February 13, 2020 by Siobhan Climer and Mishaal Khan
Scammers have been around since long before the advent of computing. From the infamous Gregor MacGregor, who invented a fictitious Central American country (of which he was, of course, Crown Prince) to the masquerading Pretorian Guard of the Roman empire, who successfully conned (then assassinated) the unfortunate Emperor Julianus, fraud is nothing new.
Whether for financial gain, power, fame, or information, scammers are always on the look-out for a new mark. Interestingly, their methods have changed little, which is why phishing remains one of the most common methods cybercriminals use to gain information.
Here are four of the most common real-life phishing scams netting victims today.

Most Common Real-Life Phishing Scams
#1: CEO Fraud / Email Account Compromise / The Gift Card Scam
According to a recent FBI report, U.S. victims of business email compromise (BEC) scamming have lost a collective $2.9 billion. In this incredibly common scam, cybercriminals spoof an executive account – typically the CEO or CFO – and request an employee complete a wire transfer or purchase gift cards for a new “incentive” program or as a personal favor.
Check out the phishing examples below:
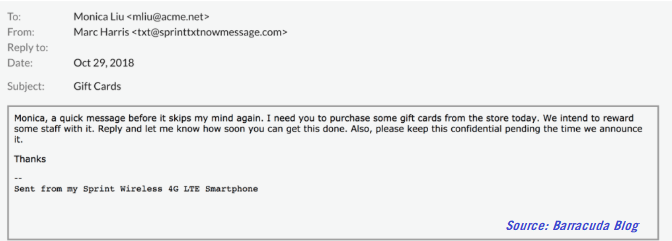
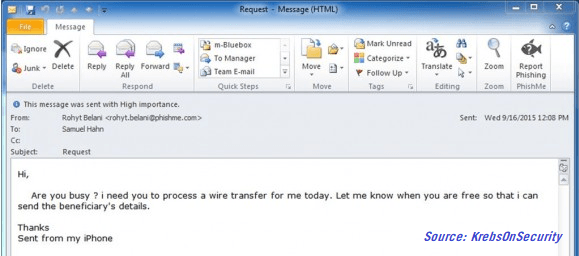
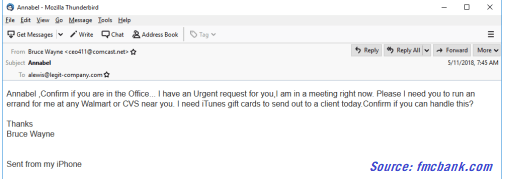
These phishing scams play on employee’s sense of duty and urgency. The scammers write “I have an urgent request” and “confirm if you can handle this” – and it works.
In the FBI report, they report that between 2016 and 2018 there was a 136% increase in identified losses tied to BEC phishing. Although this common real-life phishing scam has targeted every industry, schools, local governments, and real estate have been particularly impacted by this attack.
#2: Look-Alike Login Pages
As users have become more conscious of these threats, cyber criminals have adjusted and refined their practices. Take a look at the website screenshot below:
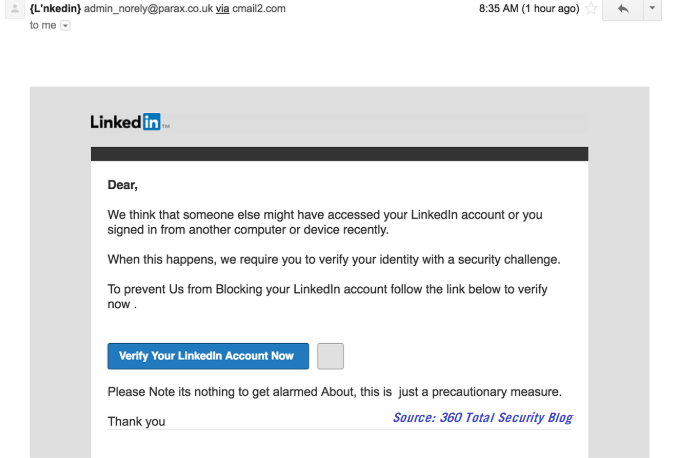
Although this phishing email is poorly composed (note the originating account and erroneous capitalization), it works.
Why? A rushed employee skimming email might not even read the email contents, instead recognizing the LinkedIn logo at the top of the email and the brand-colored button in the email.
Clicking on the ‘Verify Your LinkedIn Account Now’ button would bring you to a page that looks like a legitimate LinkedIn login page. The user enters their account information, receives an ‘Account Confirmed’ notification, and then continues on with their business – failing to realize they were just phished.
