July 28, 2020 by Siobhan Climer and Mishaal Khan
It’s not a secret. The sheer number of data breaches occurring today is enough to make a CISO quake.
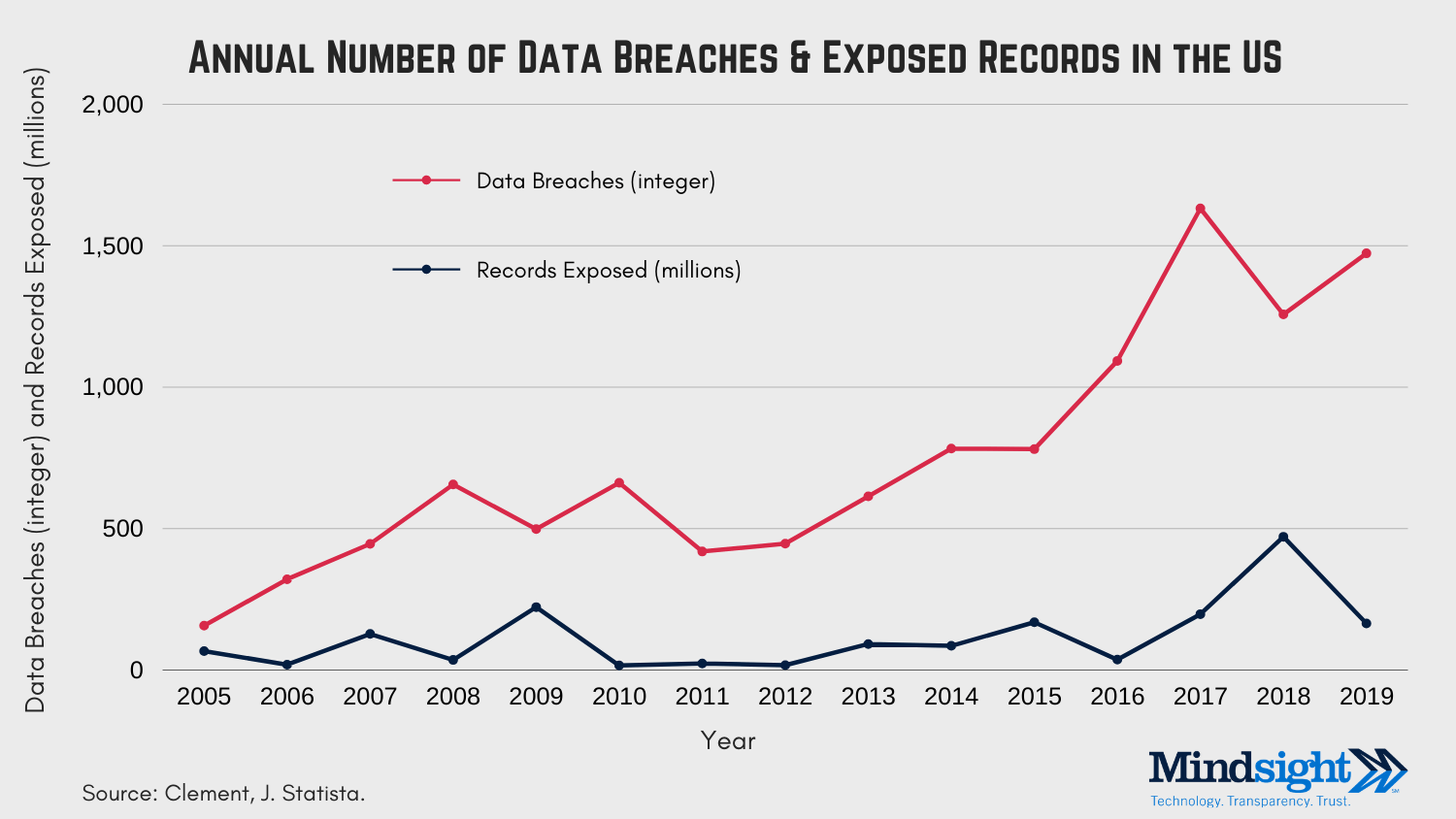
In 2005, there were 157 (reported) data breaches in the U.S. A decade later, in 2015, that number had reached 781. Last year, businesses in the U.S. reported 1,473 data breaches.
