March 5, 2019 by Siobhan Climer
“Unless you have discovery done, unless you have an external party look into your security posture, you don’t know what you have, and you don’t know what the threats are … The truth is, you don’t know what you don’t know.”
In a recent interview Mishaal Khan, whose list of cybersecurity qualifications includes Certified Ethical Hacker, CCIE R&S, Security Practitioner, Certified Social Engineer Pentester, and Senior Security Solution Architect, breaks down one of the key issues at the center of information security today: visibility. To protect data and business reputation, organizations need to understand what is happening inside their networks. They need to have cybersecurity visibility into who is accessing data, when they’re accessing data, what data they’re accessing, and how they’re accessing it.
Knowledge is power. The pen is mightier than the sword. The Pentester is mightier than the swordhacker? Eh?
Consider how risk management theory applies to cybersecurity. The number of threats to your business are almost uncountable. Breaches, nation-state attacks, insider attacks, accidental releases, ransomware – the list goes on and on. As Khan says in this same interview:
“Even I cannot help you be absolutely secure. I can get you where you want to be and target your top ten threats, but never say you’re secure. I’m not secure. I’m exposed as well, and I do this for a living. Nobody’s immune.”
Data is your primary asset. Prioritizing these threats and understanding this is central to developing a hardened security framework for today’s cybersecurity landscape. Cybersecurity visibility gives you the insight to know what to protect, how to protect it, and what you need to protect it from.
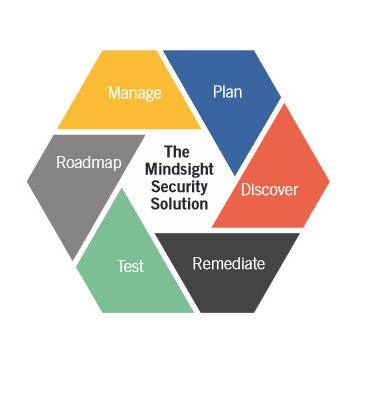
Cybersecurity Visibility Starts With Discovery
Your team has valuable knowledge of your security framework, and they will know the ins and outs from the internal perspective. Unfortunately, this internal perspective is often narrow and overly focused. Just like writers need editors, IT teams need external eyes to perform discovery. Trusted cybersecurity experts have a broader perspective, and their experience with a wide variety of industries and organizations gives them real-time insight into the changing threat landscape.
To have cybersecurity visibility into your network, complete inventory scans and vulnerability assessments are needed. Discover where the gaps are in your security approach, so you can begin to remediate. Begin the discovery process with a whiteboard session, free weekly one-on-one chats with a member of our senior security team. Chat about your biggest concerns, current solutions, and what a roadmap to a more secure future might look like.
Whether business financials and payroll records, or customer contacts and intellectual property, the data your business stores, transfers, and accesses is vital to your success. Finding tools that offer visibility into the movement of data is essential to securing it, and Mindsight’s cybersecurity team can help you identify and find the right solutions for your unique business needs.
Six Links To Security
Discovery is only one step in developing cybersecurity visibility and a hardened framework that deals with the most pertinent threats. Mindsight’s security experts understand the threats to your business. Cybercrime costs are expected to reach $6 trillion by 2021, which is why it is more important than ever to build a resilient security framework that protects your business and the data on which it relies.
We will stand by your side through thick and thin, 24x7x365 because we know no one can do it all. We’re not here for sometimes, we’re here for always. You can count on us to be there if – and when – you need security experts.
Cybersecurity Visibility: Who’s Taking What Where?
Once you have visibility into your network, you will be able to see how the data is moving and who is moving it. Today’s threats come from both outside and inside the network. By prioritizing data security with a security roadmap, you can start to develop remediation for the most significant threats. Are insiders accessing more data than they should? Are attackers penetrating your DNA layer? Are phishing attacks sneaking past your email filters and enticing unwary eyes? These threats are real. Only once you have cybersecurity visibility can you begin to identify the most relevant threats to your business. Then you can remediate, test, roadmap, and manage for the future.
Protect your data and your business today. Work with Mindsight’s trusted security team to secure your network for the threats of today and those of tomorrow.
Contact us today to discuss your cybersecurity framework.
Like what you read?
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Author
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.
Blockchain For SMBs: Does It Belong In Your Security Posture?