network from the inside
Command and control attacks are so dangerous, because the interior of a network is, in most cases, less protected than the edge. The attack dodges your defenses where they are strongest and takes advantage of the holes in your security strategy.
However, Cisco Umbrella has found a way to monitor and prevent these attacks from successfully impacting your network. Umbrella accomplishes this by merging itself with OpenDNS and serving as your network’s DNS regulator.
What is Cisco Umbrella?
Cisco Umbrella is a security service previously known as OpenDNS. It replaces the standard DNS system with Umbrella’s ever-growing data base of known malicious URLs. Normally when a user enters a URL in their web browser, the browser will send that information to a local DNS Server that has catalogued the URL, with a corresponding IP address.
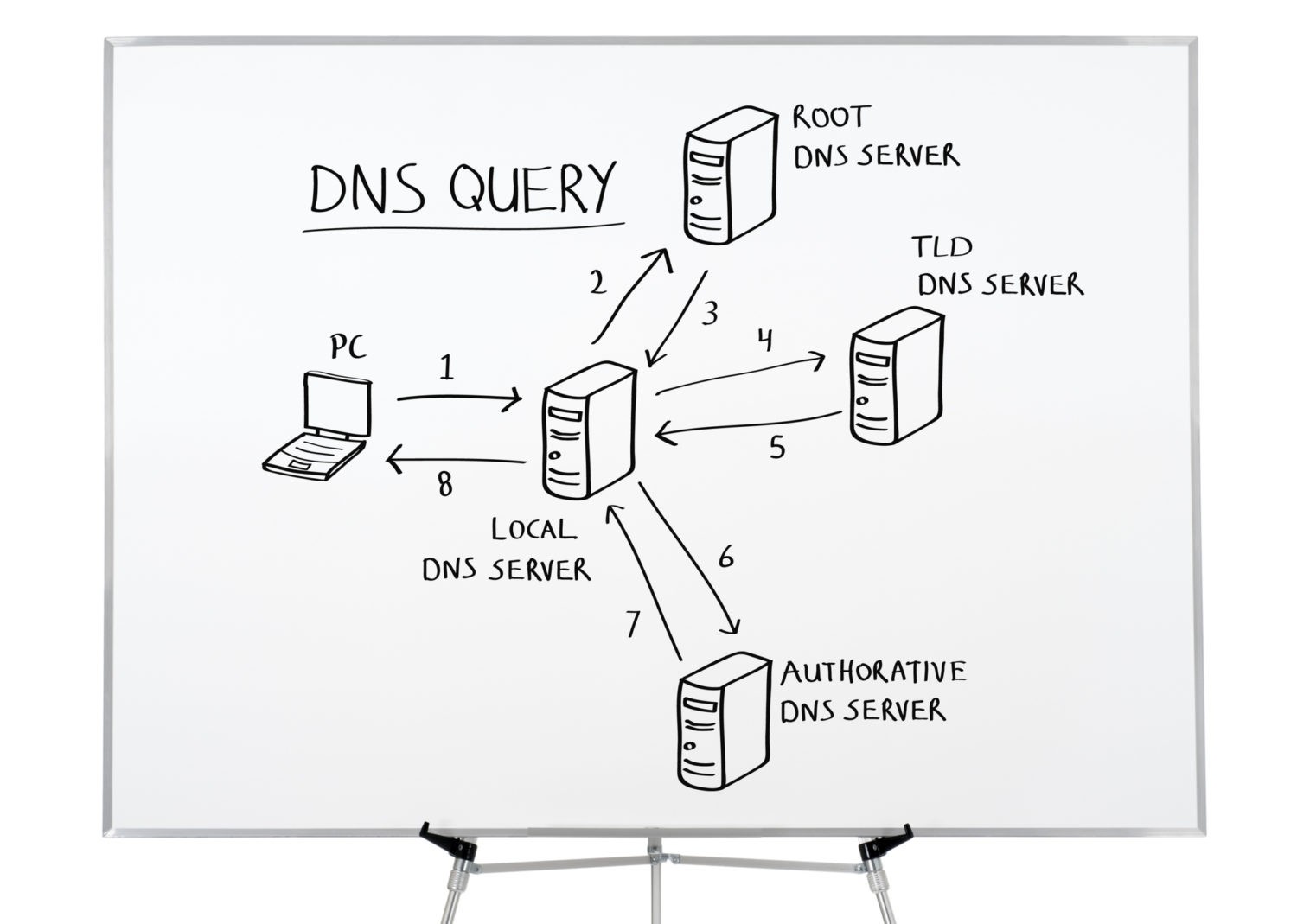
The DNS server then routes the web browser to the correct IP address and requests data. On the user’s end, they will have successfully visited a website. Umbrella takes over these responsibilities, and by doing so, provides a clever level of security to your network.
