May 18, 2021 by Siobhan Climer, Mishaal Khan, and Jason Wankovsky
This article was originally published in December of 2019.
So far in 2021, ransomware attacks have increased 102% compared to the same period in 2020, and the impact of these attacks continues to grow. Every industry – from healthcare to manufacturing, from towns and cities to banks and financial instiutions– has been affected. Particularly, healthcare and utilities have been targets (CaptureRX and Colonial Pipeline to name a few).
Sadly German authorities reported a ransomware attack in December of 2020 caused the failure of IT systems at a major hospital in Duesseldorf, and a woman who needed urgent admission died after she had to be taken to another city for treatment.
In November of 2019, KrebsOnSecurity reported 110 nursing homes and acute care facilities were unable to access patient health records after Wisconsin-based IT vendor – Virtual Care Provider Inc. (VCPI) – suffered a Ryuk ransomware attack.
What Is Ransomware?
Most in the tech industry are aware of ransomware, its prevalence and pervasiveness. Cybercriminals hack into an operations’ systems, encrypt files, and demand a ransom in exchange for a decryption key. In the case of VCPI, the criminals demand $14 million in bitcoin to decrypt the patient records.
 VCPI can’t afford the ransom. Even with a disaster recovery plan, VCPI is finding itself in a situation no one wants to be in. Karen Christianson, CEO of VCPI told Brian Krebs that, among other things, they’re primarily “dealing with getting electronic medical records back up and life-threatening situations handled first.”
VCPI can’t afford the ransom. Even with a disaster recovery plan, VCPI is finding itself in a situation no one wants to be in. Karen Christianson, CEO of VCPI told Brian Krebs that, among other things, they’re primarily “dealing with getting electronic medical records back up and life-threatening situations handled first.”
From drug orders and deliveries to Medicaid billing, the impact of this particular attack could easily put VCPI and its many clients out of business as soon as December 5th – while also impacting the lives of the most vulnerable.
This alarming example of how ransomware – and to a broader extent, cybersecurity – is intertwined with a strategic backup and disaster recovery program illustrates how vital it is to invest in both practices.
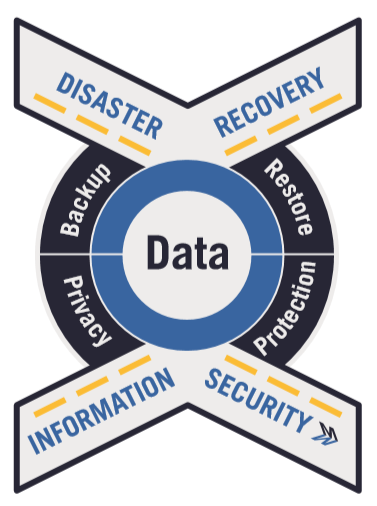
The Crossroads of Data Protection
In the white paper The Crossroads of Data Protection: Disaster Recovery and Cybersecurity, Mindsight CTO Jason Wankovsky and CISO Mishaal Khan lay out the fundamental differences between cybersecurity and disaster recovery – and how these two entities intersect at the point of data protection.
During their research, Wankovsky and Khan showed how the vital elements of both disaster recovery and information security – specifically backup, restore, protection, and privacy – all focus on the fundamental worldwide currency: data.
Why Cybersecurity Isn’t Enough
 Many see the victims of ransomware as examples of failed cybersecurity practices. In reality no one is ever entirely safe from cybercrime – not even the most resolute off-the-grid hacker.
Many see the victims of ransomware as examples of failed cybersecurity practices. In reality no one is ever entirely safe from cybercrime – not even the most resolute off-the-grid hacker.
Cybersecurity practices aim to deter threat actors who seek to hold your data ransom. A smart business will invest in vulnerability assessments and penetration testing, firewalls and multi-factor authentication, identity access management and SIEM/SOC – and resolve attacks through incident response and digital forensics.
But even that isn’t enough. Cybercriminals are often one step ahead, and if determined, they will exploit any vulnerability or gap in your security posture – even ones that have yet to be discovered.
Disaster Recovery And Ransomware
That is why it is so important that organizations prepare ahead of time for threats like ransomware. Disaster recovery programs provide continuous verification and feedback cycles that ensure that your data is backed up and restorable.  That way, in the event your data is encrypted and held ransom, you are not subject to paying a ransom and hoping for the best. By investing in disaster recovery, you are investing in control.
That way, in the event your data is encrypted and held ransom, you are not subject to paying a ransom and hoping for the best. By investing in disaster recovery, you are investing in control.
Only businesses that invest in a hardened security posture, replete with cybersecurity frameworks like NIST or the CIS20, as well as a validated disaster recovery program that tests and restores data backups from off-site (and, preferably, offline) locations are adequately prepared for a ransomware attack.
The Future Of Ransomware
 The rise in ransomware is threatening an increasing number of organizations, from small businesses to the enterprise. Organizations that take these threats seriously and begin the process of hardening security controls and creating and testing a disaster recovery program will be better able to withstand the ransomware storm that is only expected to get worse.
The rise in ransomware is threatening an increasing number of organizations, from small businesses to the enterprise. Organizations that take these threats seriously and begin the process of hardening security controls and creating and testing a disaster recovery program will be better able to withstand the ransomware storm that is only expected to get worse.
Investing in cybersecurity and disaster recovery is not something taken lightly. That’s why Mindsight’s expert-level-only engineers offer weekly whiteboard sessions – complimentary one-on-one virtual or in-person discussions over your most prevalent threats and our advisory actions. Take the opportunity to vet our services and people – we know you won’t be disappointed.
Like what you read?
Contact us today to discuss disaster recovery and ransomware threats.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Jason Wankovsky is the Chief Technology Officer and Vice President of Consulting Services at Mindsight, an IT Services and Consulting firm located in the Chicago area. Jason has over 20 years of experience in IT management and executive leadership and is responsible for Mindsight’s technology vision. He is also focused on the creation and delivery of high value managed services for clients across multiple industries. Jason leads the solution architecture team that is responsible for delivering optimal technology services and solutions that enable the businesses of clients.
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s reading and writing fantasy, gardening, and exploring the world with her twin daughters.