March 10, 2023
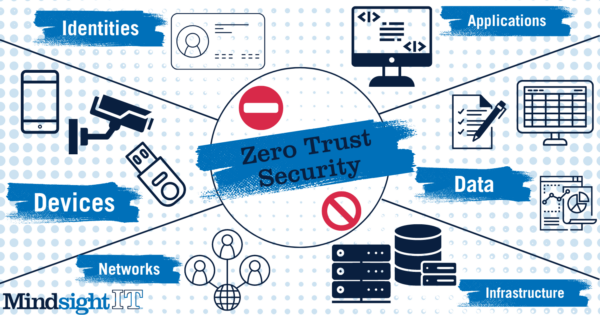
Going through life trusting nothing and no one is a miserable way to exist. But when it comes to cyber security, so-called Zero Trust is the only way to roll. Not surprisingly, its popularity is exploding.
Like the best journalism, Zero Trust — a market that’s expected to hit nearly $52 billion by 2026 — is rooted in an ethos of “never trust, always verify.” That means all access requests, including the most common ones, must be verified before they’re granted. It’s a continuous process that never lets up. Firewalls and antivirus software used to suffice. They don’t anymore. Centralized monitoring and analytics is where it’s at.
“Most of us conduct business remotely using mobile devices,” wrote Alper Kerman, a security engineer at the National Institute of Standards and Technology (NIST). “We consume, exchange, and store digital information in private clouds, public clouds, hybrid clouds, and many other variations in between. Needless to say, the conventional boundaries have expanded and become more obscured, allowing for a much larger footprint of applications and services to be located and accessed from anywhere. Of course, with that expansion, cybersecurity vulnerabilities have also grown. We now have more areas and points of attack. And we are especially vulnerable to the types of cybersecurity breaches that originate from inside the networks — inside the perimeter.”
The ongoing verification at the core of Zero Trust employs a variety of authentication and authorization protocols. They include multi-factor authentication (MFA), single sign-on (SSO), and identity and access management (IAM). The goal is simple: to make sure that only authorized users get insider access.
Here’s a good way to think about it: Despite your graying hair and increasingly noticeable wrinkles, a certain liquor store clerk always insists on seeing your I.D. Whether you find that annoying or flattering is beside the point; the policy is in place to mitigate the store’s risk. And if it works just once, perhaps preventing that business from being fined or shut down for selling booze to a minor disguised as a geezer — the safeguard has proved its value.
It’s the same for any business that relies on the internet for commerce and communication — which is nearly all of them these days. From malware and phishing attacks to password attacks and elaborate social engineering schemes, cyberspace is rife with potential pitfalls and bad actors. It’s far better, then, to be safe than sorry. That’s why the Zero Trust model is becoming increasingly popular with organizations of all types and sizes, especially in the era of remote work.
“With all the latest technology at our fingertips, we have the responsibility to do our due diligence today. Hackers don’t wait for budget approvals.” Mishaal Khan
Whereas Virtual Private Networks (VPNs) used to be a standard requirement for off-site employees, ZTNA (zero trust network access) is now becoming the norm. It’s a more sophisticated and effective form of perimeter protection.
Here’s a good nutshell explanation of ZTNA from Gartner: “Zero trust network access abstracts and centralizes access mechanisms so that security engineers and staff can be responsible for them. It grants appropriate access based on the identity of the humans and their devices, plus other contexts such as time and date, geolocation, historical usage patterns, and device posture. The result is a more secure and resilient environment, with improved flexibility and better monitoring.”
Another concept central to the Zero Trust model is something called “limiting the blast radius.” Think of cyber attacks as physical bombs, and you’ve got the idea. It’s all about minimizing the impact of a breach. Because here’s the thing: Even the best Zero Trust safeguards aren’t foolproof.
According to Microsoft, which recently published an e-book titled “Examining Zero Trust: A Roundtable Discussion,” there are seven major Zero Trust adoption strategies that organizations should follow.
- Use identities to control access
- Elevate authentication methods
- Incorporate passwordless authentication
- Segment your corporate network to help prevent lateral attacks
- Secure all business and personal devices, including computers, tablets, and phones
- Segment your applications to improve the balance between access and control
- Define roles and access controls to avoid the proliferation of old accounts that aren’t updated — and are, therefore, more vulnerable to attacks.
“Whether we call it Zero Trust or another new buzz word, we cannot allow ourselves to wait for the next breach, we must implement security measures at every layer of access. Only then we can say we did our best.” – Mishaal Khan
About The Expert
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.