June 15, 2021 by Siobhan Climer, Mishaal Khan, and Jason Wankovsky
This article was originally published in December of 2019.
Ransomware threats have been rising across the globe, and cybercriminals are targeting everyone from multinational enterprise organizations to schools, small towns, and hospitals.
It is estimated that every 14 seconds there is a new ransomware victim, and that the costs of ransomware will exceed $1.85 million per attack in 2021. To protect against these attacks, organizations have started backing up data to the cloud. But does the cloud protect against ransomware?
Are you already operating in the cloud? Our team of experts will run a brief discovery of your current deployments and make recommendations for how to optimize your environment for data protection, security, and cost.
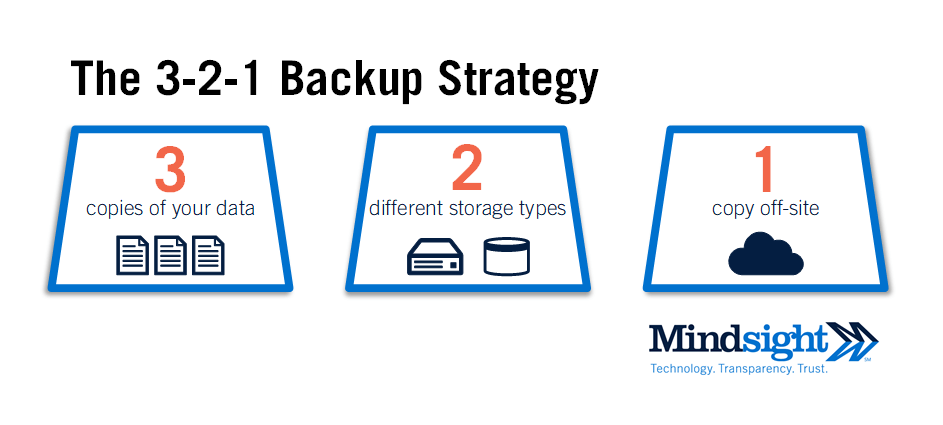
The Basics: A 3-2-1 Backup Strategy
The 3-2-1 backup strategy provides a baseline rule by which companies can protect the data on which they rely.
The 3-2-1 backup strategy states that you should keep:
- At least THREE copies of your data;
- Backed-up data on TWO different storage types;
- At least ONE copy of the data offsite.
Learn more about the 3-2-1 backup strategy. Read about best practices for backup.
Is Cloud A Viable Off-Site Solution?
The uptick in cloud computing means many backup experts have shifted their definition of off-site to equal cloud. And while the cloud is a viable off-site solution, it probably shouldn’t be the only off-site solution.
 Off-site should also include an addendum: offline. The off-site backup should be always accessible. Since the cloud operates via network connectivity, if the cloud isn’t accessible, neither will the off-site backup. Using the cloud as an off-site backup is ideal only when done in consort with a physically accessible off-site – offline – backup.
Off-site should also include an addendum: offline. The off-site backup should be always accessible. Since the cloud operates via network connectivity, if the cloud isn’t accessible, neither will the off-site backup. Using the cloud as an off-site backup is ideal only when done in consort with a physically accessible off-site – offline – backup.
It seems the new backup adage might be 3-2-1-1 – 3 copies, 2 storage types, 1 offsite and 1 offline.
Does Cloud Protect Against Ransomware?
Ransomware works by encrypting a victim’s files and holding them hostage until a bitcoin ransom is paid. And while cloud is an affordable and easy alternative to off-site tape storage, it is not magically protected from ransomware.
One of the biggest benefits of the cloud is actually that which if often the biggest concern with a cloud migration: security. While cloud providers are clearly larger targets, they are also better able to invest in the protections businesses require to defend against aggressive attackers. In 2020 alone, almost 3.1 million external attacks occurred on cloud user accounts. Though these types of attacks hit a high during the second quarter, they remained steady in most countries and increased in some over the third and fourth quarters. The resources of these cloud providers were able to thwart these attacks.
