September 12, 2019 by Siobhan Climer and Mishaal Khan
Data breaches are unnervingly common. In 2018, there were over 1,200 reported data breaches with over 196.7 million sensitive records exposed. 2019 isn’t fairing much better. In fact, according to Forbes, the first six months of 2019 have already seen 4.1 billion records exposed!
While the big name breaches of 2019 are certainly captivating – think Fortnite, Facebook, Canva, and Capital One – the fact is that “the majority of breaches reported this year had a moderate to low severity score”, exposing 10,000 or fewer records.
Why Are Small And Mid-Market Organizations At Risk?
Smaller organizations without a global or nationwide footprint are more likely to downplay their risk of attack because of their size. Unfortunately, this couldn’t be further from the truth.
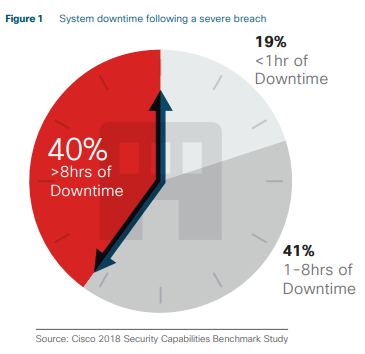 Small businesses typically have fewer security controls in place, making them a prime target for malicious hackers. Almost every business – big or small – conducts online business, and that online presence is considered low-hanging fruit by cybercriminals.
Small businesses typically have fewer security controls in place, making them a prime target for malicious hackers. Almost every business – big or small – conducts online business, and that online presence is considered low-hanging fruit by cybercriminals.
In fact, according to a recent Cisco report, Small and Mighty: How Small and Midmarket Business Can Fortify Their Defense Against Today’s Threats, more than half of midmarket companies suffered a security breach in 2018. It is important to qualify that number with the following phrase: of which they are aware.
Why? According to IBM’s annual Cost Of A Data Breach report, the average time taken to identify a data breach has risen to 279 days – and includes both identification and containment. That means that many businesses deny having suffered a breach when they simply haven’t discovered the breach yet.
How To NOT Be A Target For Cybercriminals
Mishaal Khan, Mindsight Senior Security Solutions Architect, has this to say about building your security posture:
“I always tell people you can never secure yourself 100% from anything. Even I cannot help you be 100% secure or 100% private. It’s a layered approach. You have to pick and choose your battles. You have to pick and choose what threats are relevant to you. What are you trying to protect?”
While you can never be 100% secure, there are steps you can take to minimize the likelihood of an attack and mitigate overall risk.
1. Make Data Security A Priority
The unfortunate reality is that information security has long been seen as an unwarranted cost. In the past, it was easy for boards and leadership to formulate numerous fallacies to delay security investment.
We won’t be a target.
Our data isn’t important enough.
We already use firewalls and access logs.
Security doesn’t deliver ROI.
All are definitively untrue. Everyone is a target; data is data, and data is valuable – very valuable; you are not – and will never be – 100% secure, and security controls directly impact the quality you deliver and the perception of your brand by customers.
Use this information to support conversations with leadership and demonstrate value. Send them the reports linked above. Don’t let security fall to the wayside simply because the returns aren’t immediately visible.
2. Use Process-Driven Solutions
 Gaps are how malicious hackers get in. Whether they exploit a backdoor or a chatty administrator, cybercriminals find holes and get in. That is why it is essential to use process-driven problem-solving. You could layer on security control after security control and still fall victim to a smart cybercriminal who uses your gate as a ladder.
Gaps are how malicious hackers get in. Whether they exploit a backdoor or a chatty administrator, cybercriminals find holes and get in. That is why it is essential to use process-driven problem-solving. You could layer on security control after security control and still fall victim to a smart cybercriminal who uses your gate as a ladder.
By ensuring a strategic process-driven analysis that involves discovery, planning, remediation, testing, roadmapping, and continued management, you cover the various aspects of your posture and protect it.
While these interlinked steps are all important, testing is critical. Bring in experts to test your defenses, infiltrate your system, and then share those insights with you to further harden your security posture.
3. Find Security Experts Outside Your Four Walls
It’s tempting when you’re talking about security – and, ergo, trust – to want the experts you rely on to work exclusively within your organization. But there are two reasons you should be wary of an internal-only security team.
 The first is that attacks by insiders make up a large portion of data breaches. The 2018 Insider Threat Report found that 90% of organizations feel vulnerable to insider attacks, and 53% report confirmed insider attacks against their organization in 2018. The reality is that your internal team cannot be trusted simply because they are internal.
The first is that attacks by insiders make up a large portion of data breaches. The 2018 Insider Threat Report found that 90% of organizations feel vulnerable to insider attacks, and 53% report confirmed insider attacks against their organization in 2018. The reality is that your internal team cannot be trusted simply because they are internal.
The other reason to look beyond an internal-only team is that security professionals relegated to these teams tend to lose overall market perspective. What are the latest attack methodologies? How have other mid-market healthcare clinics dealt with PHI protection?
External experts bring this broader perspective, and this only gives your organization more information and data with which to build a security posture you trust.
Mitigate Risk With Security Expertise
“Hackers are always ahead of us,” says Khan. By developing security awareness and investing in information security, your team can deter threat actors from targeting your organization.
Mitigate your risk by bringing in a team of security experts that understands the different perspectives – from ethical hacking to security frameworks – and build out a security posture that protects your organization and the data on which it relies.
Sign up for a discovery session with our team today.
Like what you read?
Contact us today to discuss how to not be a target for cybercriminals.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters. Find her on twitter @techtalksio.


