May 21, 2019 by Siobhan Climer and Mishaal Khan
Increases in cyber attacks around the world have led to a greater focus on developing robust cybersecurity policies. According to the recently released Verizon 2019 Data Breach Investigations Report, financially-motivated attacks are increasing, with hackers using ransomware focused specifically on easy targets. Web application attacks are now 13 times more likely to occur, which is concerning given the increase in web application tools used by manufacturing, healthcare, finance, education, and other commonly targeted industries.
While creating a security posture is a vital first step in responding to these increased risks, many organizations fail to continuously update their security policy with feedback. This failure leads to increased vulnerabilities. Feeding security with insights gathered during regular security assessments and red-teaming is an intrinsic part of managing the changing cybersecurity landscape.
Creating Your Initial Security Posture
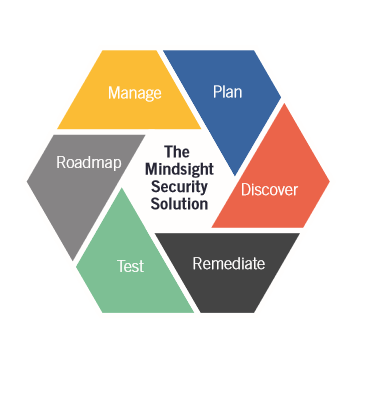 Here is an overview of how organizations can create a robust security posture. We hesitate to use the word “steps” or “cycle” because the different elements of your security posture interact together, continuously.
Here is an overview of how organizations can create a robust security posture. We hesitate to use the word “steps” or “cycle” because the different elements of your security posture interact together, continuously.
- Establish the business objectives
- Identify risk priorities
- Capture historical information
- Workshop solutions
Doing this, security experts can develop a preliminary assessment, complete with the first actions – or low-hanging fruit – the organization can take to begin securing the business.
Feeding Security With Insights
The only constant is change, so says ancient Greek philosopher Heraclitus. This philosophy holds true in technology, where change happens every day. For hackers and malicious entities, change equals opportunity. An OS update, a newly-released video game, M&A activity – all of these changes provide an opening for hackers to gather intelligence, manipulate individuals, and infiltrate organizations with gaps in their security defenses.
This is why it is so important for businesses to monitor, test, remediate, and manage their security posture. Feeding security comes down to identifying gaps, using those insights to improve security, and testing those implementations for new vulnerabilities – all the time.
To begin gathering insights, one of the first steps we recommend organizations take is with DNS filtering. Register today for a free trial of Cisco Umbrella and get access to Mindsight’s security experts and a data-rich dashboard providing you immediate insight into the current risks you’re facing.
Email us at [email protected] with any questions.
Set It And Forget It Doesn’t Work
A single misconfiguration can leave the business – and the data is relies on – at risk. As technology changes, so do the vulnerabilities. Engaging security experts who ensure that you’re feeding security with insights, continually, is the only way to stay ahead of malicious entities.
Any security firm that guarantees you complete, fail-proof security is lying to you. It’s impossible to be 100% secure. Only by prioritizing risks, managing vulnerabilities, and diving into the hard of work of continuously feeding security can you ensure you are deterring attackers and mitigating threats.
The Experts Come To You
While we host regular events to share the newest security insights, we recognize you may not be able to come. That is why we offer free weekly whiteboard sessions. Our security experts take their knowledge on the road, offering live demonstrations on the most prevalent hacks and tutorials on how to mesh cybersecurity frameworks (i.e. NIST and CIS20) with your current environment. Register for one of our upcoming whiteboard sessions and ensure you are feeding security in your organization.
Like what you read?
Contact us today to discuss feeding security in your organization.
About Mindsight
Mindsight, a Chicago IT services provider, is an extension of your team. Our culture is built on transparency and trust, and our team is made up of extraordinary people – the kinds of people you would hire. We have one of the largest expert-level engineering teams delivering the full spectrum of IT services and solutions, from cloud to infrastructure, collaboration to contact center. Our highly-certified engineers and process-oriented excellence have certainly been key to our success. But what really sets us apart is our straightforward and honest approach to every conversation, whether it is for an emerging business or global enterprise. Our customers rely on our thought leadership, responsiveness, and dedication to solving their toughest technology challenges.
Contact us at GoMindsight.com.
About The Authors
Siobhan Climer, Science and Technology Writer for Mindsight, writes about technology trends in education, healthcare, and business. She previously taught STEM programs in elementary classrooms and museums, and writes extensively about cybersecurity, disaster recovery, cloud services, backups, data storage, network infrastructure, and the contact center. When she’s not writing tech, she’s writing fantasy, gardening, and exploring the world with her twin two-year old daughters. Find her on twitter @techtalksio.
Mishaal Khan, Mindsight’s Security Solutions Architect, has been breaking and – thankfully – rebuilding computers for as long as he can remember. As a Certified Ethical Hacker (CEH), CCIE R&S, Security Practitioner, and Certified Social Engineer Pentester, Khan offers insight into the often murky world of cybersecurity. Khan brings a multinational perspective to the business security posture, and he has consulted with SMBs, schools, government institutions, and global enterprises, seeking to spread awareness in security, privacy, and open source intelligence.
Strengthen Your Security Posture: Start With A Cybersecurity Framework