And that number shows no sign of slowing down.
It’s also important to note that this number only represents reported breaches.
In all likelihood, the actual numbers are far higher. This data also reflects the delays that happen between incident and report. For example, the largest data breach on record (Yahoo) occurred in 2013 but only came to light in 2016.
While these discrepancies leave many questions for analysts and researchers, they provide context for CISOs and business leaders responsible for managing risk and protecting business assets.
Can Business Leaders Prevent A Data Breach?
In short, no.
 This answer might surprise you given the title of this article is “How To Prevent A Data Breach”, but the reality is that cyber criminals are often one step ahead of security professionals, hard at work exploiting zero day vulnerabilities, security gaps, or lazy security postures.
This answer might surprise you given the title of this article is “How To Prevent A Data Breach”, but the reality is that cyber criminals are often one step ahead of security professionals, hard at work exploiting zero day vulnerabilities, security gaps, or lazy security postures.
They are motivated, talented, and – frequently – quite stubborn.
While you can never be 100% secure, or have 100% confidence your network and data are safe, you can take steps to mitigate the risk of a data breach.
Here are some of the fundamental steps you can take to prevent a data breach or at least mitigate the impacts of one should it come your way.
How To Prevent A Data Breach
Since we have established there is no way to completely prevent a data breach, let’s discuss what data breach risk mitigation might entail.
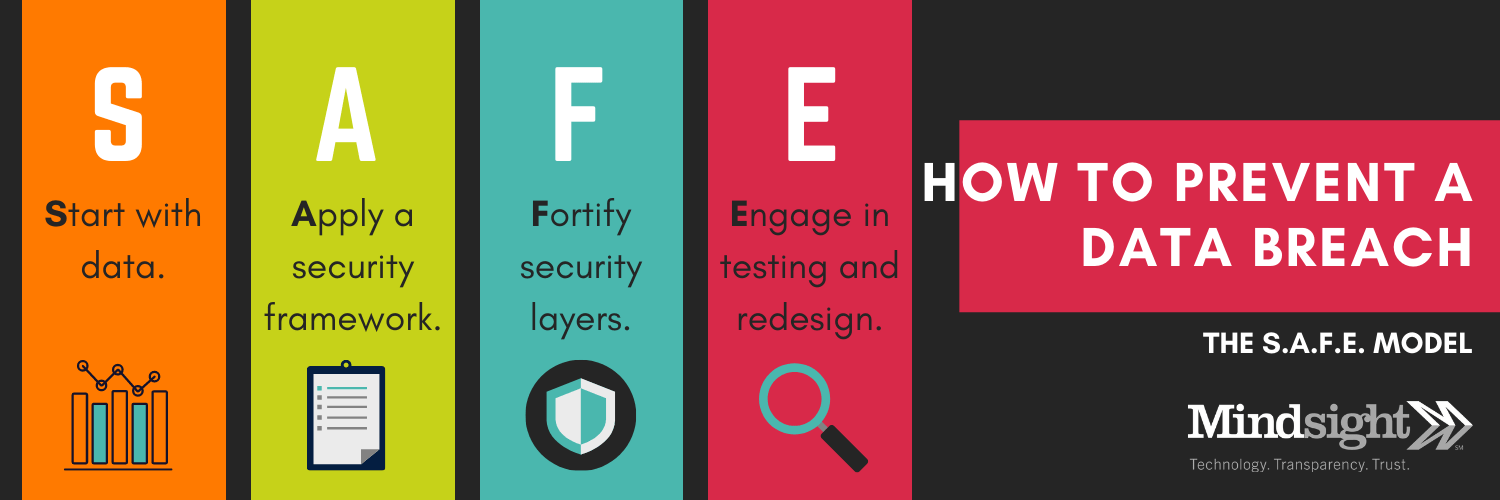
The S.A.F.E. model provides a foundational approach to data protection and breach prevention.