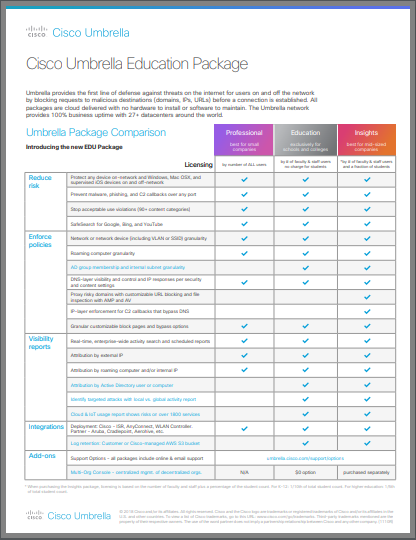
Learn more about pricing for Cisco Umbrella as it relates specifically to schools:
Cisco Umbrella and the DNS System
Cisco Umbrella is cleverly designed to prevent these sorts of attacks by merging with your DNS regulator. Companies with Cisco Umbrella simply modify their active directory to use Umbrella as their DNS regulator instead.
![]()
Umbrella itself includes an enormous directory of innocent, suspicious, and malicious domains that is constantly growing. Now, whenever a user on your network sends a request to the internet, Umbrella compares the requested domain to their directory of suspicious domains. If the domain is known to be malicious, the traffic is immediately blocked.
This is a useful tool for preventing network users from unknowingly (or knowingly) visiting malicious domains or falling victim to phishing attacks. If they click that suspicious link in an email, Umbrella will stop the traffic before it can damage the network.
For command and control attacks, the process is very similar. When that dormant file awakens and attempts to download their virus payload, Umbrella gets in the way, because that file still needs to access a domain and therefore must navigate through the DNS system and Umbrella.
An Obvious Workaround and Umbrella‘s Response
 Any IT professional is going to look at this product and see an obvious workaround. If any traffic running through the DNS system must also pass through Umbrella, why not just hard code the IP address into your command and control attack and circumvent the whole system? If the virus uses a direct IP instead of a domain, it can go straight to the source and avoid Umbrella altogether.
Any IT professional is going to look at this product and see an obvious workaround. If any traffic running through the DNS system must also pass through Umbrella, why not just hard code the IP address into your command and control attack and circumvent the whole system? If the virus uses a direct IP instead of a domain, it can go straight to the source and avoid Umbrella altogether.
Boom, the whole security strategy is nullified.
Cisco recognized this and put in an added measure. If you purchase the Insights or Platform packages of Cisco Umbrella, you’ll have an advanced feature. Whenever a request is made to a direct IP, Umbrella acts. It locks down the request, encrypts the data and first sends it through Umbrella’s directory. After Umbrella clears it, the data can then move on to its desired location.
Through this process, Umbrella can stop almost every form of command and control attack.
![]()
Managing Mobility
Employee mobility is a concern for security professionals. The corporate network can have as much protection as it wants, but if a laptop or smartphone picks up malicious files at a coffee shop, airport, or at home, it can find its way onto the corporate network next time that device is in the office.
Umbrella has a solution for this issue. Since Umbrella is cloud hosted, a small setting change on the device will route all traffic, regardless of location, through Umbrella’s directory. IT simply needs to mandate this setting change in all business devices and personal devices intending to access the network.
One Step Ahead of Malicious Files
![]() Data security is an ongoing arms race. As hackers and cyber threats become more sophisticated, so too must our data security tools. That’s why ongoing services like Cisco Umbrella are so useful. Instead of waiting for a patch and presenting an opportunity for hackers to exploit outdated security appliances, Cisco Umbrella is in the cloud and always updated.
Data security is an ongoing arms race. As hackers and cyber threats become more sophisticated, so too must our data security tools. That’s why ongoing services like Cisco Umbrella are so useful. Instead of waiting for a patch and presenting an opportunity for hackers to exploit outdated security appliances, Cisco Umbrella is in the cloud and always updated.
If a new malicious domain is found, Umbrella can blacklist it that instant and prevent their users around the world from accessing it. That’s the kind of speed and power data security needs to protect their environment.
With Cisco Umbrella, your environment can stay one step ahead of malicious files and stop attacks before they start.
Reach Out to Us to Set Up a Proof of Concept
Cisco Umbrella gives you unmatched visibility into your network. But you don’t have to take our word for it. Mindsight’s experts can walk you through setting up a proof of concept so you can see, in real-time, how Cisco Umbrella can protect your network. Sign up now to get in touch with one of our experts.
Like what you read?
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
Protect K-12 Student Users In The Cloud: Cisco’s CloudLock And Umbrella Combo