July 3, 2018 by Siobhan Climer
Yahoo? Equifax? Ashley Madison? Exactis? Cyber attacks abound in the digital realm, evolving every day to become more and more sophisticated. Why? Well, although shadowy figures in hoods infiltrating networks to steal information for profit are a real thing, so are governments who use cyber-warfare to undermine dissenting views or other nation states. Hackers get a tidy sum for an electronic health record (EHR), while nations may be able to sway voters, discourse, or ideology.
 In 2015, North Korea was implicated in an attack on Sony Pictures, with the intention of disrupting the release of The Interview. In 2014, Russia was blamed for Turla, (aka ‘Uroburos’ or ‘Snake’), which infected Western nations. Just this year, the now infamous Cambridge Analytica data leak occurred. The details around the Cambridge Analytica scandal hounding Facebook are still hazy, but over 50 million user profiles were available to the firm, while only 270,000 consented to their data being used for academic research.
In 2015, North Korea was implicated in an attack on Sony Pictures, with the intention of disrupting the release of The Interview. In 2014, Russia was blamed for Turla, (aka ‘Uroburos’ or ‘Snake’), which infected Western nations. Just this year, the now infamous Cambridge Analytica data leak occurred. The details around the Cambridge Analytica scandal hounding Facebook are still hazy, but over 50 million user profiles were available to the firm, while only 270,000 consented to their data being used for academic research.
While these recent cyber attacks and data breaches are fresh in the mind, we began to wonder when was the first cyber attack? What kinds of cyber attacks are there? What can you do to prevent your business from being breached before, during, and after an attack. By understanding the history of cyber attacks, we can begin to combat this growing threat to the security of our personal identity information (PII).
Types of Cyber Attacks
Unpatched Software – Vulnerabilities in software are discovered every day, and those software providers develop and release patches to cover any holes. Patching your software is an important – but often over-looked – step to protecting your network. The programs you use to easily browse the web, like Java, Adobe Reader, and Adobe Flash are frequently left unpatched.
 Phishing Attacks – Where most cyber-threats exploit vulnerabilities in a computer’s system, phishing attacks exploit our own gullibility and trusting nature. A phishing attack is when a hacker fishes for information, through a text message, email, or even a printed letter sent to a user from what appears to be a reputable source. The correspondence will instruct the user to submit personal information like account numbers, passwords, usernames, or similar data to the phisher. From there, the hacker can retrieve all the information they want. Check out our two-part guide on how to spot a phishing attack: Part 1 and Part 2.
Phishing Attacks – Where most cyber-threats exploit vulnerabilities in a computer’s system, phishing attacks exploit our own gullibility and trusting nature. A phishing attack is when a hacker fishes for information, through a text message, email, or even a printed letter sent to a user from what appears to be a reputable source. The correspondence will instruct the user to submit personal information like account numbers, passwords, usernames, or similar data to the phisher. From there, the hacker can retrieve all the information they want. Check out our two-part guide on how to spot a phishing attack: Part 1 and Part 2.
Network-traveling Worms – Like its hermaphroditic namesake, a computer worm copies itself onto other computers, causing network overloads or delivering a malicious virus payload. These viruses might delete files, encrypt files in a ransomware attack, or steal valuable information, like passwords. Most commonly, worms deliver a payload that installs a backdoor, enabling the computer to be controlled as a botnet by hackers.
DDoS Attacks – DDoS, or dedicated denial-of-service, attacks drive what the network recognizes as legitimate traffic through your servers, overloading the system and causing significant slow-downs, or even outages. DDoS attacks are often used to silence businesses or overwhelm a financial institution.
Trojan Horses – Named from the Greek fable, a Trojan Horse cyber-threat (or Trojan) works similarly to Odysseus’s ploy. Instead of being a threat in-and-of itself, a Trojan appears initially as an innocuous file often attached to an email as an image. Once inside the system, it remains hidden while it downloads the real threats to the computer like spyware, malware, or other viruses. The infected computer doesn’t even know it has been infected.
Advanced Persistent Threats (APT) – These threats are designed to steal intellectual property. By using phishing tactics or specific Trojans, APTs enter a system and compromise an entire network in a very short amount of time. Hackers are no longer lone wolves, but instead work in sophisticated groups looking to steal assets and sell them to competitors or ransom them back to the victimized company.
A History Of Cyber Attacks
1988 – The First: The Morris Worm
The first cyber attack began with good intentions and ended with unexpected consequences. In 1988, Cornell University graduate student, Robert Tappan Morris, developed a program to assess the size of the internet. The program would crawl the web, install itself on other computers, and then count how many copies it made. Once tallied, the results would indicate the number of computers connected to the internet.