- Start With Data
- Apply a Security Framework
- Fortify Security Layers and Seal Gaps
- Engage in Testing and Redesign
Step 1: Start With Data
“You don’t know what you don’t know.”
People’s biases and gut instincts are prone to leading them astray. This is just as true with cybersecurity as it is with most decisions. You may believe your email security is superb – but do you know?
“It’s absolutely critical that technology leaders undertake a thorough security risk assessment to identify security weaknesses before they can be exploited,” writes Brian Olearczyk in a recent Businesss to Community article.
Security risk assessments give you visibility into your current security posture, its strengths and weaknesses, and the data you need to craft a proactive security roadmap.

Step 2: Apply A Security Framework
Many business leaders forget that building a security posture for their organization is not a lonely mountain path only they can journey. This is a reality every business in every industry is reckoning with today.
That means that there are others solving the exact challenges you face.
Don’t reinvent the wheel. Instead, utilize the security frameworks developed by agnostic regulatory and advisory organizations like the Center for Internet Security (CIS) and the National Institute for Standards and Technology (NIST).
With an entire Computer Security Resource Center, NIST provides a framework within which to strategically strengthen your security posture.
Don’t guess. Get help. You deserve a security team who has your back.
Contact Mishaal Khan, Mindsight’s Senior Security Solutions Architect, to start building a security posture today.
Strengthen Your Security Posture: Start With A Cybersecurity Framework
Step 3: Fortify Security Layers and Seal Gaps
This is the activation step.
In the first two steps, you gathered data and created a strategic security plan within a designated framework.
Now, it’s time to put the pedal to the metal.
Using a security framework, begin remediation by deploying security tools and policies to address your unique security vulnerabilities and gaps. For some businesses, this may include securing edge computing networks or cloud-based applications.
For others, it might mean shredding the post-its scribbled with passwords.

Start with steps – or security controls – that make sense for you. That’s the benefit of using a security framework – it helps meet your organization where it is and remove vulnerabilities one at a time.
It can’t go without saying the importance of user awareness training when it comes to sealing vulnerabilities in your security posture. Humans are the number one threat to an organizations’ data.
Employ a trusted security advisor in assisting with a security awareness training program. A poorly-constructed program is a waste of money. In the infamous 2004 “Carronade” West Point case, cadets underwent a 4-hour user awareness training.
90% of the cadets went on to click a test phishing link.
User awareness training must go beyond a lecture or one-day workshop. It’s a continuous cycle. And, as an IT leader, you must also recognize that some users are always going to click the link. Alas.
That’s why security layers are so vital when you want to prevent a data breach.
Step 4: Engage In Testing And Redesign
Accepting failure is hard.
As a CISO and IT leader, you have to be prepared to see a security posture fail. Hopefully, that failure is at a point where you can remediate and rectify – before a data breach occurs.
That’s why testing is essential; yet many businesses fail to take this simple step.
Did your remediation controls work? Are multifactor authentication (MFA) and stronger network access controls (NAC) effective? Without testing, you are no better off than when you started.
Visibility is key. Find out if your investment is having the desired impact.

Prevent A Data Breach From Taking You Down
Data breaches can be disastrous. Many businesses, especially small and mid-sized ones, never recover.
Employ the S.A.F.E. model today to help prevent a data breach from impacting you and the data you strive to protect.
See what we can do for you. Contact us today.
Like what you read?
About Mindsight
Mindsight is industry recognized for delivering secure IT solutions and thought leadership that address your infrastructure and communications needs. Our engineers are expert level only – and they’re known as the most respected and valued engineering team based in Chicago, serving emerging to enterprise organizations around the globe. That’s why clients trust Mindsight as an extension of their IT team.
Visit us at http://www.gomindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer writes about technology trends in education, healthcare, and business. With over a decade of experience communicating complex concepts around everything from cybersecurity to neuroscience, Siobhan is an expert at breaking down technical and scientific principles so that everyone takes away valuable insights. When she’s not writing tech, she’s reading and writing fantasy, hiking, and exploring the world with her twin daughters. Find her on twitter @techtalksio.