To protect against ransomware in the cloud, businesses must understand the shared responsibility model of cloud computing. Read about how data security in the cloud is a shared responsibility.
Ransomware Can Hit The Cloud
KrebsOnSecurity offered this case study based on the ransomware attack on Children in Film, an advocacy firm for child actors that operated exclusively off of application hosting services with a managed cloud provider. An employee opened an email attachment that appeared to include an invoice – in fact, it was the payload.
“Someone in my office was logged into Outlook and opened up an invoice attachment and BAM!, within 30 minutes every single file on our Q drive had ‘vvv’ added as file extensions,” Children in Film CEO Toni Casala told Brian Krebs.
Children in Film was lucky; the strain of ransomware – TeslaCrypt – had a weakness that security firms were able to exploit, allowing most victims to escape unscathed (i.e. without paying the ransom).
The unnamed cloud provider the firm used did keep backups, but it took a week for the provider to fully restore all of the encrypted files. The attack disrupted operations for other customers on the same server as well.
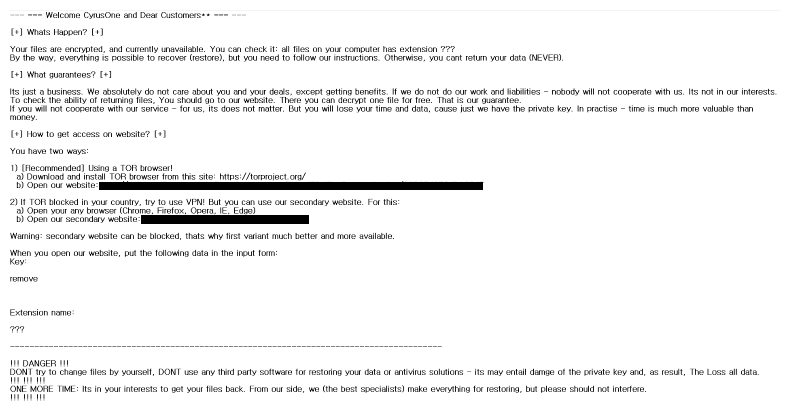
Other companies have not been as lucky. Complete Technology Solutions, a Colorado-based IT service vendor for dental practices, and CyrusOne, a major US data center provider, have both been infected by REvil (Sodinokibi) ransomware in the last week.
This summer, iNSYNQ, a cloud computing provider of virtual desktop environments, was infected with the MegaCortex ransomware strain and suffered an outage that lasted over a week, impacting not only the company’s direct clients, but those who used aspects of its infrastructure.
As the criminals noted in their ransomware alert, “If you will not cooperate with our service – for us, its does matter. But you will lose your time and data, cause just we have the private key. In practice – time is much more valuable than money.”
A Recommended Approach To Cloud For Ransomware Protection
The cloud can work for backups; however, instead of simply backing up your files to the cloud, utilize multiple clouds simultaneously to expand protections and reduce risk – without drastically increasing costs.
A dedicated cybersecurity and disaster recovery strategy is also vital to using the cloud safely and effectively. By understanding your baseline cybersecurity posture, you are better able to identify gaps and minimize threats. If you take the time to identify and categorize your applications, you will have a better sense of RTOs and RPOs, enabling a more targeted disaster recovery strategy.
Our team of experts knows backup and disaster recovery, cybersecurity, and the cloud go hand-in-hand. Talk with our experts in a complimentary one-on-one virtual or in-person whiteboard session to see what we have to offer.
Like what you read?
Contact us today to discuss how the cloud protects against ransomware.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Jason Wankovsky is the Chief Technology Officer and Vice President of Consulting Services at Mindsight, an IT Services and Consulting firm located in the Chicago area. Jason has over 20 years of experience in IT management and executive leadership and is responsible for Mindsight’s technology vision. He is also focused on the creation and delivery of high value managed services for clients across multiple industries. Jason leads the solution architecture team that is responsible for delivering optimal technology services and solutions that enable the businesses of clients.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.
What Is Cloud Storage Part 1: An Overview Of Cloud Computing Basics