This phishing scam is particularly dangerous because users may leak access credentials without realizing it, enabling cyber criminals to have essentially unlimited access to the account.
#3: Tech Support Scams
It’s not uncommon for the average user to express a lack of confidence in technical matters, and cyber criminals take advantage of that in this next common phishing scam.
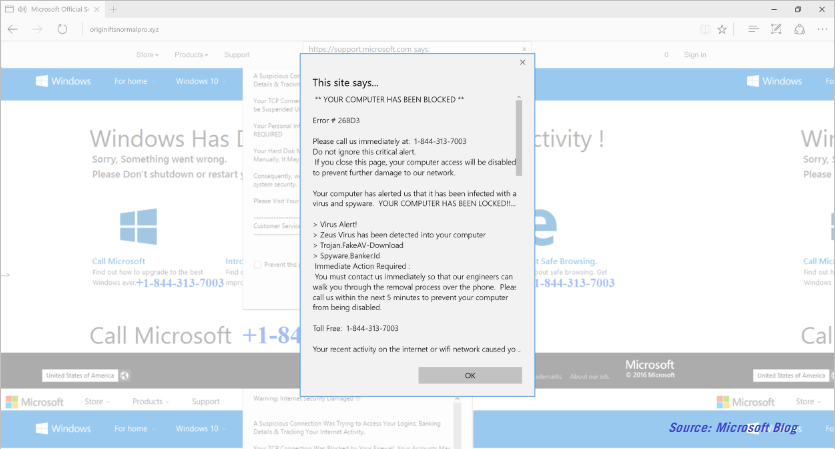
In a tech support scam, cyber criminals utilize repetitive pop-up messages, full screen functionality, and dialog box loop cycles to perpetuate the deception that something is wrong with the users PC.
In addition, scammers take on the persona of behemoth tech giants – like Microsoft, Apple, and Google – to add legitimacy to the scam.
In the example below, documented thoroughly on the Microsoft blog, cyber criminals convince users to call a toll-free number and then talk them into purchasing anti-virus software they don’t need.
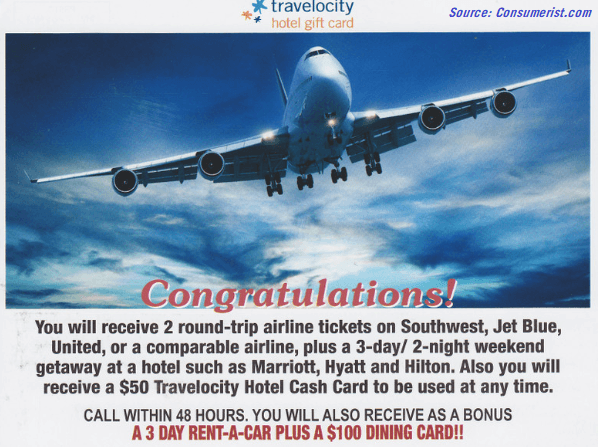
#4: “Amazing Opportunity”
Whether it’s a Nigerian prince offering an incredible investment opportunity or a work-from-home job stuffing envelopes that promises thousands a week, skepticism is a vital tool in the anti-phishing toolbox.
If an opportunity seems too good to be true, it probably is.
Security Services company ADT reported that in 2018 Americans lost over $700,000 to the ‘Nigerian Prince’ email scam and millions more in more sophisticated get-rich-quick schemes.
In these cases, cyber criminals are taking advantage of user’s desires – for financial gain, free vacations, lucky happenstance, or a change of pace. Pyramid schemes and ponzi schemes both fall under this category.
Social media has only exacerbated the issue. In one recent example, WhatsApp users have fallen victim to the ‘Loom Circle’ scam. The scam targets younger victims and promises a return of £1280 from a £160 investment.

How To Protect Your Users From The Most Common Phishing Scams
Humans are notoriously the weakest element of security. People are gullible, trusting, and curious – and it is precisely these qualities criminals rely on to make millions.
There are ways for businesses to protect their investments and put controls in place to prevent the penetration of the network – even if a phishing scam is successful in targeting an employee.
Some first steps to hardening your security posture include:
- Security Awareness Training
- Simulated Phishing Campaigns
- Multi-Factor Authentication
- Email Filtering
- Perimeter Controls (Firewalls/DNS Filtering)
- Endpoint Protection
- Enhanced Access Management
To better protect your users and your business, talk with our security experts today. Mindsight’s team of pentesters and ethical hackers understand how cyber criminals think and act, and they can help you harden your security posture to protect your business, its data, and the resources you rely on.
Like what you read?
Contact us today to discuss the most common real-life phishing scams and what you can do to protect yourself.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.