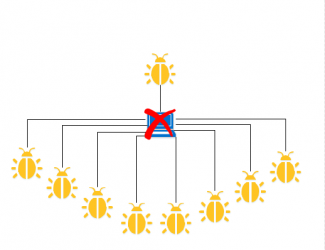 Unfortunately, problems arose for Morris, who struggled to ensure accuracy. Morris made a command that forced the worm to install itself on a computer every one out of seven times, even if the computer claimed it already had the program. With each installation, the infected computers would become further debilitated until they finally crashed. It was the first Distributed Denial of Service (DDoS) attack, and it was entirely by accident.
Unfortunately, problems arose for Morris, who struggled to ensure accuracy. Morris made a command that forced the worm to install itself on a computer every one out of seven times, even if the computer claimed it already had the program. With each installation, the infected computers would become further debilitated until they finally crashed. It was the first Distributed Denial of Service (DDoS) attack, and it was entirely by accident.
In total, the worm damaged approximately 6,000 computers (10% of the entire internet at the time). The estimated cost of repairing the effects of the worm range between $100,000 and $1 million or between $201,000 and $2.9 million adjusted for inflation. Morris was charged with the violation of the Computer Fraud and Abuse Act, and his sentence included fines, plus three years of probation and community service.
1995 – LA KIIS FM Porsche
In an amusing cyber attack, Kevin Poulsen used his hacking ability to cheat in a radio contest. LA KIIS FM was giving away a Porsche to the 102nd caller, and Poulsen naturally wanted to win. He infiltrated the phone network to block their ability to receive calls, so Poulsen was assured the 102nd caller slot. Despite winning the Porsche, he was eventually caught and sentenced to five years in prison.
In 2002, the internet was hit directly, marking a first in the history of cyber attacks. By targeting the thirteen Domain Name System (DNS) root servers, a DDoS attack assaulted the entire internet for an hour. While most users were unaffected, the DDoS attack could have shut down the internet if it had been sustained for a longer period. Up until this point there had never been such a sophisticated cyber attack launched on such a large scale.
2008 – The Church of Scientology
A hacker group known as Anonymous targeted the Church of Scientology website for a DDoS attack. The attack was orchestrated as part of a political activism movement against the church called “Project Chanology.” In one week, the Scientology website was hit with as many as 500 DDoS attacks. Some of these were strong enough to even bring the website down. A New Jersey teenager was sentenced to two years’ probation and hefty fines for the crime.
It wasn’t until 2016 that Yahoo announced, while in negotiations for its sale to Verizon, that it had been the victim of a “state-sponsored” attack in 2014. 500 million accounts had been compromised. But it got worse. In December 2016, Yahoo announced another breach that had happened in 2013 compromising 1 billion user accounts. A few months later, Yahoo had to revise its estimates and announce that all 3 billion user accounts had likely been affected, reducing Yahoo’s value by about $350 million.
2014 – JPMorgan Chase
The accounts of 76 million households and 7 million small businesses were compromised in a cyber attack during the summer of 2014. The hackers gained access to names, addresses, phone numbers, and emails of the account holders, but there was no evidence that passwords or Social Security numbers had be retrieved.
2016 – Adult Friend Finder
The names, email addresses, and passwords of over 412.2 million accounts spanning over 20 years were leaked in October 2016. The passwords were only protected by the poor SHA-1 hashing algorithm, which meant most had been exposed by the time the leak was discovered.
2017 – Equifax
The news moves so fast, it can be tough to recall that 143 million user accounts were exposed last year by Equifax. As one of the largest U.S. credit bureaus, the leaked data was incredibly sensitive and valuable – social security numbers, birth dates, addresses, driver’s license numbers, and even some credit card numbers. The breach likely started in mid-May and was discovered in July, though Equifax delayed announcing it publicly until early September. Equifax struggled to explain why it took so long to discover – and report – the breach.
June 27, 2018 – Exactis
This June, according to Wired, 340 million records were leaked by an unknown marketing firm located in Florida: Exactis. That’s more than double the enormous Equifax breach of 2017. Your name, address, phone number, interests, habits, number of children (along with their ages and genders), plus other personal information, such as if you smoke or adhere to a particular religion, was likely part of this leak. How did it happen? An open database accessible to any hacker – not the work of a malicious entity – just poor cyber security.
Who’s Next?
Data breaches happen to businesses every day. Whether it is a reputable education website like Edmodo.com (May 2017 – 77 million user accounts exposed) or a close-knit gaming site like Rune.live (March 2017 – 9,618 user accounts exposed), everyone is at risk. Data is valuable. Passwords, names, emails – personal identify information (PII) can be sold and bought in the darkest corners of the darknet.
It’s up to you to ensure you have security in place, and a disaster recovery plan in case anything goes wrong. Find out what tools are available to protect your business from a cyber attack, be it malware, ransomware, or DDoS. Ensure your systems are monitored daily, and you or a monitoring team are alerted if anything goes awry. Mindsight works daily with clients to do just that.
As the nefarious lion Scar once sang, “Be prepared!”
Contact us today to discuss how to avoid earning a place in the history of cyber attacks.
Like what you read?
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Author
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.